TL;DR
- Cloud waste accounts for over 30% of enterprise cloud spend, according to estimates from Boston Consulting Group (BCG), due to idle or unmanaged resources across AWS, Azure, and GCP.
- Continuous FinOps moves cost control into CI/CD pipelines, where spend checks and policy enforcement happen before deployment.
- Firefly connects cloud accounts with IaC, giving teams real-time cost visibility, automated waste detection, and drift correction.
- Guardrails block cost overruns or policy violations directly in Terraform, GitHub Actions, or GitLab CI, ensuring every deployment stays within limits.
- Enterprises using Firefly achieve sustained cost savings and governance consistency across multi-cloud environments through automation, not manual reviews.
Cloud spending is growing faster than teams can control. Gartner estimates enterprise cloud costs will reach ~$723B by 2025, and BCG reports that ~30% of that spend is wasted due to idle or over-provisioned resources. With workloads spread across AWS, Azure, and GCP, every provider exposes billing differently, making it difficult to map resources back to teams or business units. Engineers end up managing thousands of resources with limited visibility into ownership or justification.
This pain is visible everywhere, even on X, where Aethir Cloud recently pointed out that “traditional cloud providers are becoming the biggest bottleneck for AI innovation,” citing AWS charging $4.30/hr for an H100 GPU while distributed networks offer the same for $1.49/hr. The takeaway isn’t just pricing, it’s the broken cloud economics model. Companies can’t wait for end-of-month billing reports anymore. Cost control is shifting into CI/CD pipelines through continuous FinOps and policy-driven automation, enforcing budgets, tags, and limits during provisioning instead of reacting after the bill arrives.
Where Cloud Cost Management Breaks Down
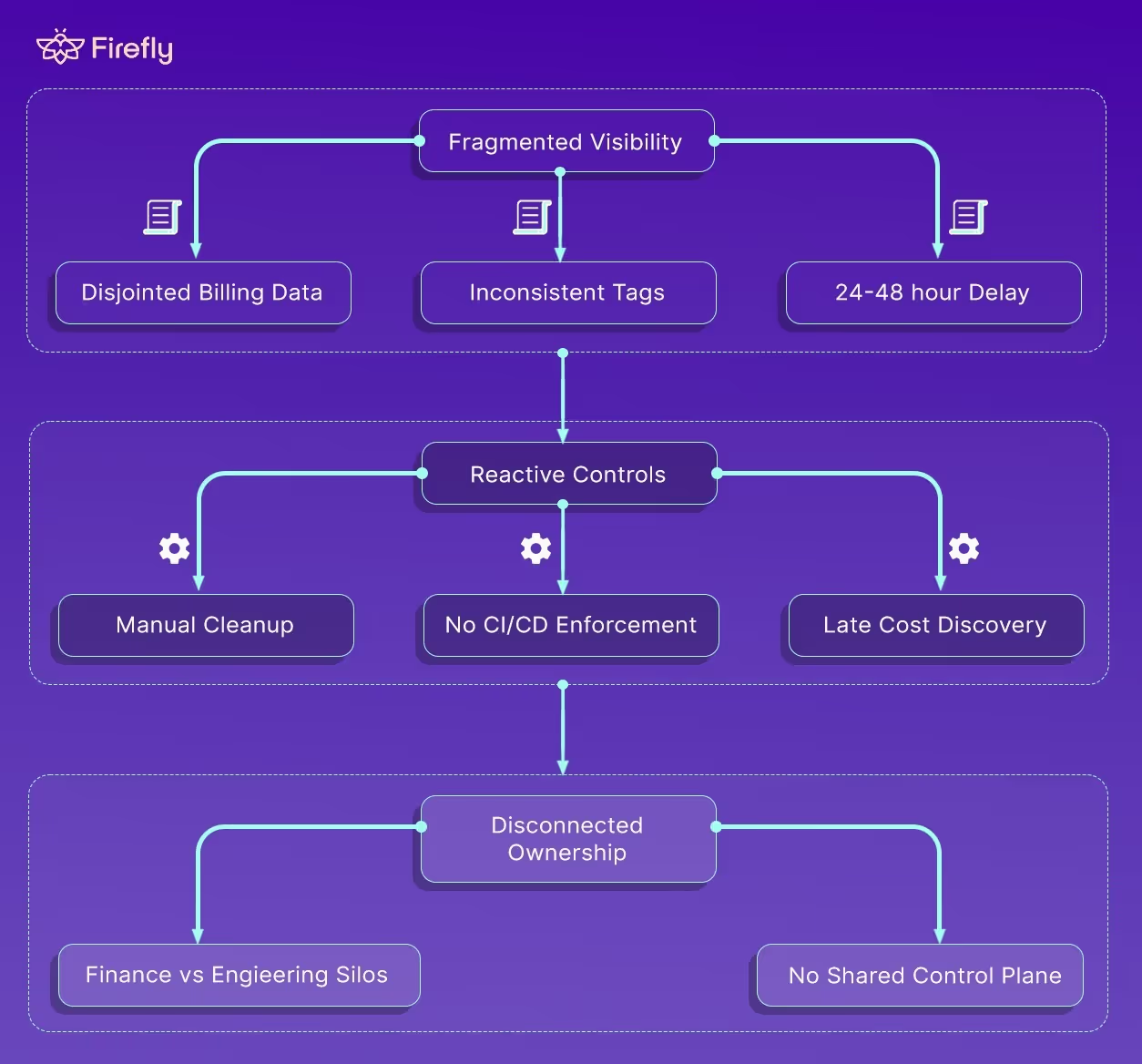
Every enterprise says it tracks cloud costs. Most actually chase them after the damage is done. The breakdown isn’t in awareness; it’s in the operational wiring.
Fragmented Visibility
Open any large cloud account and you’ll see the problem immediately. An EC2 instance tagged env=prod on AWS, a VM labeled Production in Azure, and a GCP Compute Engine with no tag at all three identical workloads, three different naming conventions, three billing identifiers.
Finance asks, “Which team owns these?” and engineering can’t answer without three separate API calls, a few CSV exports, and manual joins in a spreadsheet.
AWS gives you hourly cost data through Cost Explorer or CUR exports, Azure pushes daily summaries through its Cost Management API, and GCP delivers cost tables through BigQuery export, all with different field structures and timestamp formats.
By the time you normalize them into a single dataset, the data is at least 24–48 hours old. Any decision based on that is already reactive. Engineers provisioning new workloads today are effectively blind to yesterday’s cost impact.
Reactive Controls
Most cost controls live in Confluence pages or monthly cleanup scripts. Let's suppose someone spins up a p4d.24xlarge instance for a benchmark, forgets it, and the next finance report shows a surprise $12K spike. Then comes the Slack thread: “Who launched this?”, followed by three days of blame-hunting.
Tagging policies exist, but no one enforces them at deploy time. CI/CD pipelines rarely validate costs before applying infrastructure changes. At best, there’s a “budget review” after the invoice. By then, the spend is already booked and can’t be clawed back.
Infrastructure doesn’t drift overnight; it drifts in silence. Idle EBS volumes, unattached IPs, orphaned snapshots, all invisible until someone audits manually. That’s why “cost reviews” often turn into post-mortems instead of preventive controls.
Disconnected Ownership
Finance operates on budgets and forecasts; engineering operates on pipelines and SLAs. The gap between those two is where cost governance dies.
Example: Finance sets a quarterly budget for $250K in compute spend. Engineering scales test clusters to meet a load requirement. Both are technically correct, yet neither has visibility into the other’s data in real time.
Without a unified control plane that ties infrastructure changes to budget constraints, cost discipline depends entirely on tribal knowledge. Some teams build internal scripts to sync tagging with cost centers, others try to enforce naming conventions in Terraform, but these are local fixes, not systemic ones.
Over time, this disconnect manifests as drifted infrastructure, resources that don’t match declared IaC, environments that outlive their projects, and expenses that no one owns.
Moving Toward Continuous FinOps
Dashboards and monthly reports don’t control costs; they only describe what’s already happened. Real control begins when cost awareness becomes part of the deployment process itself. That’s the idea behind Continuous FinOps: treating cost, compliance, and governance as part of infrastructure automation, not after-the-fact finance.
Continuous FinOps connects finance and engineering at runtime. Every resource defined in code is evaluated against policy before it reaches the cloud, shifting cost visibility left into CI/CD without slowing delivery.
Enterprise Example: Prudential Financial
This shift is already visible in mature organizations like Prudential Financial. The 150-year-old company began its cloud journey in 2018 to accelerate innovation. Early successes, faster time-to-value, and flexible cost models soon led to scale. Cloud spend grew from $4 million in the first year to $50 million by 2024, prompting a new question: How do we ensure value for every dollar?
In 2021, Prudential established a dedicated FinOps function built around four capabilities: waste management, purchasing management, consumption management, and cost-aware architecture. Teams adopted developer-centric tools like starter kits, automated alerts, and a self-service Pricing Bot that surfaced real-time cost estimates at design time. This integration of cost data into engineering workflows delivered more than 21 % annual cost avoidance and embedded cost awareness into the company’s cloud DNA.
Core Principles of Continuous FinOps
The Prudential case reflects the three principles every Continuous FinOps model rests on:
- Visibility: Unified, well-tagged inventories make every resource discoverable and attributable.
- Optimization: Automation identifies and remediates idle or mis-sized assets before they waste spend
- Operation: Policies live as code, versioned, reviewed, and enforced within CI/CD alongside infrastructure code.
Together, these ensure teams discover, optimize, and operate through code, embedding cost control where work actually happens.
Policy-as-Code: The Enabler
Policy engines such as OPA, Sentinel, and Infracost operationalize these principles. They evaluate every change at commit or merge time, automatically comparing estimated costs and compliance rules. When a change breaches a defined threshold, the CI/CD pipeline provides instant feedback, no waiting for finance reports or manual reviews.
This “budget-aware automation” is how organizations like Prudential have turned FinOps from a reporting exercise into an engineering discipline, ensuring that every deployment is both fast and financially disciplined.
Operationalizing Continuous FinOps with Firefly
FinOps produces real results only when cost checks, policy enforcement, and cleanup happen automatically, right inside deployment pipelines. Firefly connects to your cloud accounts and infrastructure-as-code to bring that automation directly into your existing DevOps workflow.
Resource-Level Cost Visibility
Firefly surfaces cost data at the resource level, showing estimated monthly spend for each provisioned resource, whether it’s an EC2 instance, an Azure VM, or a GCP disk. That context makes it easy to spot expensive or oversized components before deployment.
Each codified resource in Firefly is linked to its configuration, owner, and environment. When you open a workload, you immediately see how much it costs, which service it belongs to, and whether it aligns with tagging or budget policies.
For teams running across AWS, Azure, GCP, or Kubernetes, Firefly normalizes billing data into one consistent schema. This eliminates the need for manual reconciliation between different cloud cost models.
In the Firefly Governance dashboard shown below, each policy row represents a real-time cost or optimization rule, such as overprovisioned compute instances, unattached volumes, or unused load balancers, mapped across multiple providers. The view combines visibility, severity, and compliance on a single screen, so engineers can identify and act on inefficiencies immediately:
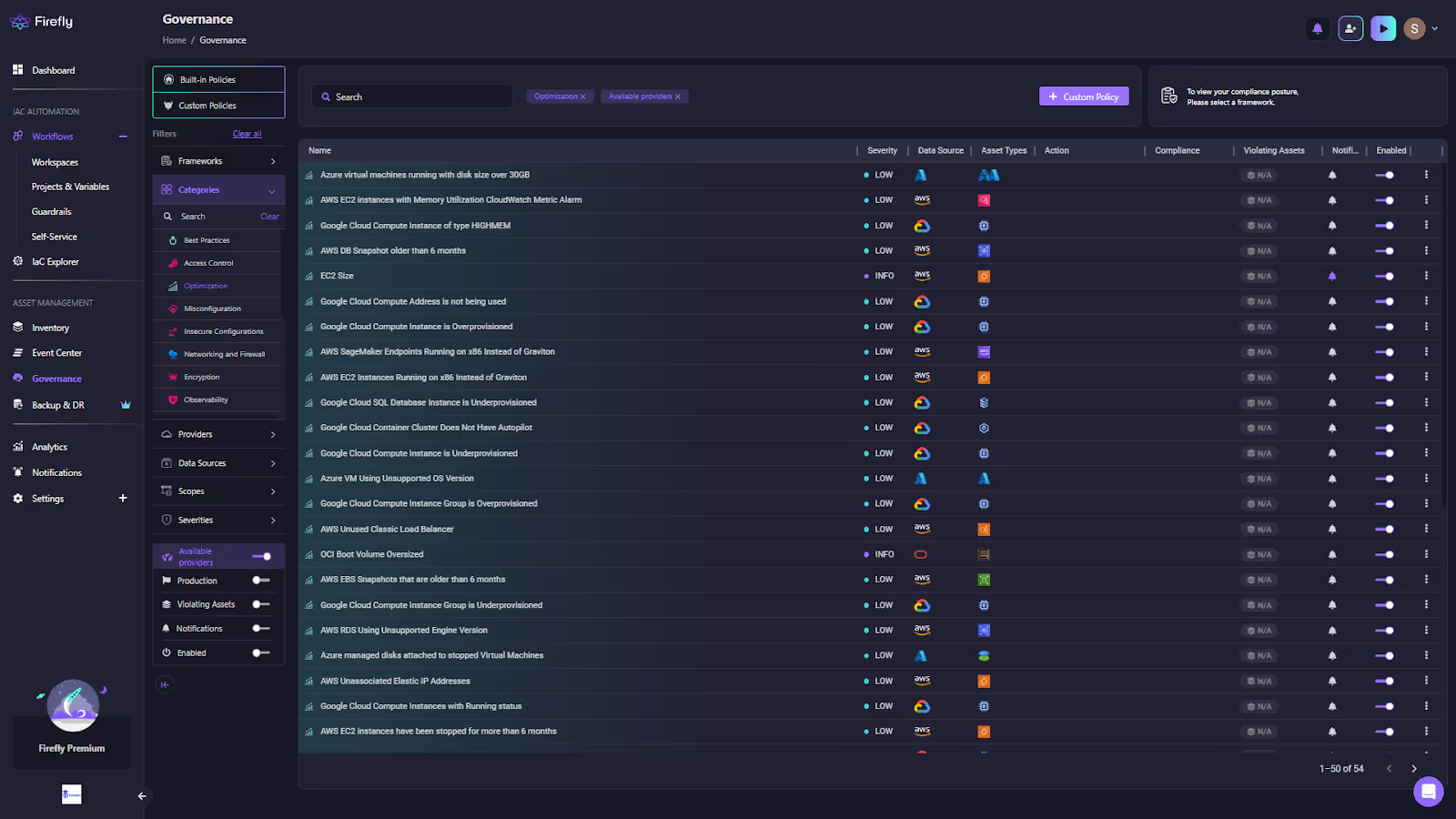
This level of cost transparency turns cloud optimization from a finance task into an everyday engineering operation.
Detecting and Fixing Cloud Waste
Most waste comes from forgotten or idle resources that quietly accumulate cost. Firefly continuously scans for these inefficiencies and flags them for cleanup.
Common examples include:
- Unattached volumes, such as EBS or Azure Disks.
- Idle compute instances running under 5% CPU for extended periods.
- Orphaned IPs are still allocated but unused.
- Snapshots and backups that exceed retention policies.
Each finding includes the estimated monthly waste and a recommended action. Firefly can automatically open a pull request to remove the resource or trigger a cleanup workflow through its automation engine.
Cost Guardrails in Workspaces
Firefly Guardrails bring FinOps directly into the CI/CD pipeline, making cost control part of every code review, not an afterthought. Instead of catching budget overruns weeks later, these guardrails evaluate every Terraform plan or deployment against predefined limits in real time.
Teams can define precise rules that:
- Alert when an environment exceeds its allocated budget.
- Block merges that introduce resources outside cost or compliance limits.
- Prevent deployment of unapproved instance types or untagged assets.
For example, a team might configure a Guardrail to stop any Terraform plan that adds more than $1,000/month in new spend, or to block a pull request if a resource lacks mandatory cost tags.
Below, the screenshots show how this enforcement works in practice:
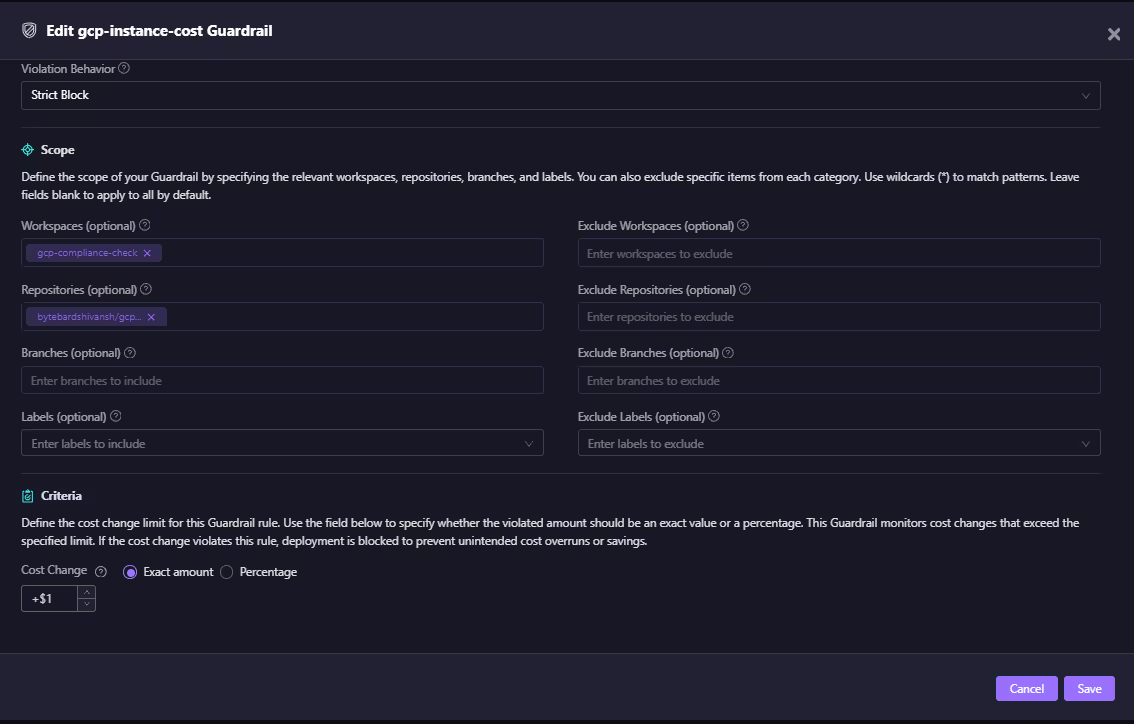
- In the Guardrails setup screen, engineers define the scope of each rule, selecting workspaces, repositories, or branches, and set the violation behavior (alert, soft block, or strict block). The rule can be based on exact dollar limits or percentage-based cost changes, ensuring flexibility for both dev and prod environments.
- During a Terraform plan, Firefly analyzes the proposed infrastructure changes and estimates their cost impact. If the plan exceeds the allowed limit, it’s automatically blocked before deployment.
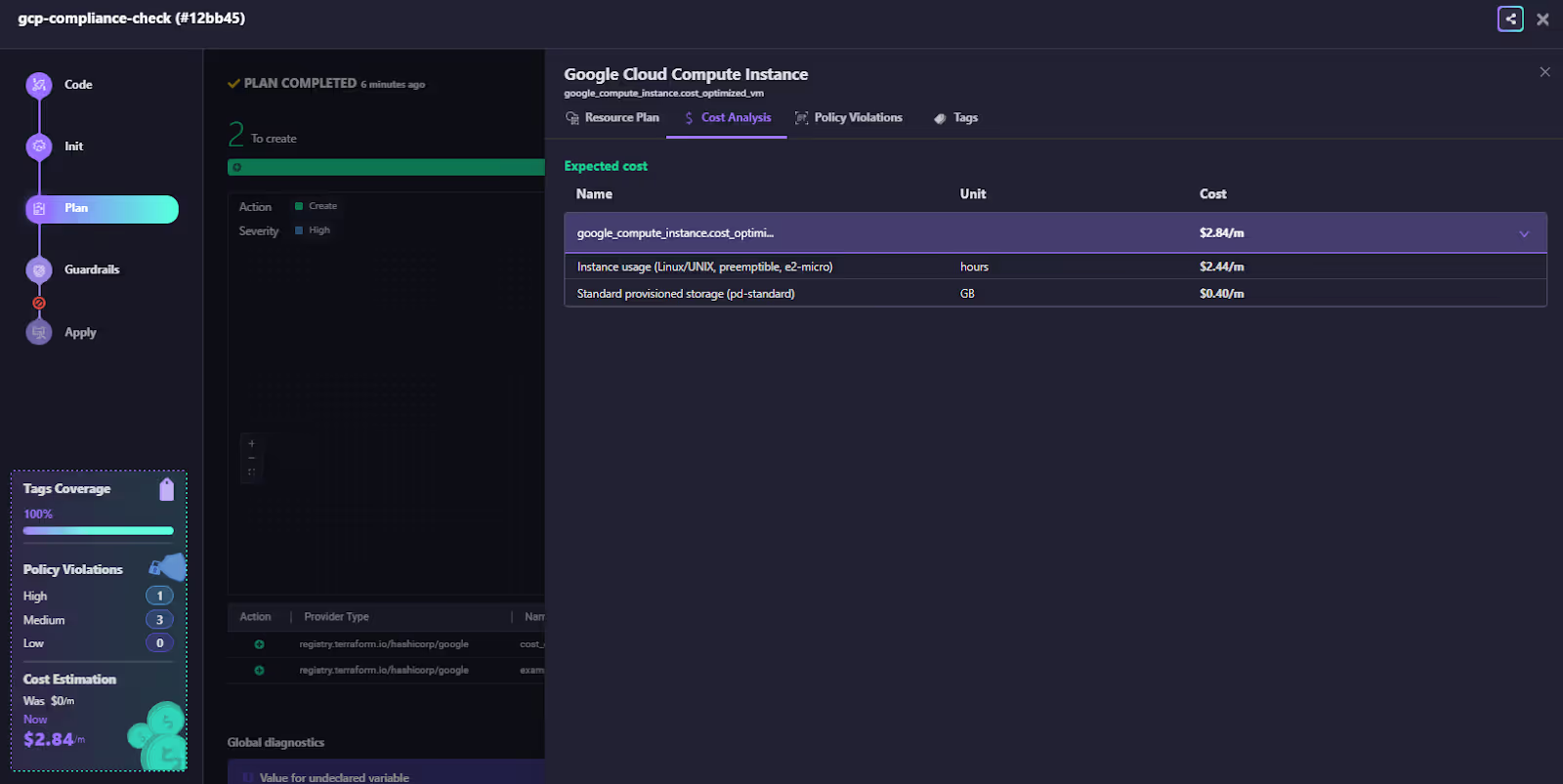
- The pipeline view below shows a gcp-compliance-check run where one Guardrail blocked a cost increase of +$2.84/month beyond the allowed +$1 threshold.
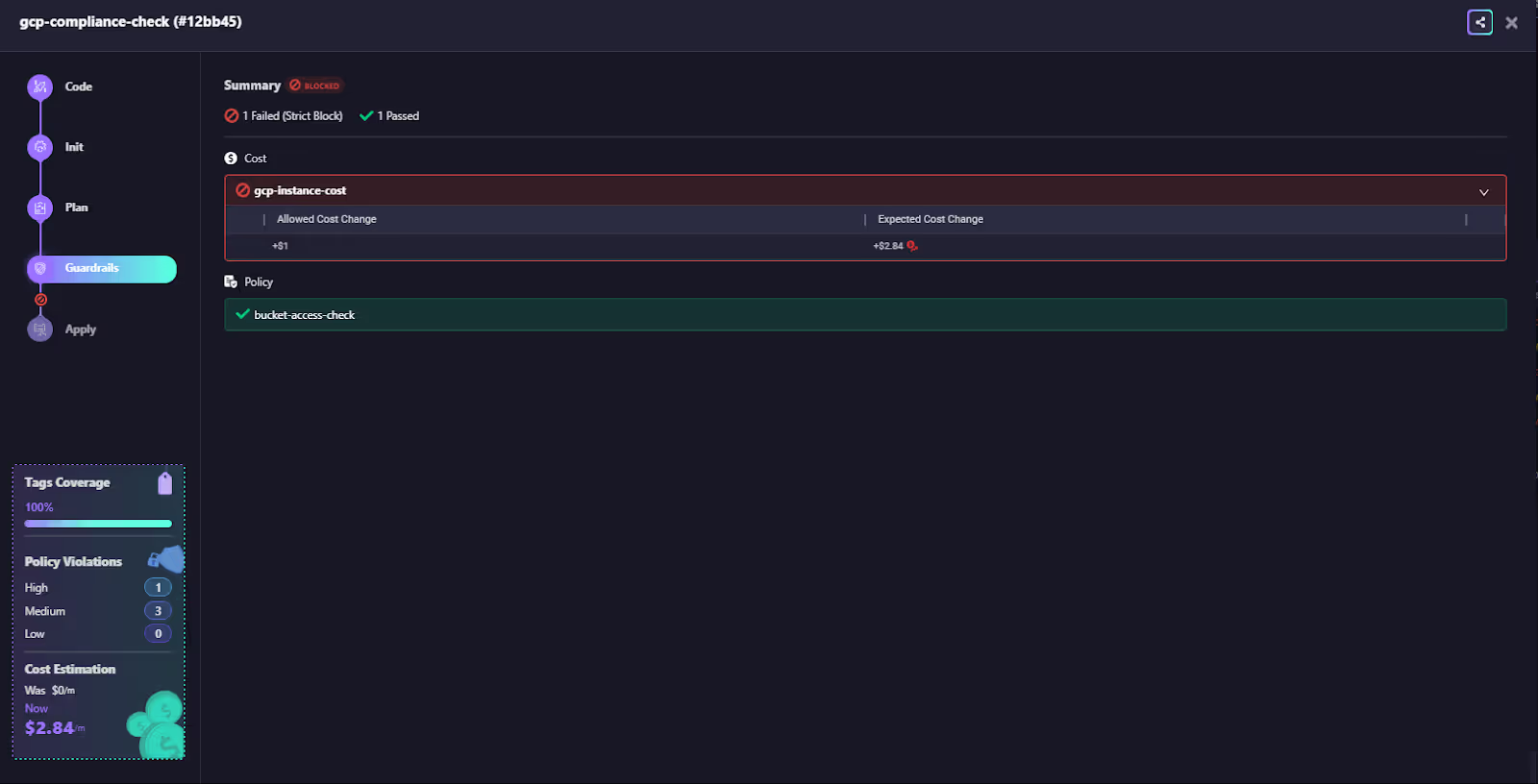
The pipeline stops immediately, providing engineers with clear visibility into which rule failed and why. It also pushes a notification in Slack notifying who, and what is being deployed beyond the threshold set.
These guardrails integrate natively with Firefly Runners and existing Ci/CD pipelines, so engineers see cost violations and compliance issues in the same context as their deployment results. This turns cost enforcement from a reactive review step into an automated, built-in quality gate for every commit.
Automated Remediation
Firefly’s automation engine doesn’t just detect issues; it can act on them. When a Cloud Waste policy is violated, Firefly can:
- Suggest or execute deletion commands for unused resources.
- Resize or downgrade underutilized instances.
- Automatically apply missing tags or policy labels.
This reduces manual cleanup time and ensures consistent enforcement across environments without blocking developer velocity.
Continuous Cost Reporting
Firefly’s cost reports track cloud spend and optimization results over time. Reports show total spend, waste reduction, and Guardrail-triggered events by environment, team, or service. They can be exported for governance reviews or used in FinOps dashboards to demonstrate progress in cost optimization.
For FinOps teams, these reports make it easy to quantify cost avoidance, budget compliance, and ROI from automation, data that’s otherwise hard to capture manually.
Built for the Teams That Own the Cloud
Firefly is designed for the people closest to infrastructure: DevOps, SREs, and platform engineers who manage daily deployments. It fits into existing workflows rather than introducing new ones, helping teams control cost and policy without friction.
By connecting visibility, guardrails, and automation in one system, Firefly turns FinOps into an ongoing process, not a month-end review.
Applied Examples: How Teams Used Firefly in Production
The easiest way to see what FinOps looks like in practice is to look at how engineering teams are running it every day. These examples show how different organizations used Firefly to cut waste, bring unmanaged infrastructure back under code, and make cost control part of normal operations, not a separate monthly exercise. Each case reflects a practical use of automation, guardrails, and IaC reconciliation to keep cloud environments efficient and predictable.
Aqua Security reduced waste by disabling unused services and idle resources
Aqua Security used Firefly’s Cloud Waste policies to locate idle SaaS monitors, unattached volumes, and other unused cloud resources that were still accruing costs. Each finding was routed to the correct owner, with auto-generated cleanup commands executed safely during low-risk windows. This automation alone saved around $22,100 per year, and the same guardrails now run continuously to prevent waste from reappearing.
- Waste types: inactive monitors, idle workloads, unattached storage.
- Workflow: detect, alert owner, approve, execute automatically.
- Outcome: recurring savings without manual review cycles.
AppsFlyer restored control by codifying unmanaged resources
AppsFlyer manages a large AWS footprint using Terraform, but many resources had drifted from code or were created outside IaC. Firefly’s discovery engine compared live infrastructure with Terraform state, flagged unmanaged assets, and generated HCL definitions automatically. Pull requests were opened through the normal review pipeline, bringing 1,500+ resources under code and fixing over 40 drift events in one quarter.
- Workflow: discover, diff live vs. code(IaC), generate IaC, raise a PR, review, and merge.
- Guardrails: enforced tagging and resource size standards to prevent new drift.
- Outcome: complete visibility, consistent configuration, and traceable cost ownership.
Basis Technologies cut cloud waste through continuous drift checks
Basis Technologies replaced periodic audits with Firefly’s continuous drift detection. The system monitored AWS environments for configuration changes or orphaned assets that no longer matched declared IaC or tagging standards. Firefly opened pull requests for detected drift and scheduled cleanup for unattached volumes, aged snapshots, and unused IPs. This resulted in an 83% reduction in waste and about $34,000/year in verified cost savings.
- Controls: tagging, region, and instance-size guardrails; weekly cleanup workflows.
- Process: detect, open PR, review, and revert drift.
- Outcome: sustained cost reduction without slowing delivery.
These case studies make one thing clear: when cost visibility, drift detection, and automation are built directly into engineering workflows, FinOps stops being a finance process and becomes an operational habit. That’s what keeps modern cloud environments efficient, predictable, and easy to scale without losing financial control.
Scaling FinOps Across Multi-Cloud Environments
FinOps becomes a different challenge once teams move beyond a single cloud or region. Each provider, AWS, Azure, GCP, or OCI, has its own API, pricing model, and tagging logic. Without a unified control plane, the same policies and automation that work in one environment can fail to apply elsewhere. At scale, consistency is the real problem, not visibility.
Making Automation Work Across Clouds
Firefly extends the same cost and policy automation to every provider. It integrates directly with Terraform, Argo CD, GitHub Actions, and GitLab CI to evaluate changes before deployment.
- IaC Sync: Keeps AWS, Azure, GCP, OCI, and Kubernetes resources aligned with Terraform or CloudFormation definitions.
- GitOps Integration: Works with ArgoCD and Flux to auto-revert drifted resources using the same IaC baseline.
- CI/CD Guardrails: Blocks high-cost or non-compliant resources in pipelines, regardless of the cloud they target.
This ensures a single, consistent policy enforcement layer across clouds, no custom scripts or duplicated logic.
Continuous Lifecycle Governance
Once deployed, Firefly keeps the infrastructure in sync through continuous scans. It validates tagging, budget thresholds, and configuration rules across all accounts. If drift or waste appears, Firefly opens pull requests or applies pre-approved fixes automatically.
This automation removes the need for per-cloud cleanup jobs and keeps policies uniform, regardless of where workloads run. Cross-cloud consistency is the real measure of FinOps maturity. Firefly allows teams to apply the same tagging, cost, and compliance rules across every environment from a single control plane. That’s how large enterprises maintain predictable spend and operational discipline as they scale their cloud footprint.
FAQs
1. What is Enterprise Cost Management?
Enterprise cost management refers to tracking, analyzing, and optimizing IT or cloud spending across departments. It helps organizations enforce budgets, reduce waste, and align costs with business outcomes.
2. Which AWS tools help estimate costs?
AWS provides the AWS Pricing Calculator, AWS Cost Explorer, and AWS Budgets to help plan, estimate, and monitor cloud expenses effectively.
3. Which AWS tool can estimate the cost of an Amazon EBS volume before implementation?
The AWS Pricing Calculator is used to estimate the cost of Amazon EBS volumes and snapshots before deployment by simulating different configurations and usage levels.


