Infrastructure-as-Code (IaC) has revolutionized infrastructure management by enabling teams to define and automate resource provisioning through code. This ensures consistency, scalability, and version control, which is essential in modern cloud environments.
GitHub Actions has become a go-to CI/CD tool, allowing teams to automate tasks like testing, building, and deploying directly within GitHub. It provides flexibility through YAML-defined workflows, but for large-scale IaC, it lacks critical features such as drift detection, policy enforcement, and robust visibility into infrastructure changes.
For example, a senior engineer at a growing company automated the deployment of containerized applications across multiple environments using GitHub Actions. With automated workflows, they reduced manual overhead in testing and deployments. However, as the infrastructure grew, the need for better governance and compliance became clear. GitHub Actions alone didn’t address drift detection or policy enforcement, which are crucial for maintaining reliable and secure environments. This is where Firefly complements GitHub Actions. Firefly adds the necessary automation and governance features, like drift detection, policy enforcement, and centralized logging, allowing teams to manage IaC at scale without compromising security or compliance.
This blog breaks down how GitHub Actions workflows are typically used for IaC, where they fall short in production environments, and how Firefly complements them with features like policy guardrails, drift detection, and centralized infrastructure visibility. We'll also walk through real-world examples of integrating Firefly into GitHub Actions pipelines to automate and govern infrastructure more effectively.
What Are GitHub Action Workflows?
GitHub Actions is a CI/CD platform that lets you automate workflows directly from your GitHub repository. It’s become a popular choice for infrastructure automation because it integrates tightly with Git-based workflows, supports event-driven triggers, and is easy to customize through YAML files.
In the context of Infrastructure-as-Code (IaC), GitHub Actions is often used to automate tasks like running terraform plan on pull requests or applying changes to different environments after merges. Understanding the core components of a GitHub Actions workflow is key to using it effectively in IaC pipelines.
Core Components of GitHub Workflows
- Events: Events are triggers that kick off a workflow. They can respond to things like a code push, pull request update, or a scheduled job. For example:
- push: Runs the workflow when code is pushed to a branch.
- pull_request: Triggers when a PR is opened or updated.
- schedule: Uses cron syntax to run workflows periodically (e.g., nightly Terraform drift checks).
- workflow_dispatch: Allows manual triggering from the GitHub UI.
- Jobs: A workflow is made up of one or more jobs. Each job runs in isolation, typically on a GitHub-hosted runner like an Ubuntu VM. Jobs can run in parallel or sequentially depending on dependencies. Example: A Terraform job might run a plan, while another job handles linting or policy checks.
- Steps: Steps are individual commands inside a job, like running a shell script, installing a tool, or invoking an action. Steps are executed in order. Many open-source actions exist for common tasks like setting up Terraform or posting comments to PRs.
- Runners: Runners are the actual machines that execute your jobs. GitHub provides hosted runners (Linux, macOS, Windows), but you can also bring your own self-hosted runners if you need more control over the runtime, for example, to access private cloud networks or persistent state.
Common IaC Use Cases in GitHub Actions
Here are some typical use cases for GitHub Actions in IaC pipelines:
- Terraform Plan and Apply: Automate terraform plan on every pull request to preview changes, and run terraform apply post-merge to update cloud environments.
- Validation and Linting: Run terraform validate, tflint, checkov, or terrascan to catch misconfigurations or security issues early.
- Multi-Environment Deployments: Use branch-based or label-based logic to deploy to staging, QA, or production environments with appropriate approval workflows.
- Scheduled Drift Detection: Run nightly or weekly terraform plan jobs against the last applied state to detect manual changes made outside the codebase.
Example: GitHub Actions Workflow for Terraform
Here’s a simple GitHub Actions workflow that initializes Terraform, runs a plan on pull requests, and applies changes after a merge:
name: Terraform Plan and Apply
on:
pull_request:
branches: [main]
jobs:
terraform:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v4
- name: Set up Terraform
uses: hashicorp/setup-terraform@v3
with:
terraform_version: 1.6.0
- name: Terraform Init
run: terraform init
- name: Terraform Plan
run: terraform plan
- name: Terraform Apply
if: github.event_name == 'push'
run: terraform apply -auto-approve
This GitHub Actions workflow is triggered on every pull request to the main branch. First, it checks out the code and initializes Terraform. Then, it runs terraform plan, providing reviewers with a preview of the changes that will be made to the infrastructure. If the pull request is merged (which results in a push to the main branch), the workflow continues by running terraform apply, automatically applying the approved changes to the infrastructure. This process ensures that infrastructure changes are reviewed and applied seamlessly, reducing manual intervention and increasing automation.
GitHub Actions is a versatile tool that helps automate tasks like deployment and testing. However, as infrastructure grows, managing complex workflows and ensuring compliance becomes challenging. In the next section, we’ll explore the limitations of using GitHub Actions alone for IaC projects.
Limitations of Using GitHub Actions Alone for IaC
While GitHub Actions provides excellent automation for CI/CD workflows, there are certain challenges when it comes to managing Infrastructure-as-Code (IaC) at scale. GitHub Actions is designed to handle a wide range of tasks, but when you're managing cloud resources and infrastructure code, the complexity of the processes increases. Here are some of the key limitations:
1. No Native Drift Detection
GitHub Actions can automate the execution of IaC tasks like terraform plan and terraform apply, but it doesn't detect infrastructure drift by default. Drift occurs when changes are made to cloud resources outside of your IaC code, such as manual edits in the cloud console or changes from another team. Without drift detection, there’s no way to ensure that the infrastructure in your cloud environment matches the state defined in your code, leading to potential configuration mismatches or failures.
2. Lack of Policy Enforcement
While GitHub Actions workflows can automate infrastructure provisioning, enforcing policies like cost control, security standards, or compliance checks is not built into the system. For example, there’s no built-in mechanism to ensure that every deployed resource meets internal standards (e.g., specific tags, naming conventions, or cost limits). Developers need to implement custom checks or rely on third-party tools to enforce these policies, which can add complexity and potential gaps in governance.
3. Poor Visibility Into Infrastructure Changes
GitHub Actions gives you visibility into the build and deployment process, but tracking infrastructure changes in a clear and centralized manner can be challenging. While you can see the output of terraform plan in your workflow logs, it’s not always easy to track, audit, or visualize the changes across multiple workflows, environments, or branches. This can lead to a lack of visibility into what infrastructure changes have been applied and the overall impact of those changes.
4. Manual Secrets and Variable Management
GitHub Actions provides secrets management through GitHub's encrypted secrets storage, but managing sensitive data like API keys, credentials, and environment-specific variables across multiple workflows and environments can quickly become cumbersome. If not handled carefully, this can introduce security risks, such as accidentally exposing secrets or failing to update variables across different environments. While GitHub Actions does support environment variables, maintaining a consistent and secure approach to variable management requires significant manual configuration.
5. Lack of Integrated Feedback for Pull Requests
GitHub Actions workflows provide feedback to developers on the success or failure of a pipeline, but there’s limited integration when it comes to actionable feedback within pull requests. While application and API code reviews have mature tooling, infrastructure-as-code reviews lack the same depth. For example, when a developer opens a pull request with infrastructure changes, they may not receive sufficient feedback on potential issues such as policy violations, security risks, or cost estimates related to those changes. This can delay the approval process or result in issues being discovered too late.
How Firefly Runners Improve GitHub Action Workflows
Firefly addresses these limitations out of the box. It extends GitHub Actions with built-in drift detection, policy guardrails, cost and security checks, and centralized logging, all without you writing custom workflows or rebuilding capabilities that Firefly already provides. This makes IaC deployments faster, more secure, and more reliable by default.
1. Automatic Plan and Apply on Pull Request and Merge
One of the key features of Firefly Runners is its ability to automatically trigger terraform plan and terraform apply based on pull request (PR) and merge events, which streamlines the deployment process. Here’s how it works:
- PR Trigger: When a developer opens a pull request, Firefly automatically triggers a terraform plan, allowing reviewers to view the potential impact of the proposed changes, including resource additions, modifications, and deletions.
- Merge Trigger: Once the pull request is approved and merged, Firefly automatically triggers a terraform apply to execute the changes in the cloud environment, making the process seamless and reducing manual effort.
Here’s how Firefly’s bot automatically generated a detailed terraform plan output as a GitHub PR comment, with cost impact, changed assets, and detected policy violations:
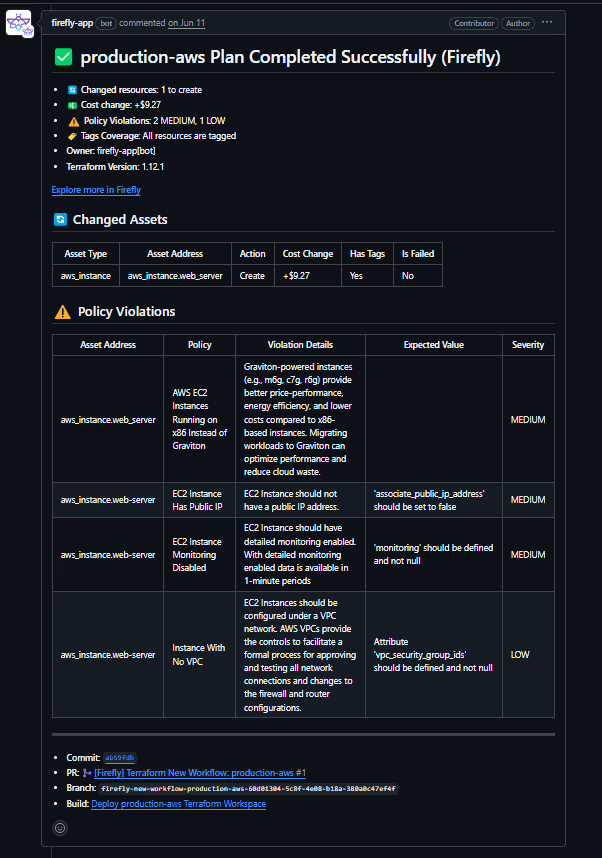
This integration provides immediate feedback to developers and ensures that only approved changes are applied to the infrastructure, reducing errors and delays.
2. PR Comments with Infrastructure Summaries and Violations
Firefly’s integration with GitHub Actions doesn’t stop at triggering terraform plan and apply. It goes a step further by providing detailed summaries directly in PR comments. Here’s what you get:
- Infrastructure Summary: Firefly includes a summary of the proposed infrastructure changes, such as which resources are being added, modified, or destroyed. This gives developers and reviewers visibility into the exact changes that are being made before they are applied.
- Guardrail Violations: If any changes violate established policies (e.g., cost rules, security policies, tagging standards), Firefly will immediately flag these violations in the PR comments. This gives the team the opportunity to fix issues before they are merged, reducing the chances of policy violations in production environments.
3. Policy Guardrails to Block Unsafe Code
Firefly provides Guardrails that automatically enforce policies around security, cost, and compliance. These policies can be defined in advance and automatically evaluated whenever a new plan is generated.
- Cost Guardrails: Prevent changes that would increase infrastructure costs beyond predefined thresholds, such as blocking the creation of expensive resources or triggering alerts when cost estimates exceed a certain value.
- Security and Compliance Guardrails: Ensure that resources comply with best practices, such as enforcing encryption for storage services, ensuring no publicly accessible databases are provisioned, or blocking the use of certain instance types.
- Tagging Policies: Automatically enforce consistent tagging across all resources, helping with cost allocation, monitoring, and resource organization.
Firefly’s Guardrails ensure that your infrastructure changes align with your organization’s policies and standards, and provide an automated way to enforce these rules without requiring manual intervention.
4. Drift Detection via Periodic Plan
Firefly automatically detects infrastructure drift by scheduling periodic terraform plan executions. Drift detection is critical for identifying configuration changes that have been made outside of the infrastructure-as-code pipeline. For instance:
- Detecting Out-of-Band Changes: Firefly will run periodic terraform plan checks, even if no new PRs are opened, and detect if manual changes have been made in the cloud console or through other tools.
- Alerts on Drift: If drift is detected, Firefly will alert the relevant team members, ensuring that infrastructure stays consistent with the IaC code and is always in a known and controlled state.
This provides an added layer of visibility and control, especially when managing large and dynamic environments where infrastructure changes can happen at any time.
5. Centralized Logging and Dashboards
With Firefly, all infrastructure operations, whether plan or apply, are logged in a centralized dashboard. This improves traceability, troubleshooting, and auditing:
- Detailed Logs: Firefly records all actions, including plan results, apply results, and any violations or warnings triggered during the workflow execution.
- Audit Trails: The logs serve as an audit trail, providing full visibility into who made which changes and when, which is invaluable for both security and operational purposes.
- Centralized Monitoring: Teams can track all workflows, monitor execution status, and quickly identify issues in the deployment pipeline, streamlining troubleshooting and improving operational efficiency.
6. Integrated Variable and Secret Management
Firefly provides centralized variable management to ensure consistency across workspaces and environments. Variables can be defined at the project level and inherited by all associated workspaces. This reduces duplication and minimizes the chance of inconsistent configurations across environments.
- Sensitive Variables: Firefly allows you to mark sensitive values (e.g., API keys, database credentials) as sensitive, ensuring they are encrypted and redacted in logs.
- Centralized Access Control: Variables and secrets can be shared across projects, ensuring that all workspaces have access to the necessary configuration values while enforcing proper access controls.
This integrated management of variables and secrets ensures that configuration values are consistently used across all workflows, without exposing sensitive information.
7. Manual vs Auto-Apply Controls for Different Environments
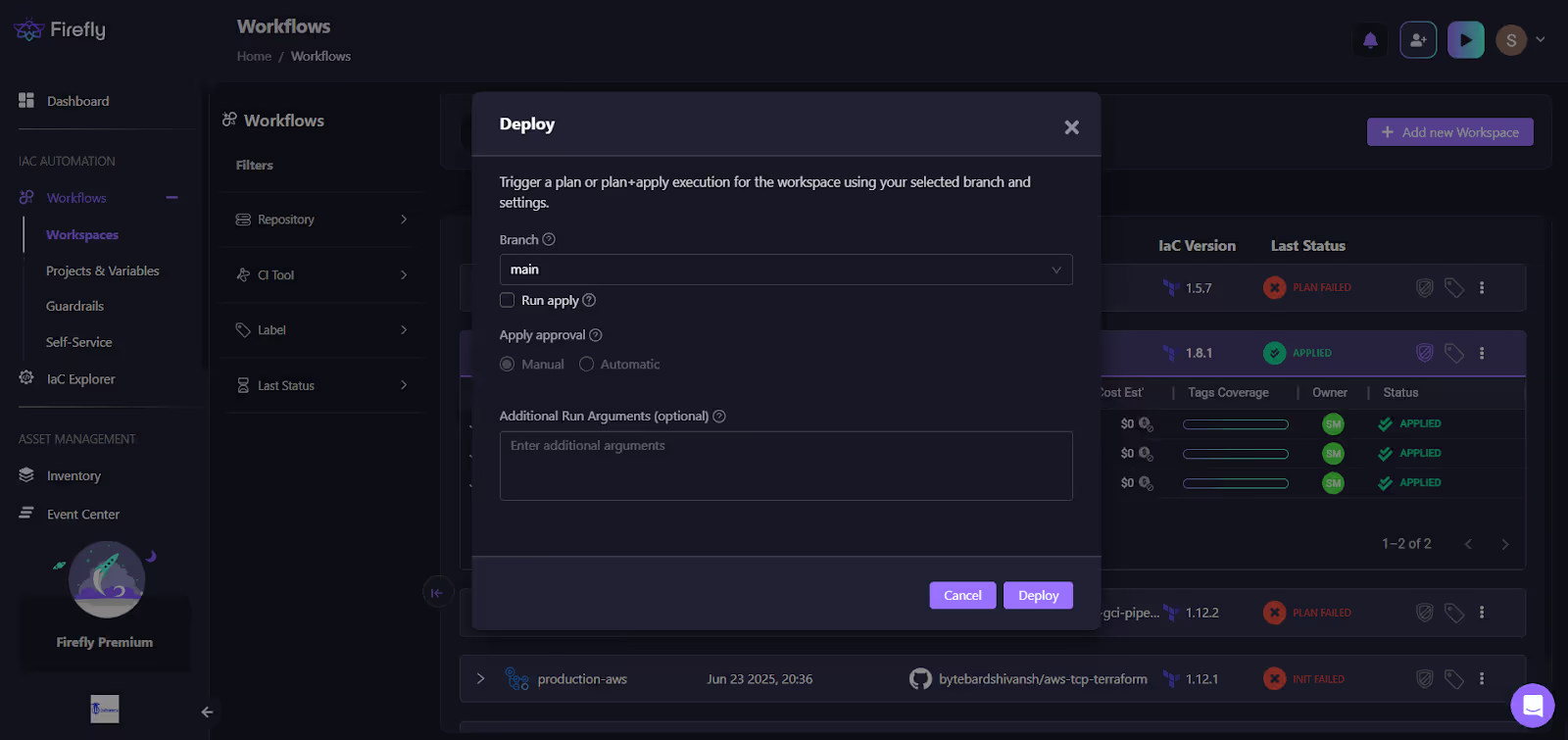
As shown in the above snapshot from Firefly UI, while deploying, wo offers flexibility in how infrastructure changes are applied:
- Manual Apply: In production or critical environments, manual approval for terraform apply ensures that any changes are thoroughly reviewed before being applied. This acts as a safeguard to prevent accidental changes in sensitive environments.
- Auto Apply: For non-production environments or development, Firefly allows automatic application of changes after a successful plan, speeding up the deployment process and reducing manual effort.
This ensures that Firefly can be configured to meet the needs of both fast-paced development environments and more controlled production workflows.
Firefly Integration Options: Two Paths
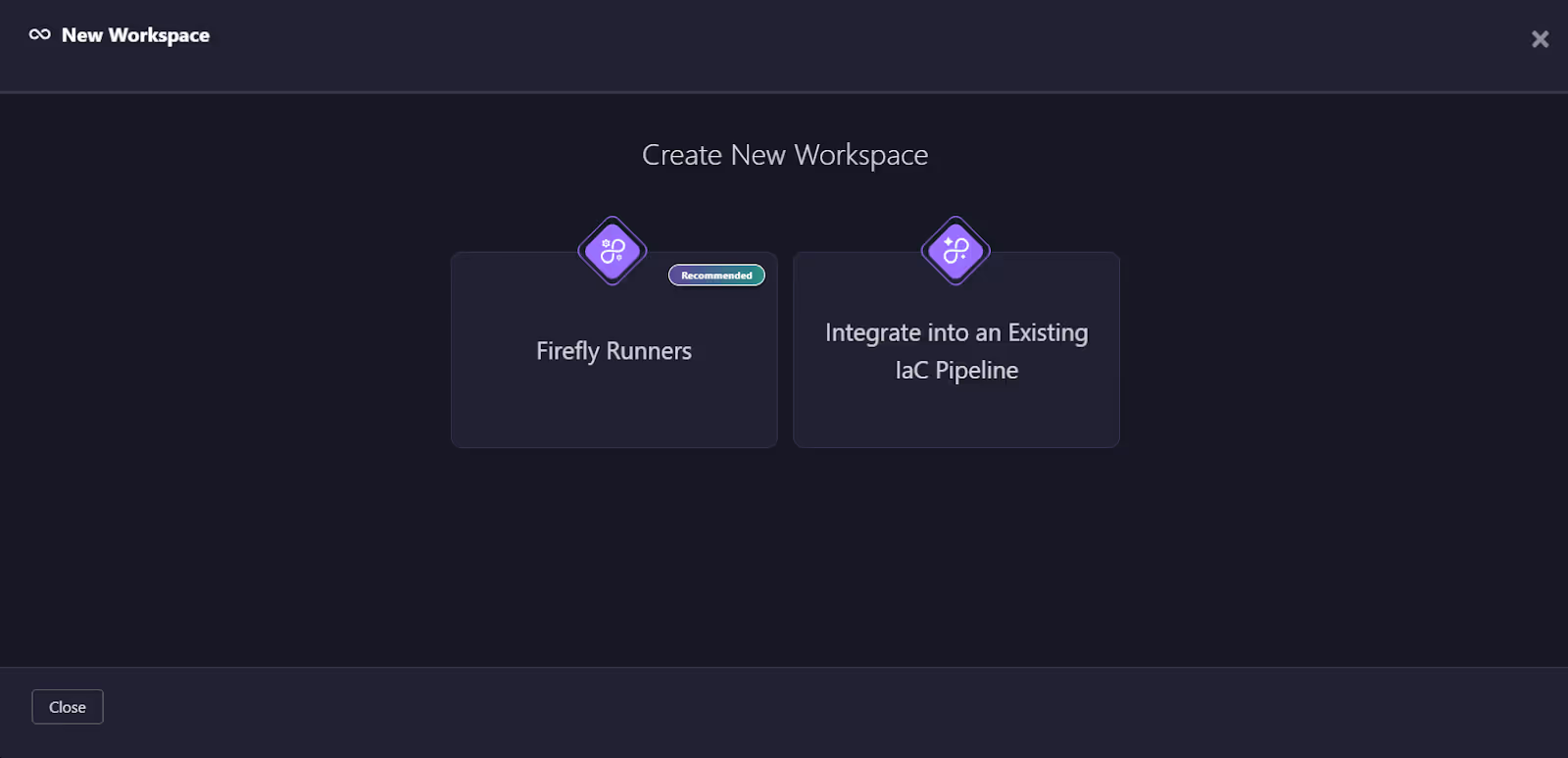
When creating a new workspace in Firefly, the UI presents two distinct integration options for connecting with your existing GitHub Actions workflows: Firefly-Managed Workflows and Hybrid GitHub Actions Integration. Depending on your team's needs and existing CI/CD setup, you can choose the method that best fits your requirements.
Firefly Integration Options: Two Paths
When creating a new workspace in Firefly, you are presented with two integration models for working with your GitHub Actions workflows: Firefly-Managed Workflows and Hybrid GitHub Actions Integration. Each serves a different operational need, depending on whether you want a fully managed setup or a complement to an existing pipeline.
Firefly-Managed Workflows
In this model, Firefly assumes full control of the execution environment and automates the entire pipeline process. Your workspace is defined in the Firefly UI and connected to your version-controlled IaC repository, such as one hosted on GitHub. When a pull request is opened or changes are merged into the main branch, Firefly automatically triggers terraform plan and terraform apply using its own secure runners.
All aspects of the infrastructure-as-code lifecycle, drift detection, policy enforcement through guardrails, and logging are handled directly within Firefly. This approach is particularly suitable for teams seeking a simplified IaC deployment process that eliminates the operational burden of managing CI/CD runners. It is also well-suited for teams aiming to reduce complexity while retaining control and security.
The main advantage of this model lies in its ease of setup. Firefly’s infrastructure removes the need for configuring runners, and governance capabilities are built in by default. Execution takes place in an isolated environment, ensuring secure Terraform, OpenTofu, or Terragrunt operations. For teams that want a quick, well-governed, and automated IaC workflow without the responsibility of maintaining infrastructure, this is the recommended option.
Hybrid GitHub Actions Integration
The hybrid model is designed for teams that already operate a mature GitHub Actions CI/CD pipeline and prefer to keep execution within that environment while enhancing it with Firefly’s capabilities. In this setup, Firefly connects to your existing pipeline using the fireflyci CLI or GitHub Action. Execution of terraform plan and terraform apply remains in GitHub Actions, but results can be sent to Firefly for analysis, policy checks, and audit logging.
This approach leaves your current workflows intact, allowing you to benefit from Firefly’s visualization, drift detection, and governance without major changes to the CI/CD structure. Firefly adds value by providing centralized monitoring and posting automated feedback directly on pull requests, including policy violations and detailed change summaries.
The hybrid model is ideal for organizations that need to maintain full control over their CI/CD environment while gaining the visibility, policy enforcement, and insights that Firefly offers. It is a way to extend, rather than replace, your existing automation processes.
Code Snippet for Hybrid Integration
For teams using GitHub Actions and integrating Firefly for enhanced visibility and monitoring, here’s a simple example of how you can post the Terraform plan results to Firefly:
#Option 1
- name: Post Plan to Firefly
uses: gofireflyio/fireflyci-action@v1
with:
args: post-plan
env:
FIREFLY_ACCESS_KEY: ${{ secrets.FIREFLY_ACCESS_KEY }}
#option 2
- name: Download Firefly CLI
run: |
curl -O https://gofirefly-prod-iac-ci-cli-binaries.s3.amazonaws.com/fireflyci/latest/fireflyci_Linux_x86_64.tar.gz
tar -xf fireflyci_Linux_x86_64.tar.gz
chmod +x fireflyci
- name: Post Plan to Firefly (CLI)
env:
FIREFLY_ACCESS_KEY: ${{ secrets.FIREFLY_ACCESS_KEY }}
FIREFLY_SECRET_KEY: ${{ secrets.FIREFLY_SECRET_KEY }}
run: ./fireflyci post-plan -l plan_log.jsonl -f plan_output.json --workspace test-workspace
This step takes the generated Terraform plan logs (plan_log.jsonl and plan_output.json) and posts them to Firefly, either through the official Firefly GitHub Action or the Firefly CLI binary. Once uploaded, Firefly evaluates the plan against the governance policies you’ve configured in your workspace. It then provides real-time feedback in the form of pull request comments, highlighting violations or compliance issues. This ensures that every infrastructure change is automatically reviewed, validated, and kept in line with your organization’s standards before being applied.
Example: Integrating Firefly in an Existing GitHub Action Workflow
Here is an existing GitHub Action YAML for a Terraform deployment, which integrates Firefly for better visibility and control over your infrastructure deployment.
name: Terraform with Firefly CI
on:
push:
branches: [ main ]
workflow_dispatch:
inputs:
action:
description: "Terraform action to perform"
required: true
default: "apply"
type: choice
options:
- apply
- destroy
jobs:
deploy:
runs-on: ubuntu-latest
permissions:
contents: read
id-token: write
env:
FIREFLY_ACCESS_KEY: ${{ secrets.FIREFLY_ACCESS_KEY }}
FIREFLY_SECRET_KEY: ${{ secrets.FIREFLY_SECRET_KEY }}
steps:
- name: Checkout repo
uses: actions/checkout@v4
- name: Set up Terraform
uses: hashicorp/setup-terraform@v3
with:
terraform_version: 1.8.1
- name: Authenticate to GCP
uses: google-github-actions/auth@v2
with:
credentials_json: '${{ secrets.GCP_CREDENTIALS_JSON }}'
- name: Terraform Init
run: terraform init
- name: Terraform Plan and Generate Logs
if: github.event_name == 'push' || github.event.inputs.action == 'apply'
run: |
terraform plan -json -out=tf.plan > plan_log.jsonl
terraform show -json tf.plan > plan_output.json
- name: Download Firefly CLI
if: github.event_name == 'push' || github.event.inputs.action == 'apply'
run: |
curl -O https://gofirefly-prod-iac-ci-cli-binaries.s3.amazonaws.com/fireflyci/latest/fireflyci_Linux_x86_64.tar.gz
tar -xf fireflyci_Linux_x86_64.tar.gz
chmod +x fireflyci
- name: Firefly Post Plan
if: github.event_name == 'push' || github.event.inputs.action == 'apply'
run: ./fireflyci post-plan -l plan_log.jsonl -f plan_output.json --workspace test-workspace
- name: Terraform Apply with Log
if: github.event_name == 'push' || github.event.inputs.action == 'apply'
run: terraform apply -auto-approve -json > apply_log.jsonl
- name: Firefly Post Apply
if: github.event_name == 'push' || github.event.inputs.action == 'apply'
run: ./fireflyci post-apply -f apply_log.jsonl --workspace test-workspace
- name: Terraform Destroy with Log
if: github.event.inputs.action == 'destroy'
run: terraform destroy -auto-approve -json > destroy_log.jsonlThis workflow triggers on push to the main branch or manually via workflow_dispatch. It also accepts a choice input (apply or destroy) for the action.
- Steps:
- It checks out the code, sets up Terraform, and authenticates to GCP.
- It runs terraform plan, generating a log and output that are used later.
- The Firefly CLI is downloaded and used to post the plan and apply logs to Firefly for better visibility and tracking.
- Finally, terraform apply or terraform destroy is executed, depending on the action.
After running the plan and applying steps, Firefly monitors and ensures the deployment adheres to your organization's policies and best practices. Here's a visual of what this looks like within the Firefly platform:
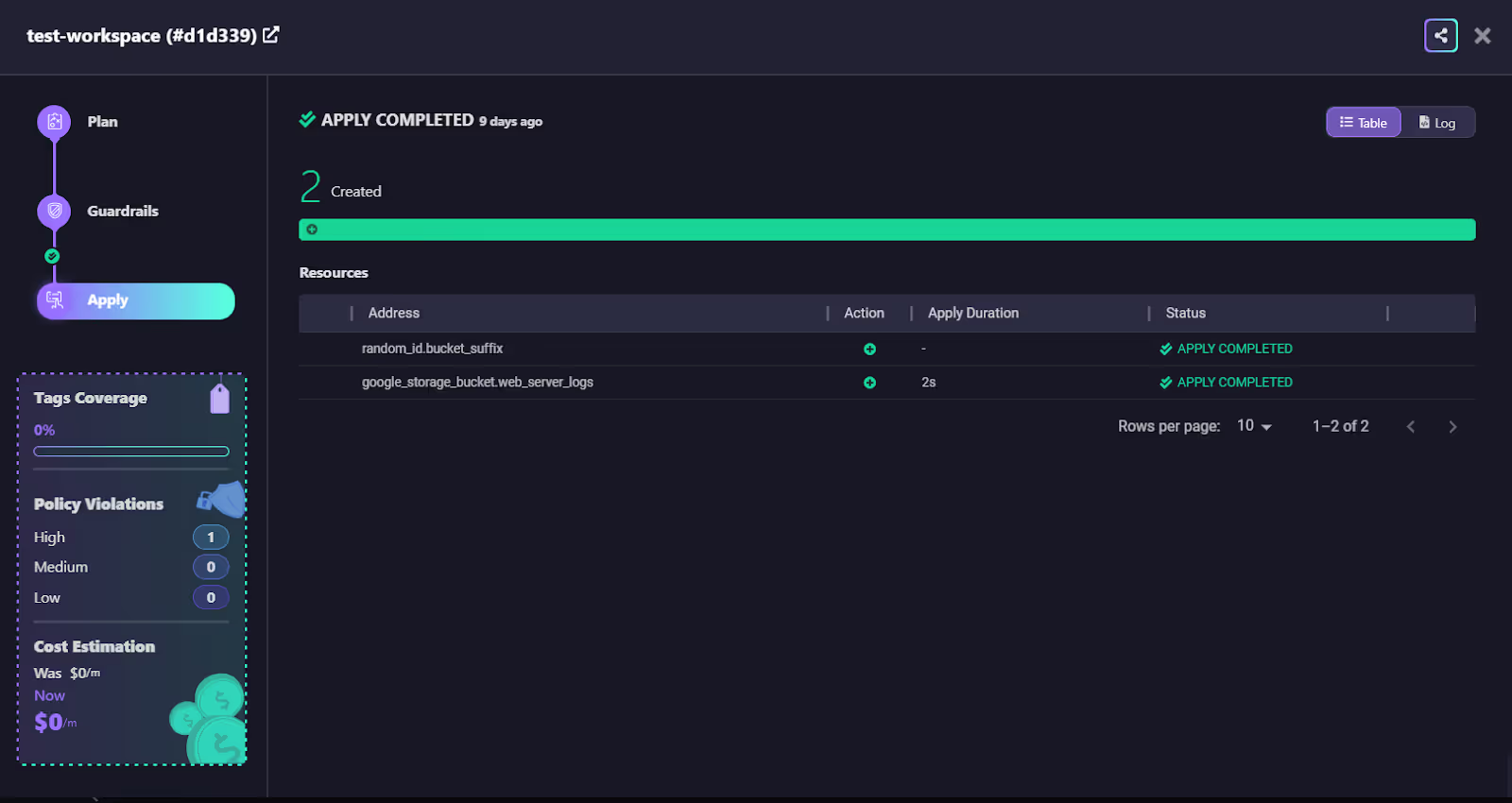
The above summary of the applied changes provides a detailed breakdown of the infrastructure deployment. It highlights the resources created, which lists all the resources that were affected during the deployment process. This gives you visibility into the exact components that were added or modified in your infrastructure.
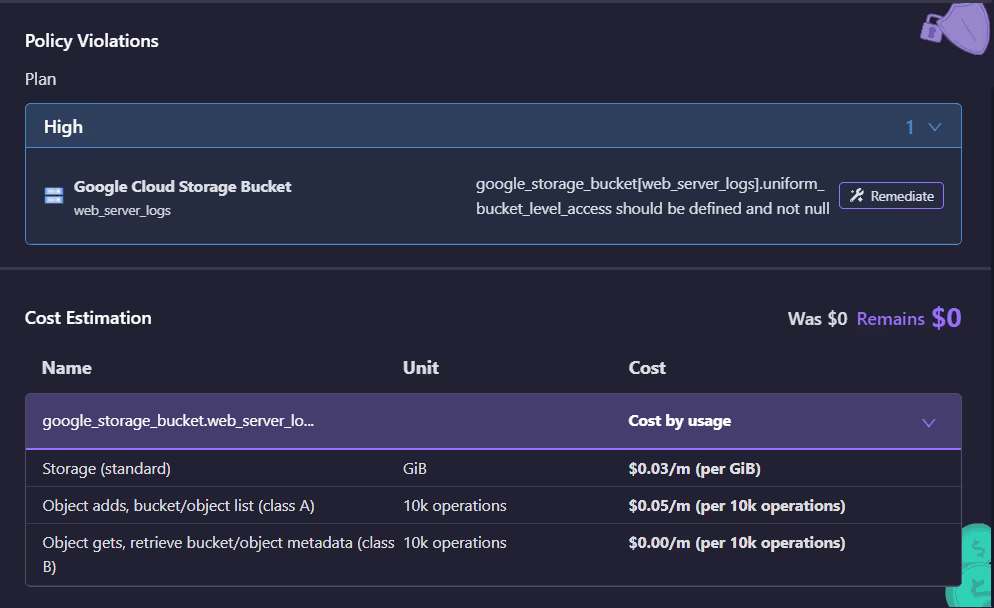
Additionally, the policy violations section shows any issues with your deployment, such as security misconfigurations or cost overruns. This feature helps you stay compliant with organizational standards by flagging any violations before they can cause problems in your environment.
Why Firefly if you already use GitHub Actions?
Firefly doesn’t replace GitHub Actions; it enhances it. By integrating Firefly Workflows, teams gain: structured organization and RBAC via projects; centralized variable and workflow management; automated policy enforcement through guardrails; drift detection; and a unified UI for logging, visualization, and audit trails. Whether using Firefly-managed runners or augmenting your current pipelines, you get governance, visibility, and scalability that GitHub Actions alone doesn’t offer.
Conclusion
Automating your GitHub Action workflows with Firefly significantly enhances the efficiency, security, and scalability of your infrastructure deployments. By integrating Firefly with Terraform, OpenTofu, and Terragrunt, you can automate critical processes like plan generation, policy enforcement, apply execution, and cost estimation, all while maintaining full visibility and control. Firefly’s seamless integration with your existing CI/CD pipelines allows for immediate feedback on policy violations, drift detection, and detailed execution logs.
With features like policy guardrails, automatic logging, and centralized management, Firefly ensures that your infrastructure changes adhere to organizational standards and best practices. Whether you opt for fully managed Firefly workflows or hybrid integrations with GitHub Actions, the platform enables teams to deploy infrastructure confidently, reducing human errors and operational overhead.
FAQs
1. What is the Difference Between Github Actions and Workflows?
GitHub Actions is the platform where you define tasks and jobs to automate your CI/CD pipeline. A workflow in GitHub Actions is a collection of jobs that are triggered by events in your repository (e.g., pull requests, pushes). Workflows are typically defined in YAML files located in the .github/workflows directory.
2. What is the Difference Between Jenkins and Github Workflows?
Jenkins is a widely used open-source automation server for continuous integration and continuous delivery. It provides extensive plugin support and flexibility for creating complex pipelines. GitHub workflows, on the other hand, are defined directly within the GitHub repository, offering a more integrated experience with GitHub services and actions for automation, CI/CD, and version control.
3. Is GitHub workflow YML or YAML?
GitHub workflows use YAML (YAML Ain't Markup Language), a human-readable data serialization format. .yml is simply a file extension commonly used for YAML files, so they both refer to the same format.
4. What is the Difference Between Name and Id in Github Workflows?
In a GitHub workflow, name refers to a human-readable label for the workflow or job, making it easier to identify in the GitHub Actions UI. ID is typically used for internal reference and can uniquely identify a job or a step within the workflow for tracking purposes. The name is for user understanding, while the ID is used programmatically within the workflow.


