Over the past decade, cloud environments have evolved from static infrastructures to highly dynamic, distributed systems. The rise of multi-cloud, hybrid cloud, and microservices architectures has complicated compliance practices. Workloads now span multiple providers, services, and regions, creating environments too complex for manual audits, spreadsheets, or periodic checks to manage effectively. Continuous configuration changes make it easy for gaps to slip through and remain undetected until they cause real issues.
Regulatory demands add further pressure. GDPR, CCPA, and new AI/ML requirements require real-time compliance and continuous monitoring.
As highlighted in a recent Twitter post, the global cloud compliance market is projected to grow from USD 30 billion in 2022 to USD 59.1 billion by 2027. This growth underscores how essential automation has become: embedding compliance into development and deployment workflows allows organizations to catch misconfigurations early, enforce policies consistently, and reduce risk across distributed environments.
This blog explains why compliance automation is critical in the cloud era, outlines the tools and technologies that enable it, and breaks down the core pillars that support this shift. It also presents real-world examples, such as using Terraform and Checkov to automate compliance checks, and shows how integration with CI/CD pipelines can make compliance a continuous process instead of a one-time task. Finally, it covers best practices and future trends to help organizations stay ahead in the evolving world of cloud compliance.
What Is Cloud Security Compliance Automation?
Cloud Security Compliance Automation refers to the use of tools and technologies to continuously enforce, monitor, and maintain compliance in cloud environments. Instead of waiting for periodic audits or manual reviews, compliance rules are embedded directly into infrastructure, code, and workflows. This ensures that compliance is monitored in real-time and any deviations are addressed immediately.
By integrating compliance into the development pipeline and infrastructure as code (IaC), automation ensures that every cloud resource, whether it’s a virtual machine, storage bucket, or Kubernetes cluster, meets regulatory and security standards before being deployed and continuously throughout its lifecycle.
Core Pillars of Compliance Automation
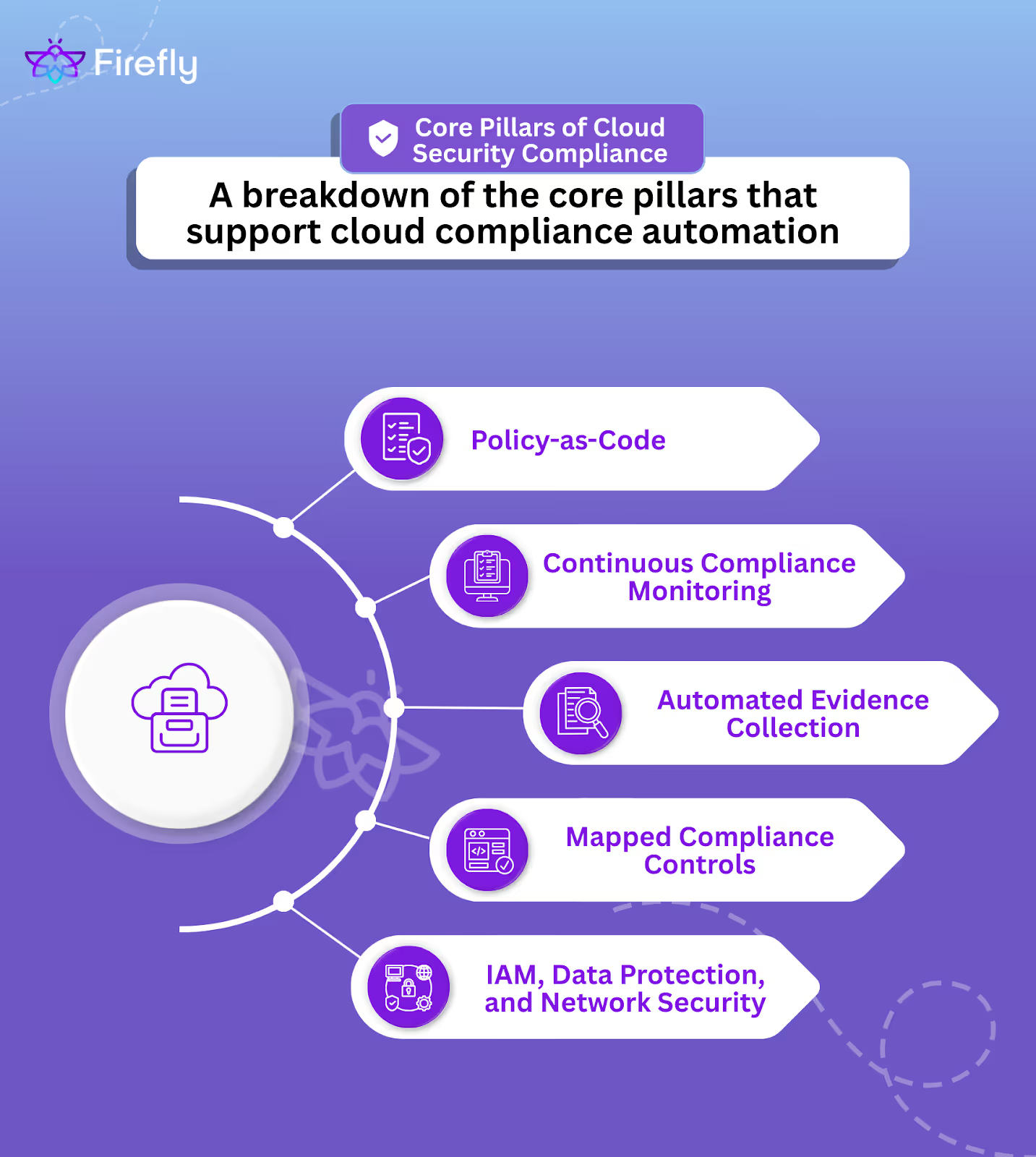
Cloud environments require a robust approach to security and compliance to ensure resources are protected from threats and adhere to regulatory requirements. The core pillars of Cloud Security and Compliance Automation ensure that both security and compliance are continuously monitored and enforced across dynamic cloud infrastructures.
Policy-as-Code
Policy-as-Code defines compliance rules directly in code. These policies are version-controlled, tested, and enforced whenever infrastructure is deployed. This maintains continuous compliance, rather than relying on periodic manual checks.
- Example: A rule may require encryption for all storage. If a resource is deployed without encryption, the system blocks it.
- Benefits: Automates compliance, ensures consistency, and enables audit-friendly version control of policies.
Continuous Compliance Monitoring
Continuous Compliance Monitoring evaluates cloud resources in real time against standards. Cloud Security Posture Management (CSPM) tools scan environments to detect misconfigurations, policy violations, or security gaps.
- Example: A public-facing storage bucket without encryption is flagged immediately.
- Some tools not only alert but can auto-remediate, keeping resources compliant without human intervention.
Automated Evidence Collection
Automated Evidence Collection replaces manual effort during audits. Compliance tools continuously capture logs, configurations, permissions, and security settings.
- Centralized storage ensures quick access for audits.
- Audit data stays current, saving time and reducing errors during external reviews.
- Especially critical in industries with frequent audits (e.g., finance, healthcare).
Mapped Compliance Controls
Mapped Compliance Controls tie regulatory frameworks directly into Infrastructure-as-Code (IaC). Embedding compliance checks in Terraform or CloudFormation ensures a compliant infrastructure at deployment.
- Example: Terraform scripts can enforce encryption and access logging on every storage bucket.
- Result: Every provisioned resource automatically adheres to security and compliance standards.
Identity and Access Management (IAM)
Identity and Access Management (IAM) enforces access control across cloud resources. Automation tools scan IAM policies to detect excessive permissions, missing MFA, or misconfigured roles.
- IAM automation enforces least privilege.
- Tools ensure only required permissions are granted.
- Compliance risks from over-permissioning are reduced.
Data Protection
Data Protection safeguards sensitive data at rest, in transit, and in use. Compliance automation verifies encryption and enforces protection throughout the data lifecycle.
- Example: If a storage bucket lacks encryption, automation flags or remediates it.
- Data Loss Prevention (DLP) tools monitor the movement of sensitive data and block unauthorized transfers.
Network Security
Network Security secures cloud connectivity and prevents unauthorized access. Compliance automation validates network setups and monitors for violations.
- Tools verify segmentation of VPCs, firewall rules, and DDoS protection.
- Policies check routing tables, VPNs, and subnet rules against compliance frameworks.
Governance and Compliance
Governance and Compliance automation ensure cloud operations align with legal and industry requirements such as GDPR, HIPAA, and PCI-DSS.
- Tools continuously track adherence to regulations.
- The Shared Responsibility Model is embedded into automation, clarifying which controls are managed by the provider versus the customer.
Security Monitoring and Incident Response
Security Monitoring and Incident Response provide real-time visibility and fast remediation of threats. SIEM platforms and cloud-native services like GuardDuty or Google Cloud SCC track potential violations.
- Automated workflows alert teams, log incidents, and trigger responses.
- Example: A non-compliant resource can be patched or access restricted immediately.
- Benefit: Breaches and compliance gaps are handled before escalation.
Cloud Compliance Automation rests on these pillars: Policy-as-Code, Continuous Monitoring, Automated Evidence Collection, IAM, Data Protection, and Governance. Together, they maintain compliance continuously, reduce human error, and secure cloud environments end-to-end.
Automating Compliance Checks with Checkov on Terraform
This section demonstrates how to automate security and compliance checks for a Terraform script using Checkov. The goal is to provision a Google Cloud Storage bucket with Terraform and scan the script for compliance violations based on industry best practices.
Start by writing a Terraform configuration that provisions a Google Cloud Storage bucket. This script uses the Google Cloud provider and the Random provider to create a bucket with a random name.
terraform {
required_providers {
google = {
source = "hashicorp/google"
version = ">= 5.0"
}
random = {
source = "hashicorp/random"
version = ">= 3.0"
}
}
}
provider "google" {
project = var.project_id
region = var.region
}
variable "project_id" {}
variable "region" { default = "us-central1" }
variable "location" { default = "US" }
resource "random_id" "suffix" {
byte_length = 4
}
resource "google_storage_bucket" "demo" {
name = "csa-demo-${var.project_id}-${random_id.suffix.hex}"
location = var.location
}Explanation:
- A Google Cloud Storage bucket resource (google_storage_bucket.demo) is defined.
- The bucket name is a combination of the project ID and a randomly generated suffix.
- The location is set to US. Other configurations are left to defaults for simplicity.
To scan the TF script for compliance issues, use Checkov to evaluate the script against security best practices. This can be done by running the following command:
checkov -f main.tf
The scan will output results, showing whether any misconfigurations or compliance violations are present. Here's an example output:
[ terraform framework ]: 100%|████████████████████|[1/1], Current File Scanned=main.tf
[ secrets framework ]: 100%|████████████████████|[1/1], Current File Scanned=main.tf
[ secrets framework ]: 100%|████████████████████|[1/1], Current File Scanned=main.tf
_ _
___| |__ ___ ___| | _______ __
/ __| '_ \ / _ \/ __| |/ / _ \ \ / /
| (__| | | | __/ (__| < (_) \ V /
\___|_| |_|\___|\___|_|\_\___/ \_/
By Prisma Cloud | version: 3.2.457
Update available 3.2.457 -> 3.2.467
Run pip3 install -U checkov to update
terraform scan results:
Passed checks: 0, Failed checks: 4, Skipped checks: 0
Check: CKV_GCP_62: "Bucket should log access"
FAILED for resource: google_storage_bucket.demo
File: \main.tf:27-30
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/google-cloud-policies/google-cloud-storage-gcs-policies/bc-gcp-logging-2
27 | resource "google_storage_bucket" "demo" {
28 | name = "csa-demo-${var.project_id}-${random_id.suffix.hex}"
29 | location = var.location
30 | }
Check: CKV_GCP_78: "Ensure Cloud storage has versioning enabled"
FAILED for resource: google_storage_bucket.demo
File: \main.tf:27-30
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/google-cloud-policies/google-cloud-general-policies/ensure-gcp-cloud-storage-has-versioning-enabled
27 | resource "google_storage_bucket" "demo" {
28 | name = "csa-demo-${var.project_id}-${random_id.suffix.hex}"
29 | location = var.location
30 | }
Check: CKV_GCP_29: "Ensure that Cloud Storage buckets have uniform bucket-level access enabled"
FAILED for resource: google_storage_bucket.demo
File: \main.tf:27-30
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/google-cloud-policies/google-cloud-storage-gcs-policies/bc-gcp-gcs-2
27 | resource "google_storage_bucket" "demo" {
28 | name = "csa-demo-${var.project_id}-${random_id.suffix.hex}"
29 | location = var.location
30 | }
Check: CKV_GCP_114: "Ensure public access prevention is enforced on Cloud Storage bucket"
FAILED for resource: google_storage_bucket.demo
File: \main.tf:27-30
Guide: https://docs.prismacloud.io/en/enterprise-edition/policy-reference/google-cloud-policies/google-cloud-general-policies/bc-google-cloud-114
27 | resource "google_storage_bucket" "demo" {
28 | name = "csa-demo-${var.project_id}-${random_id.suffix.hex}"
29 | location = var.location
30 | }The scan results show 4 failed checks, each indicating security and compliance gaps in the bucket configuration:
- CKV_GCP_62: "Bucket should log access"
- The bucket is missing access logging, which is essential for auditing and tracking access to data.
- The bucket is missing access logging, which is essential for auditing and tracking access to data.
- CKV_GCP_78: "Ensure Cloud storage has versioning enabled"
- Versioning is not enabled, meaning that data could be lost or overwritten without recovery.
- Versioning is not enabled, meaning that data could be lost or overwritten without recovery.
- CKV_GCP_29: "Ensure that Cloud Storage buckets have uniform bucket-level access enabled"
- The bucket does not have uniform access controls, which can lead to inconsistent access and potential security vulnerabilities.
- The bucket does not have uniform access controls, which can lead to inconsistent access and potential security vulnerabilities.
- CKV_GCP_114: "Ensure public access prevention is enforced on Cloud Storage bucket"
- The bucket allows public access, which could expose sensitive data to unauthorized users.
To resolve the compliance issues, update the Terraform script to include the necessary security features. Here's an updated version of the script that addresses the violations:
resource "google_storage_bucket" "demo" {
name = "csa-demo-${var.project_id}-${random_id.suffix.hex}"
location = var.location
# Enable access logging
logging {
log_bucket = "logging-bucket" # Replace with your log bucket name
log_object_prefix = "access-log"
}
# Enable versioning
versioning {
enabled = true
}
# Enforce uniform bucket-level access
uniform_bucket_level_access = true
# Disable public access
iam_configuration {
public_access_prevention = "enforced"
}
}Once the Terraform script is updated, re-run the Checkov scan to verify that all compliance violations are resolved. With the updated configuration, Checkov should now return 0 failed checks, confirming that the Google Cloud Storage bucket is compliant with the required security and compliance standards.
Benefits of Compliance Automation
Compliance automation makes cloud security proactive, scalable, and efficient. By embedding checks into development and deployment workflows, it strengthens security while reducing manual overhead.
Improved Security Posture
Compliance automation enforces security best practices consistently. Automated checks validate encryption, access controls, and MFA, reducing the risk of misconfigurations and human error.
- Proactive enforcement minimizes security gaps.
- Misconfigured resources are flagged before exposure.
- Security posture improves through continuous validation.
Faster Remediation and Reduced Risk
Automated monitoring flags violations in real time and can remediate issues instantly. This speed is a sharp contrast to manual audits, which often uncover issues late.
- Example: An S3 bucket with public access is immediately flagged, and in some cases automatically corrected.
- Rapid response reduces the window of exposure.
- Risks of breaches and compliance failures are significantly lowered.
Continuous Monitoring and Audit Readiness
Compliance automation provides always-on monitoring and continuous audit readiness. Evidence of compliance is available in real time, eliminating last-minute scrambles.
- Regulations like GDPR, HIPAA, and PCI DSS require ongoing adherence.
- Automated tools log configurations, access, and security data continuously.
- Audit reporting becomes faster, simpler, and less resource-intensive.
Cross-Cloud Consistency
Multi-cloud operations create complexity due to platform-specific policies. Automation standardizes compliance across providers like AWS, Azure, and Google Cloud.
- Tools such as Checkov enforce consistent policies in Terraform or CloudFormation.
- Security controls are applied uniformly regardless of cloud provider.
- Multi-cloud environments remain compliant without manual harmonization.
Enhanced Efficiency and Cost Savings
Automation reduces the time and cost of manual auditing and remediation. Catching compliance issues early prevents costly production problems.
- Encryption, access logging, and network rules are enforced automatically.
- Preventing data breaches reduces recovery costs.
- Teams spend more time building solutions instead of chasing compliance fixes.
Scalable Compliance Practices
Compliance automation grows with the cloud environment. Policies scale automatically as infrastructure expands or new services are added.
- Large and dynamic cloud environments stay compliant by default.
- Security standards are embedded into every new resource.
- Compliance never lags behind infrastructure growth.
Benefits of Cloud Compliance Automation
Cloud compliance automation enforces security and regulatory requirements without relying on manual processes. It continuously monitors cloud environments, eliminates human error, and keeps compliance aligned with industry standards. This approach saves time, reduces risk, and enables organizations to scale securely.
Continuous Compliance and Monitoring
Automation replaces point-in-time audits with real-time compliance checks. Configuration drift is detected and corrected immediately, keeping the environment always audit-ready.
1. Proactive Risk Management
Automated scanning identifies vulnerabilities and misconfigurations across multi-cloud and hybrid environments before they become breaches. Early remediation reduces the chance of costly security incidents
2. Enhanced Security Posture
Consistent, automated enforcement of security policies closes gaps often introduced by manual processes. Automation also accelerates detection and response to new threats, strengthening defenses across the cloud.
3. Scalability Across Environments
Compliance automation scales with cloud growth. As infrastructure expands across platforms and services, policies remain consistent and up to date regardless of environment size or complexity.
4. Cost and Time Savings
Evidence collection, control testing, and reporting are automated, reducing audit preparation costs and freeing teams from repetitive tasks. Resources can be directed toward higher-value engineering and security work.
5. Accuracy and Consistency
Automation removes human error from compliance tasks. Policies are enforced uniformly across all cloud resources, reducing the risk of misconfigurations and non-compliance penalties.
6. Streamlined Audits
Audit evidence and reports are generated automatically and on demand. Organizations stay audit-ready year-round, and external audits become faster and less resource-intensive.
7. Faster Deployment and Innovation
Integrating compliance checks into DevOps and CI/CD pipelines ensures that new applications and services ship quickly without sacrificing compliance. Teams can innovate with confidence while maintaining security standards.
8. Stronger Stakeholder Confidence
Continuous compliance builds trust with customers, regulators, and partners. A proven ability to maintain security and compliance becomes a competitive advantage in the market.
Compliance automation strengthens security, reduces risk, lowers costs, and accelerates delivery. By embedding automated checks into cloud operations and pipelines, organizations achieve continuous compliance without slowing innovation.
Challenges & How to Solve Them

While cloud compliance automation offers significant benefits, it also presents challenges related to the scale and complexity of modern environments. False positives, evolving regulations, fragmented multi-cloud policies, and developer resistance can all reduce effectiveness if not addressed.
The right mix of policy-as-code, contextual intelligence, and seamless integration into CI/CD pipelines enables the transformation of compliance from a roadblock into a continuous, automated safeguard.
False Positives and Contextual Rules
One of the most common pain points with compliance automation is false positives, alerts that flag configurations as violations even when they are not risky. This creates unnecessary remediation work and can erode trust in the system.
Firefly minimizes false positives with context-aware scanning, which uses metadata and resource configuration details to assess compliance more accurately. AI-driven prioritization filters out minor deviations that don't impact security, ensuring that teams focus on meaningful issues. Additionally, dynamic policy management adjusts compliance rules based on the specific context of each cloud provider and environment (e.g., AWS, Azure, GCP), reducing the occurrence of false positives in multi-cloud environments.
Handling Complex Regulations
Compliance frameworks such as GDPR, PCI DSS, and HIPAA are subject to frequent updates and vary by geography. This makes ongoing compliance management complex, as organizations must keep pace with evolving regulations.
Firefly provides pre-configured Compliance Packs for standards like SOC 2, ISO 27001, and GDPR, which are regularly updated to reflect changes in regulations. Organizations can extend these packs with Policy-as-Code, integrating compliance directly into Infrastructure-as-Code (IaC) templates like Terraform or CloudFormation. A centralized policy repository ensures that updates are automatically applied across all environments, helping organizations maintain continuous compliance without manual intervention.
Managing Multiple Cloud Environments
As organizations adopt multi-cloud strategies, managing compliance becomes more challenging. Each cloud provider (AWS, Azure, Google Cloud) has its own set of policies and compliance frameworks, making it difficult to maintain consistent governance across environments.
Firefly supports multi-cloud compliance by providing tools that can scan resources across different cloud platforms. Policies are applied consistently across AWS, Azure, and Google Cloud, consolidating compliance findings in a single dashboard. This reduces the complexity of managing separate compliance workflows for each cloud provider, allowing teams to monitor and enforce policies from a unified interface.
Continuous Policy Updates
As compliance baselines and regulations evolve, updating compliance rules across every Infrastructure-as-Code (IaC) template can be time-consuming and error-prone, leading to inconsistencies in policy enforcement.
Firefly integrates compliance rules directly into version-controlled repositories, allowing automatic propagation of updates across all IaC templates. When Compliance Packs or custom policies are updated, those changes are automatically enforced across environments without the need for manual adjustments. This ensures that new regulatory requirements are consistently applied, keeping cloud environments aligned with the latest standards.
Integration with Existing Workflows
For compliance automation to succeed, it must integrate seamlessly into DevOps workflows. Tools like Checkov can be embedded into CI/CD pipelines in GitHub Actions, Jenkins, or similar systems so that scans run automatically during builds. Using reusable templates and modular workflows makes setup lightweight and repeatable. When compliance becomes part of the deployment process instead of a separate gate, it improves adoption and ensures coverage without slowing teams down.
Cloud compliance automation addresses complex and evolving regulatory needs, but challenges such as false positives, multi-cloud management, and developer adoption must be tackled head-on. Context-aware scanning, policy-as-code, centralized repositories, and pipeline integrations are the building blocks for effective adoption. With these strategies, compliance can evolve from a manual, error-prone task into a continuous safeguard that strengthens security and reduces operational overhead. Now let’s walkthrough through how Firefly helps streamline cloud security compliance automation and offers solutions to these challenges.
Unified Compliance and Governance with Firefly
Firefly automates cloud security compliance by mapping your entire cloud environment to Infrastructure-as-Code (IaC) and continuously enforcing governance policies across AWS, Azure, GCP, and Kubernetes. Instead of relying on manual audits or point-in-time checks, Firefly ensures continuous compliance by integrating directly into your CI/CD pipelines and existing DevOps workflows.
Cloud compliance isn’t just about one-time checks; it must be enforced both during infrastructure deployment and after it goes live in production. Firefly unifies both stages into a single compliance framework that follows resources across their entire lifecycle.
Compliance During Deployment
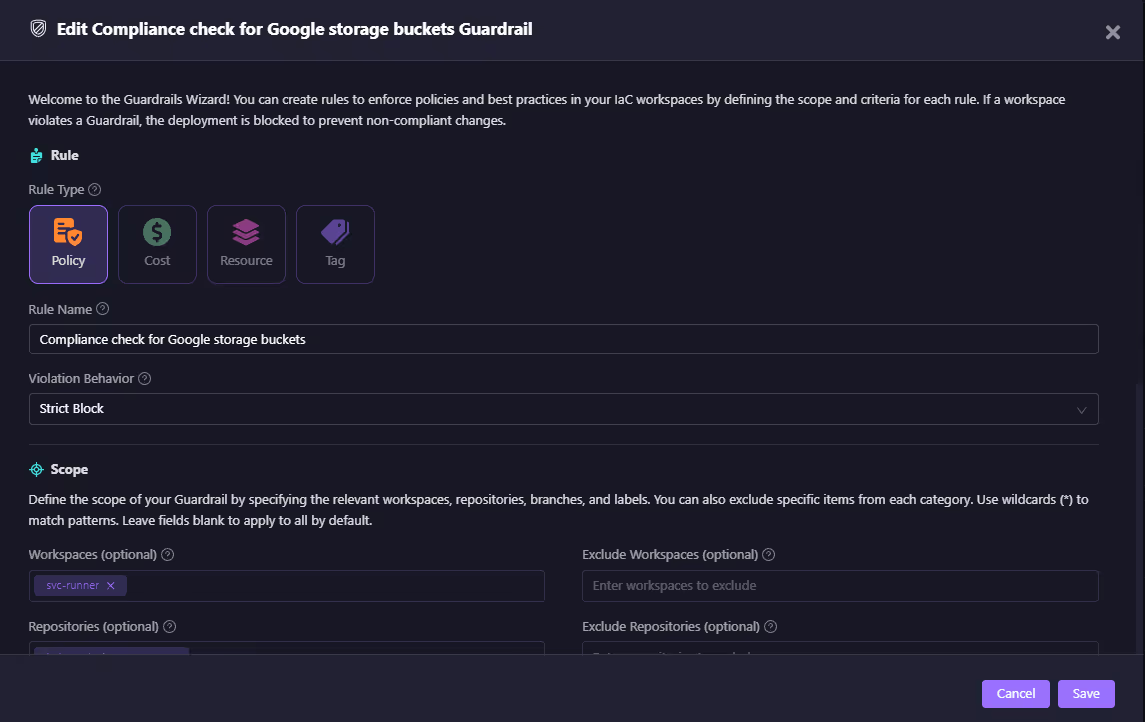
When you deploy infrastructure with Firefly Runners, you can attach Guardrails that enforce security and compliance policies in real time. If a violation is detected, the Runner blocks the deployment before misconfigured resources ever go live.
Example: In the screenshot below, a Guardrail called “Compliance check for Google Storage Buckets” prevents the creation of a bucket that doesn’t meet compliance standards:
The deployment is halted, and developers see exactly which policies were violated, along with remediation options as shown in the snapshot below:
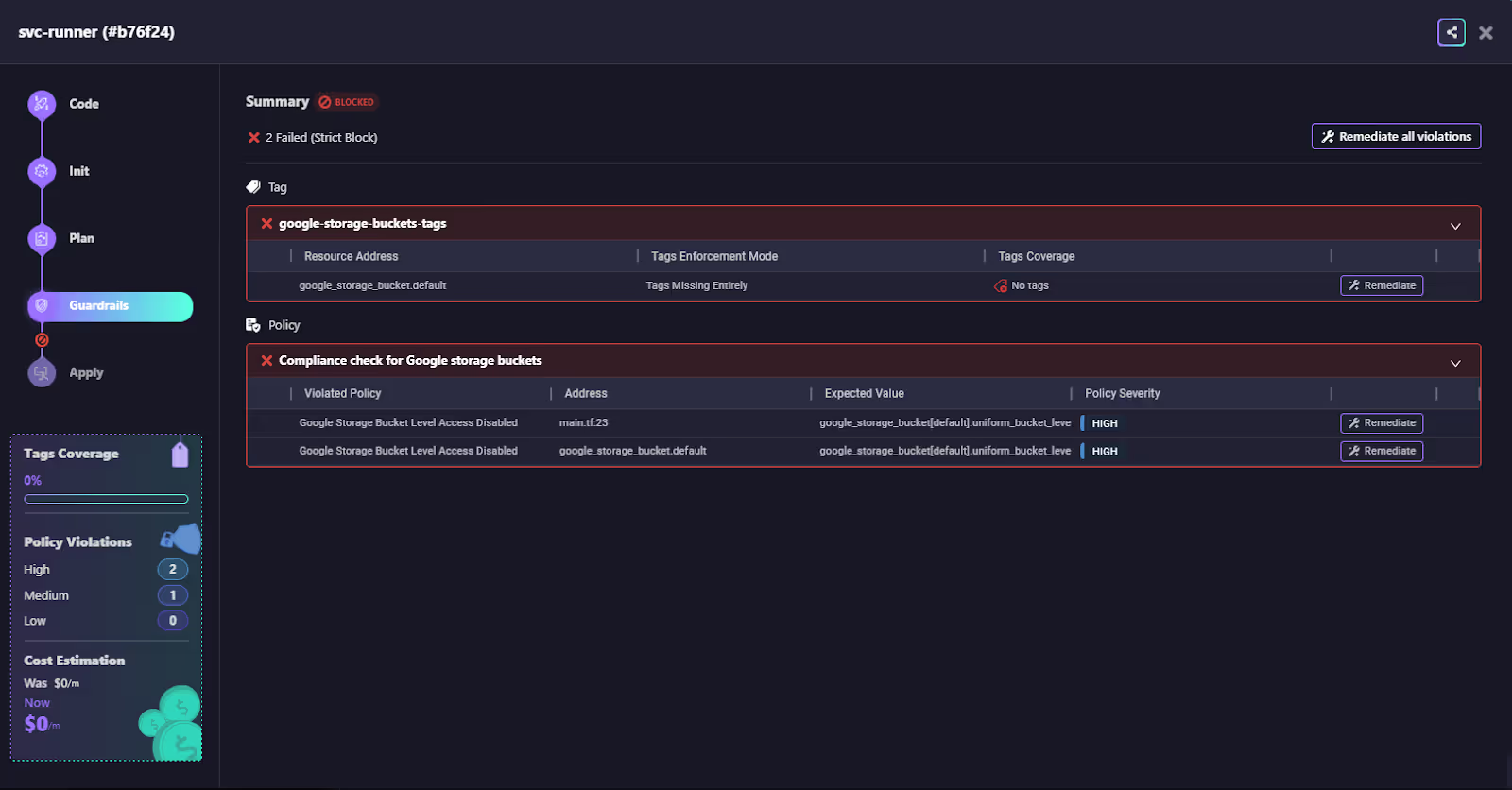
This makes Firefly more than a passive scanner; it’s an active enforcement layer, ensuring compliance is applied at the provisioning stage instead of only after the fact.
Compliance After Deployment (Runtime)
Once resources are live, Firefly continues monitoring them to catch drift, manual changes, or newly introduced violations. This ensures compliance is not a one-off gate but a continuous process.
Granular Policy Enforcement with Real-Time Visibility
When a compliance policy is triggered (e.g., “Google Cloud Storage Bucket Logging Not Enabled”), Firefly doesn’t just raise a generic alert. It surfaces detailed, actionable insights, including:
- Policy description (what the rule enforces).
- Affected asset types and data sources.
- Severity classification (Info, Medium, High, Critical).
- The actual Rego policy logic ensures transparency and auditability.
Here’s a snapshot of Firefly’s Governance Dashboard, which lists all the active compliance packs and policies. Each policy is shown with its severity level, violating assets, compliance percentage, and available remediation options.
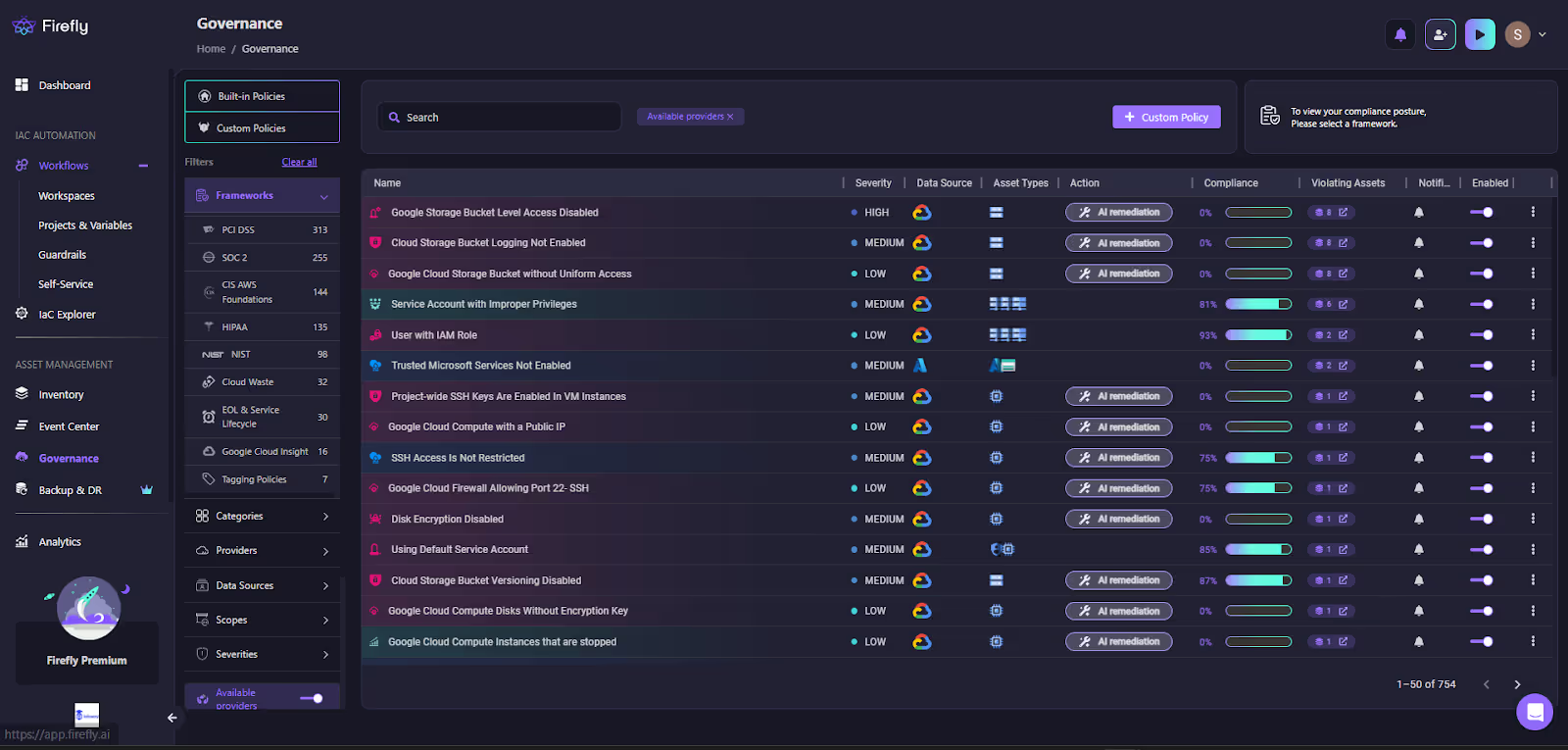
The above Firefly Governance Dashboard displays compliance policies across GCP, AWS, and Azure, along with their severity and compliance percentage. In addition to flagging violations, Firefly provides:
- AI-powered remediation suggestions, so issues can be fixed instantly.
- Workflow integrations (e.g., Jira tickets, GitHub pull requests) enable remediation to become part of the development lifecycle.
Resource-Level Compliance Monitoring
Selecting a violating asset opens a detailed Inventory View, showing every affected resource under that policy, as shown in the snapshot below:
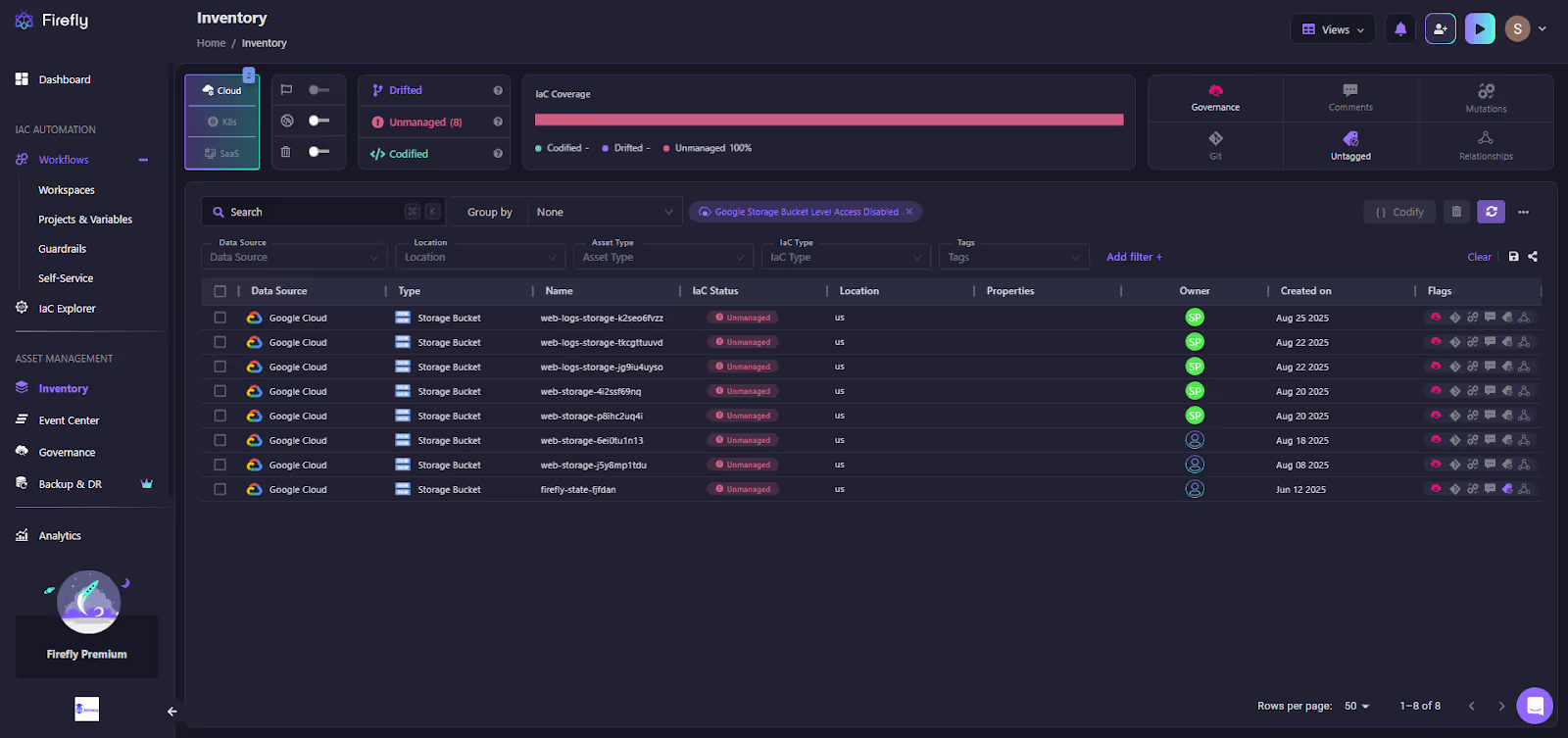
For example: “Google Cloud Storage Buckets without Uniform Access.” Each flagged resource is enriched with:
- IaC status (Codified, Drifted, or Unmanaged).
- Owner attribution.
- Creation date and region.
- Other compliance/security policies the resource violates.
This turns Firefly into more than just a compliance engine; it acts like a Cloud Security Posture Management (CSPM) solution, continuously monitoring resources at a granular level while connecting policy violations back to ownership and IaC coverage.
With Firefly, compliance is no longer a fragmented process spread across multiple tools and manual efforts. Instead, it is a seamless and continuous process that integrates directly into your workflows. Firefly makes compliance:
- Preventive: It acts as a guardrail, blocking misconfigurations during deployment to ensure security and compliance before any changes go live.
- Detective: Continuous runtime scanning monitors for drift and new violations, ensuring compliance is upheld in real-time as your infrastructure evolves.
- Corrective: Powered by AI, Firefly provides automated remediation, integrating directly into developer workflows to quickly resolve compliance issues without manual intervention.
This approach ensures that your compliance posture is not just a "snapshot in time," but a dynamic, enforceable process that spans both your code and cloud environments.
FAQs
1. What is Compliance Automation?
Compliance automation uses tools and processes to continuously enforce security, regulatory, and industry standards across cloud resources, reducing manual effort and ensuring adherence throughout the infrastructure lifecycle.
2. What is GRC Automation?
GRC (Governance, Risk, and Compliance) automation integrates policy enforcement, risk management, and regulatory monitoring into automated workflows, ensuring consistent compliance and reducing operational risk.
3. What is AWS Cloud Compliance?
AWS cloud compliance ensures that AWS resources meet regulatory and security standards like SOC 2, PCI DSS, HIPAA, and GDPR, using automated controls, monitoring, and reporting tools.
4. What is Compliance in Cloud Security?
Compliance in cloud security means continuously enforcing security policies and regulatory requirements across cloud environments, including access controls, encryption, and auditing, to maintain a secure and compliant infrastructure.





.svg)









