You log into an AWS account and it’s full of EC2 instances, S3 buckets, RDS clusters, and load balancers. Nobody on the team can tell you who owns what or why half of them exist. The bill keeps rising, but there’s no way to map spending to teams or projects.
I came across a Reddit thread where an engineer inherited a small AWS setup managed in Terraform. His first question: “How do I tag everything with Note=Created and maintained by Terraform without editing every single resource?” That’s the right instinct. Even in a small environment, tagging gaps turn into wasted time and money. At scale, they make cost reporting, compliance checks, and incident response almost impossible.
The core issue isn’t the lack of tags themselves, it’s the lack of a tagging framework and enforcement. Without standards, tags are inconsistent or missing altogether. One team uses Env=prod, another uses Environment=Production. Automation breaks. Finance can’t allocate costs. Security can’t scope policies.
Tagging isn’t cosmetic. It’s the baseline for cost control, governance, and automation in cloud environments. If you skip it, you’re operating blind.
What is Cloud Tagging?
A tag is metadata you attach to a resource. It’s always a key-value pair: environment=prod, owner=team-a, cost-center=finance. Tags don’t affect how the resource runs, but they decide how you track spend, enforce policies, and automate operations.
Where Tagging Goes Wrong
- Case sensitivity: On most platforms, keys are case-insensitive, but values are case-sensitive. That means Environment=Prod and environment=prod look similar in the console but are stored differently. This breaks cost reports and automation jobs. Pick a convention, usually lowercase keys, normalized values, and enforce it.
- Not a substitute for naming: Names guarantee uniqueness (prod-payments-db-01), tags classify (environment=prod, application=payments). Both serve different purposes, and you need both.
The Downsides of a Poor Tagging Strategy
A weak or inconsistent tagging strategy doesn’t just make things messy; it creates real financial, operational, security, and compliance problems that scale with your cloud footprint.
- Wasted cloud spend: Without consistent tags, orphaned or idle resources stay invisible. Unused test VMs, forgotten snapshots, or old load balancers keep running with no owner tied to them. These resources quietly inflate costs that could have been flagged instantly if they carried owner or environment tags.
- Inaccurate cost allocation: If one team uses Env=prod, another uses environment=production, and a third doesn’t tag at all, Finance has no way to split the bill accurately. Showback and chargeback models collapse, budgets become guesswork, and forecasting future spend is nearly impossible.
- Operational inefficiency: When tags are missing, engineers end up grepping through consoles and CLI outputs to figure out what a resource does or who owns it. That manual hunt slows down troubleshooting, patching, and decommissioning. In large environments, it also creates inconsistent “fixes” that make automation harder to trust.
- Multi-cloud complications: Each provider handles tagging differently — AWS allows 50 tags per resource and only activated ones show up in Cost Explorer, Azure has inconsistent limits across services, and GCP splits between legacy labels and the newer IAM-integrated tags. Without a cross-cloud tagging framework, you can’t get a unified view of cost or compliance.
- Automation failures: Infrastructure automation assumes good tags. Auto-scaling groups, backup jobs, scheduled shutdowns, and monitoring dashboards all filter on tags like environment=dev or backup=daily. If those aren’t consistent, automation silently skips resources, leaving them unmanaged.
- Security blind spots: Untagged resources mean unknown resources. A public-facing bucket or VM without owner or environment tags may sit unnoticed until it becomes an entry point for attackers. Security teams can’t enforce IAM policies or ABAC conditions without reliable metadata to scope access.
- Compliance risks: In regulated environments, auditors will ask: Which assets store PII? Which systems fall under PCI? If data-classification or compliance tags aren’t present, the only fallback is a manual audit, time-consuming, error-prone, and potentially leading to fines.
- Loss of accountability: Without owner tags, there’s no traceable responsibility for a resource. Incidents drag on because no one knows who to page. Long term, this creates “shadow IT”, unapproved resources that bypass governance entirely.
- Data exposure through tags: Tags themselves can be a liability. Because they’re stored in APIs, billing exports, and logs, placing sensitive data (like customer names or PII) in a tag leaks that data far wider than intended.
All of these issues point to one conclusion: without a structured tagging strategy, cloud resources quickly turn into an unmanageable sprawl. To avoid that chaos, tags need to be applied consistently and used as the organizing layer for cost, compliance, and operations. This is where a strong tagging framework shows its value.
How Tags Keep Cloud Resources Organized
Tagging is not about making the console look neat. In production, tags are the only way to connect cloud resources to cost, compliance, and operations.
Cost allocation
Cloud bills without tags are just totals. With tags like cost-center=finance or project=payments, you can break spending down by team, environment, or business unit. On AWS, you must activate those tags as cost allocation tags before they show up in Cost Explorer or Budgets. GCP tags and labels can be exported to BigQuery for the same purpose. Azure Cost Management depends on tags to report across subscriptions. Without them, Finance has no way to map spend back to owners.
Compliance and audits
Auditors will ask, “Which resources store PII?” or “Which databases are in PCI scope?” If you tag resources with data-classification=pii or compliance=pci, you can pull that list immediately. In Azure, you can use Policy to enforce that every storage account has a data-classification tag. On AWS, SCPs can block resource creation unless required compliance tags are present.
Security enforcement
Tags tie directly into IAM. On AWS, you can write policies like: allow users to manage only resources tagged with environment=dev. On GCP, tags integrate with IAM Conditions so you can scope permissions to specific tag values. This is how attribute-based access control (ABAC) is implemented in practice.
Automation
Operational automation needs a selector. Tags provide it.
- Backup jobs can run against all resources tagged backup=daily.
- Lifecycle policies can delete objects with retention=30d.
- Lambda or Functions can stop VMs tagged with schedule=off-hours.
Azure specifically recommends tagging patch windows (patch-window=sunday-02:00) so updates can run consistently across fleets.
Incident response
During an outage, you don’t want to parse every alert in the system. If resources and metrics are tagged with application=payments-api, you can immediately filter to the impacted scope. Without tags, you’re sifting through noise.
Governance and reporting
Cloud providers all emphasize tag governance:
- AWS has dashboards and Config rules to report untagged resources.
- Azure Policy can append or block resources missing tags.
- GCP tags inherit down the org/folder/project hierarchy, giving a complete picture when you query at the org level.
This lets you measure coverage of mandatory tags (owner, environment, cost-center) and enforce standards automatically.
Building a Tagging Strategy
A tagging strategy is a binding contract. If every team makes up its own keys and values, the whole system breaks. You’ll never get consistent cost reports, automation will miss resources, and security policies won’t line up. The only way tagging works at scale is if the rules are written down, agreed on, and enforced in code.
Get all the right teams in the room
- FinOps cares about cost-center and department tags. These have to be activated as cost allocation tags in AWS so they show in Cost Explorer/Budgets. On GCP, they need to appear in billing exports to BigQuery.
- DevOps/Engineering knows what automation depends on. Example: backups triggered by backup=daily, off-hours shutdown by schedule=off-hours. They also need tags wired into Terraform/CloudFormation/ARM so they’re applied by default.
- SecOps needs tags like data-classification=pii or sensitivity=high so IAM conditions and org policies can scope access. On GCP, those tags integrate with IAM Conditions; on AWS, you can enforce them with aws:ResourceTag.
- Compliance defines tags like compliance=pci so auditors can pull in-scope resources without manual searches.
Mandatory vs Optional Tags
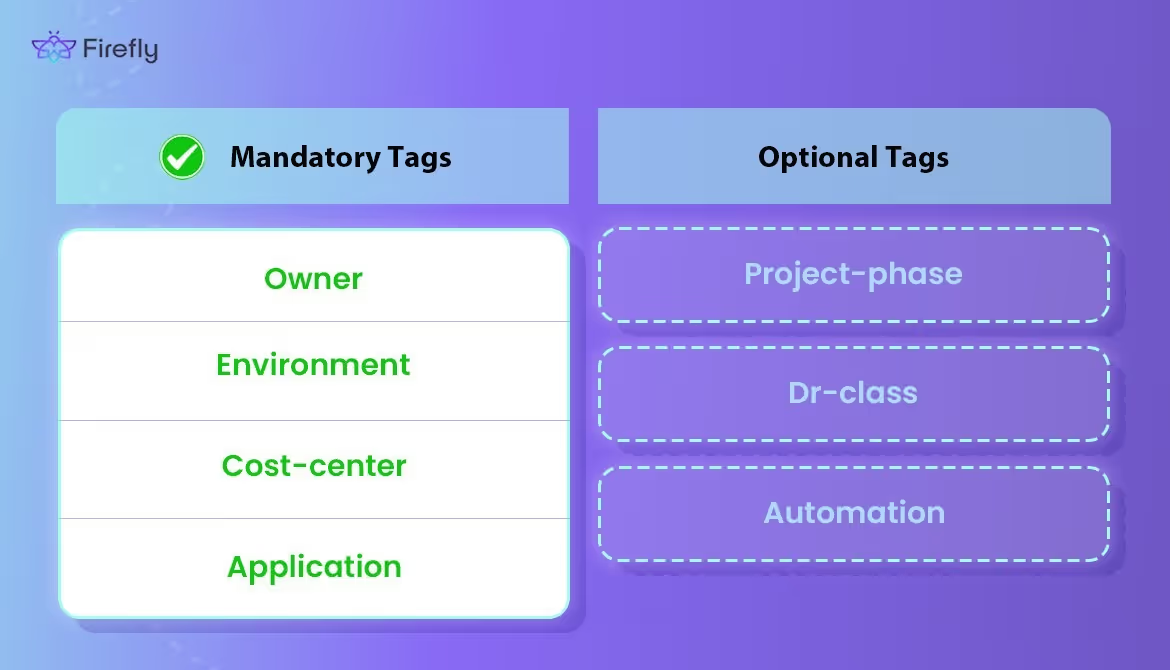
Keep the core set small and universal, then let teams extend.
- Mandatory (every resource, no exceptions):
- owner: team email/DL. If this is missing, you won’t know who to call when an EC2 is burning money.
- environment: dev, staging, prod. Needed for IAM, automation, and cost splits.
- cost-center: billing code or finance unit. Without this, Finance can’t charge back.
- application: service name or ID. Let's you map costs and incidents back to systems.
- Optional (when needed):
- project-phase: discovery, rollout, retired.
- dr-class: primary, standby.
- automation: markers like backup=daily or schedule=off-hours.
Enforce ownership and consistency
- AWS: Tag Policies + SCPs + IAM condition keys (aws:RequestTag, aws:TagKeys). Block resource creation if required tags are missing. Use Config rules or Lambda to backfill drift.
- Azure: Azure Policy with modify effect can auto-append missing tags or block non-compliant resources.
- GCP: Define tag keys/values at org/folder level. Bind them with tagUser/tagAdmin roles. Remember: one resource can have max 50 tag bindings.
Keep a Tag Dictionary
Publish one source of truth: a list of approved keys, allowed values, casing rules, and examples. Example: environment must be exactly dev|staging|prod (lowercase). No “Prod”, no “production”. AWS explicitly calls this out: inconsistent casing kills reports.
Tied directly to business outcomes
Don’t tag for the sake of it. Every tag must drive cost, security, or ops:
- cost-center → budget tracking and showback.
- data-classification → enforce encryption + restricted IAM.
- owner + application → point to the team on call during incidents.
- environment + automation → enable lifecycle jobs, patch cycles, shutdown schedules.
Start small, then scale
Begin with the four mandatory keys, enforce them in non-prod first, then expand. AWS guidance is clear: don’t over-engineer on day one; tag what gives you immediate visibility and control, then iterate.
Designing a Tagging Framework
A tagging strategy says what keys are required; a tagging framework defines how they’re structured, validated, and enforced across clouds. Without a framework, drift creeps in, different spellings, inconsistent values, and tags that automation can’t use.
Categorize tags for clarity
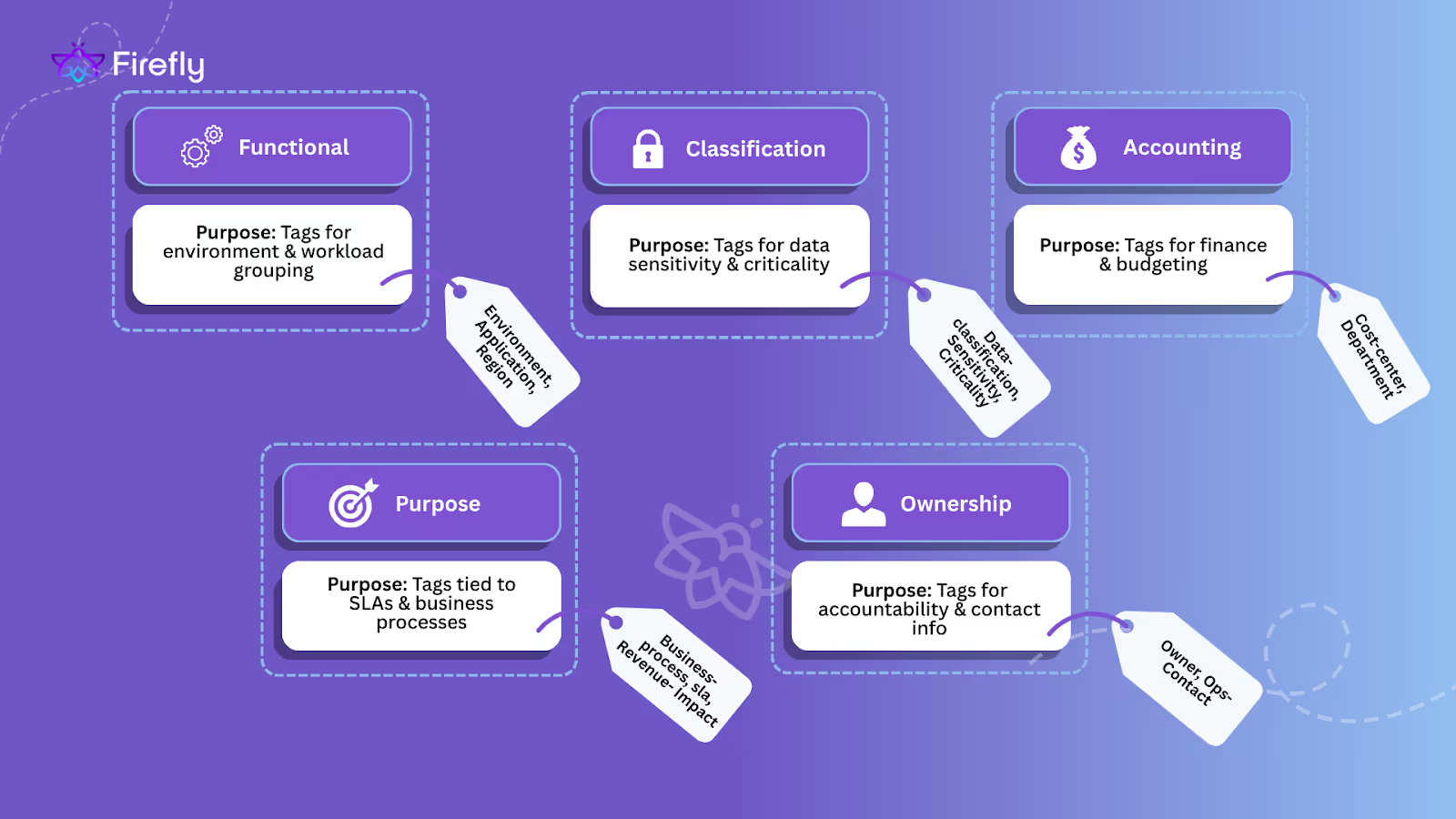
Microsoft’s guidance groups are tagged into five categories that scale well in practice:
- Functional: environment, application, region
- Classification: data-classification, sensitivity, criticality
- Accounting: cost-center, department
- Purpose: business-process, sla, revenue-impact
- Ownership: owner, ops-contact
This structure forces each tag to serve a clear purpose instead of ending up with random “misc” metadata.
Define key formats and casing rules
- Keys should be lowercase with hyphens (cost-center, dr-class).
- Values should be short and normalized (dev, staging, prod) instead of free text.
- Ambiguous spellings must be banned (production vs prod), with one standard documented and enforced.
Enforce allowed values
Framework rules are only useful if they are checked automatically. For example:
- environment must be one of [dev, staging, prod].
- dr-class only [primary, secondary, standby].
- data-classification should be [public, internal, confidential, pii].
Cloud providers offer enforcement tools: AWS Tag Policies, Azure Policy with allowed values, and GCP’s centrally defined tag keys that reject invalid inputs. Terraform can also embed validation directly in modules, ensuring that a plan fails before resources are created.
Validating Tags with Terraform
In this setup, the Terraform configuration provisions two Google Cloud resources:
- A Compute Engine instance (from the compute_instance module), which enforces labels such as environment and usage.
- A Cloud Storage bucket (from the gcs_bucket module), which applies the same labeling rules.
Both modules declare environment as a required label with allowed values [dev, pre-prod, prod]. The plan fails if anything outside this set is passed in.
Here’s the execution of terraform plan with a tags.tfvars file where the environment is set to "stage":
❯ terraform init -upgrade && terraform plan -var-file="tags.tfvars"
Initializing the backend...
Upgrading modules...
- compute_instance in modules\compute_instance
- gcs_bucket in modules\gcs_bucket
Initializing provider plugins...
- Finding hashicorp/google versions matching ">= 5.0.0"...
- Finding hashicorp/random versions matching ">= 3.5.0"...
- Using previously-installed hashicorp/google v6.49.2
- Using previously-installed hashicorp/random v3.7.2
Terraform has been successfully initialized!
Terraform used the selected providers to generate the following
execution plan. Resource actions are indicated with the
following symbols:
+ create
Terraform planned the following actions, but then encountered a problem:
# random_string.suffix will be created
+ resource "random_string" "suffix" {
+ id = (known after apply)
+ length = 5
+ lower = true
+ number = true
+ numeric = true
+ special = false
+ upper = false
}
Plan: 1 to add, 0 to change, 0 to destroy.
╷
│ Error: Invalid value for variable
│
│ on tags.tfvars line 3:
│ 3: environment = "stage"
│ ├────────────────
│ │ var.environment is "stage"
│
│ environment must be one of: dev, pre-prod, prod.
│
│ This was checked by the validation rule at
│ variables.tf:35,3-13.
╵The plan halts immediately because the tag framework rule is violated. Once corrected to a valid value like pre-prod, the plan runs successfully and applies consistent labels to both the VM and the bucket. This is how framework rules move from documentation into real enforcement; bad tags never make it into production.
Maintain a Tag Dictionary
A framework must be backed by a single source of truth that lists:
- Keys, descriptions, allowed values, and examples.
- Ownership of each tag (who defines and maintains it).
- Update the change history whenever tags are added, renamed, or deprecated.
This dictionary should be version-controlled in Git and referenced by both policies and IaC modules. It acts as the long-term guardrail that keeps tagging standards consistent and auditable.
Operationalizing Tagging
A tagging standard only works if it’s treated as part of day-to-day operations. Tags are the one piece of metadata you can always rely on; they show up in the console, APIs, billing exports, and monitoring tools. Unlike a CMDB (Configuration Management Database, e.g., ServiceNow, BMC Atrium), which can drift out of sync with reality, tags stay attached to the resource itself.
Tag everything that can be tagged
Servers are the obvious starting point, but you also need to tag networks, load balancers, queues, disks, snapshots, images, endpoints, and anything that supports tags. When untagged resources slip through, they turn into blind spots for cost, monitoring, or cleanup.
Keep compliance and traceability built in
Certain tags are non-negotiable in production:
- owner: team distribution list or service account (not a personal email). This makes hand-offs and incident response clean.
- billing / cost-center: code or contract ID that Finance uses to allocate spend.
- source: which system created it (Terraform, GitHub Action, custom deploy job).
- state-ref: where its state or pipeline lives (S3 bucket, repo name).
- expires: date when temporary resources should be removed, or never for production.
With these in place, you don’t waste hours figuring out who owns a resource, how it was created, or whether it should still exist.
Automate audits and reconciliation
- Use AWS Config, Azure Policy compliance, or GCP Asset Inventory to surface missing or invalid tags.
- Run scheduled jobs to normalize casing (Prod → prod) and backfill defaults (expires=never for prod).
- Quarantine or flag resources missing mandatory tags instead of allowing them to sit unnoticed.
Standardize key formats and values
- Lowercase keys, no spaces or punctuation.
- Controlled values for common tags (environment=dev|staging|prod).
- Document everything in a central Tag Dictionary and enforce it through IaC and policies.
Integrate with monitoring and automation
Most observability tools (Datadog, CloudWatch, Azure Monitor) use tags as their primary filter. Correct tags mean new servers appear automatically in dashboards and alert groups. Incorrect tags mean blind spots or alert noise. Similarly, backup jobs, patch schedules, and shutdown policies all rely on consistent tag filters.
Continuous review
A tag schema is never done. New compliance rules, new projects, and new automation use cases will demand new keys. Review the dictionary quarterly, prune unused tags, and update enforcement policies to match.
Real-World Use Cases
Tags are only useful if they solve problems. In practice, they’re the backbone for cost tracking, compliance, automation, and security.
Cost management (FinOps)
- Cost allocation → A tag like cost-center=marketing or project=crm-migration lets Finance break down the AWS or Azure bill by project or department instead of one giant number.
- Budgeting & forecasting → Historical spend grouped by application or team makes it possible to build accurate budgets and spot trends.
- Cost optimization → If environment=test is applied consistently, it’s easy to target all test workloads for nightly shutdown to cut costs.
- Showback/chargeback → Activating cost-center tags in billing systems means Finance can send each team a usage report or even bill them internally. That drives accountability.
Governance and compliance
- Regulatory compliance → Tags like compliance=hipaa or data-classification=pii identify resources that must have encryption, restricted IAM policies, or audit logging.
- Auditing → An owner tag with a team email gives auditors an immediate point of contact. Without it, you end up doing mass emails asking, “Who owns this VM?”
- Policy enforcement → Cloud policies can block any resource missing required tags. For example, block creation of a environment=production VM unless it also has backup=enabled.
Automation and operations
- CI/CD pipelines → Terraform default_tags, CloudFormation stack-level tags, and Azure ARM template tags ensure new resources are born compliant.
- Lifecycle management → A retention-period=30d tag can trigger cleanup scripts to delete temporary buckets or instances automatically.
- Monitoring and alerting → Datadog, CloudWatch, and Azure Monitor all use tags to group resources. A tag like team=data-engineering routes alerts to the right Slack channel.
- Resource grouping → Ops can patch or back up everything tagged application=payments and environment=staging with a single query, instead of managing resources one by one.
Security and access control
- ABAC (Attribute-Based Access Control) → AWS IAM or GCP IAM Conditions can grant developers access only to environment=dev resources. They never see prod by default.
- Security posture → Adding criticality=high or confidentiality=internal lets SecOps target high-risk resources for extra scans, stricter firewall rules, or more frequent backups.
Incident response
When an alert fires on i-0a12b3c4d5, tags give you the context instantly:
- environment=prod
- application=payments-api
- owner=payments-team@company.com
Now you know what’s broken, where it runs, and who’s on call, no guesswork.
Disaster recovery
A quick query for dr-class=primary and region=us-east-1 shows which databases or clusters don’t have a secondary copy in another region. That kind of gap is much cheaper to catch in advance than during an actual failover.
How Firefly Helps With Cloud Tagging
A tagging framework only works if it’s enforced. Firefly enforces tag policies in two critical phases: during deployment and after deployment.
Tagging Policies During Deployment
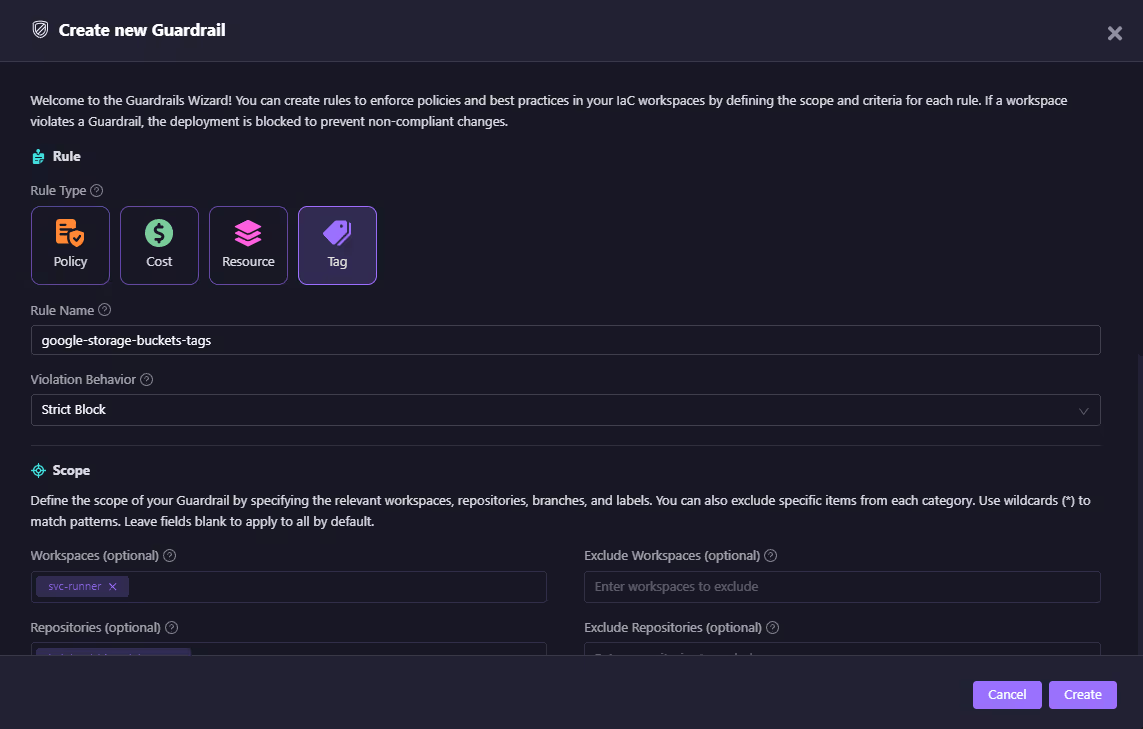
Firefly guardrails plug into Terraform and other IaC pipelines to stop non-compliant resources before they ever reach production. For example, a Google Storage bucket without mandatory tags will fail at the plan stage, and the developer gets immediate feedback.
In the snapshot below, a guardrail is being created that enforces tags on Google Storage buckets. The violation behavior is set to Strict Block, meaning the pipeline run will be rejected if tags are missing.
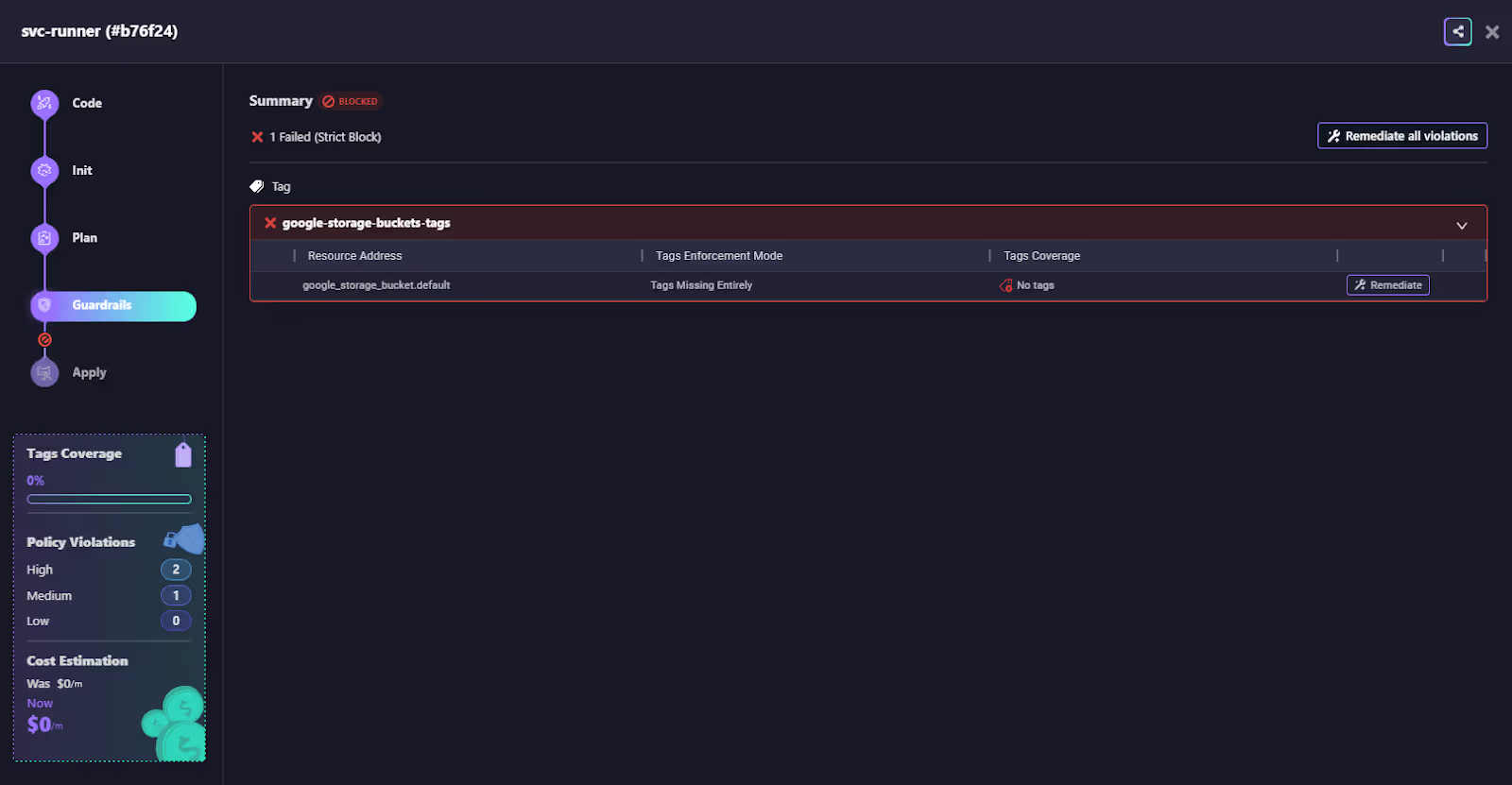
When the pipeline is deployed using the Firefly runner, the guardrail runs during the plan step. Here, the deployment is blocked because the storage bucket resource had no tags attached. The violation details highlight the exact resource and the reason: Tags Missing Entirely.
Firefly also sends notifications to Slack so teams know immediately why a deployment failed. The message shows the number of resources changed, the severity of violations, and tag coverage for the run.
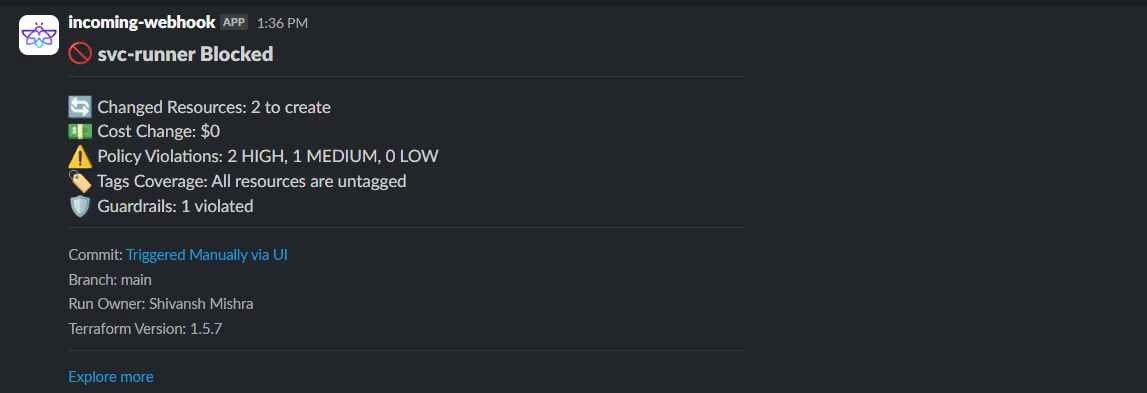
This workflow ensures that missing tags never make it past the CI/CD pipeline.
Tagging Policies After Deployment
Even with strong guardrails in CI/CD, some resources get created outside the pipeline through the console, scripts, or third-party tools. Firefly’s Governance Dashboard continuously scans cloud and SaaS accounts to detect those untagged or mis-tagged resources and brings them under control.
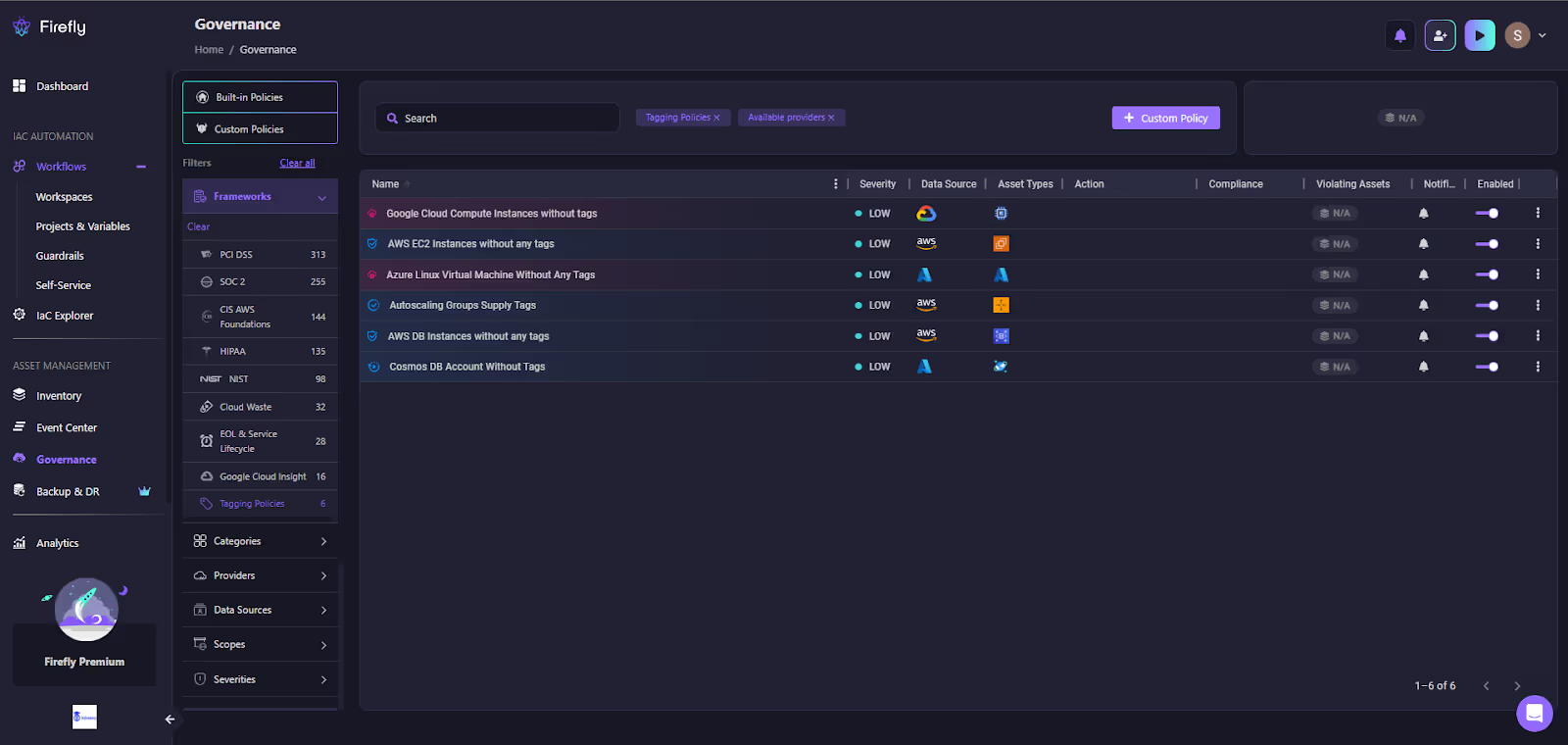
In the snapshot above, the Governance Dashboard shows a list of built-in and custom tagging policies applied across AWS, Azure, and GCP. Each entry highlights:
- Policy name: e.g., AWS EC2 Instances without any tags, Google Cloud Compute Instances without tags.
- Severity: impact level (low/medium/high).
- Data source and asset type: the cloud provider and the resource type covered by the rule.
- Violating assets: how many resources currently fail the policy, with a link to drill down into the exact instances.
- Actions: remediate directly, trigger a pull request for an IaC fix, or run CLI commands on the cloud resource.
This view makes it clear, at a glance, which resources in production are drifting from the tagging framework. Engineers can filter policies by framework (CIS, HIPAA, PCI), provider, or severity to focus on what matters. From here, violations can be fixed in IaC repos via automated pull requests or patched directly in the cloud for unmanaged assets.
By this dashboard with pre-deployment guardrails, Firefly ensures tagging standards are enforced both when resources are created and while they’re running.
FAQs
How do Cloud Tags Work?
Cloud tags are key–value metadata pairs like environment=prod or owner=team-a that you attach to resources. They don’t affect runtime behavior but provide context that tools and policies use. Tags show up in billing, IAM, monitoring, and automation, making it possible to organize, filter, and enforce rules across instances, buckets, and databases.
What is a Tagging Strategy?
A tagging strategy is a documented, enforced standard for how tags are defined and applied. It specifies mandatory keys (owner, environment, cost-center), allowed values, and casing rules. The goal is consistency so tags can drive cost allocation, automation, compliance, and security policies without breaking due to drift or spelling differences.
What is Strategy Tagging in Finance?
In finance, tagging maps resources directly to budgets and projects. Tags like cost-center=marketing or project=crm-migration let finance split the cloud bill by department or initiative. This enables showback or chargeback models, improves forecasting, and ties real spend back to financial strategy instead of treating cloud usage as one lump expense.
Why is Tagging Important in Managing Cloud Instances?
Tags add the context that raw instance IDs don’t provide. With tags, instances can be grouped by environment, mapped to owners, tied to cost centers, and targeted by IAM or automation rules. This makes it possible to control spend, enforce compliance, route alerts, and run lifecycle operations like backups or scheduled shutdowns with precision.





.svg)









