TL;DR
- Enterprises face rising cloud inefficiencies, with 91% wasting spend due to overprovisioned, idle, or unmanaged resources caused by fragmented and manual governance.
- Traditional audits and centralized approval models can’t keep up with the dynamic, fast-changing nature of modern cloud and AI environments.
- Governance-as-Code (GAC) embeds compliance, security, and cost control directly into CI/CD workflows using Terraform and OPA, making governance proactive rather than reactive.
- Fragmentation and drift from ClickOps and manual fixes undermine visibility and compliance, creating cost and security risks across multi-cloud estates.
- Firefly unifies governance by auto-codifying unmanaged assets, detecting and remediating drift, enforcing guardrails, and providing a single control plane, turning governance into an automated, efficient, and developer-friendly discipline.
Cloud adoption in enterprises is accelerating rapidly, driven by AI initiatives, application modernization, and the growing need for agility. As organizations continue to invest heavily in public cloud platforms, a critical issue is emerging: despite skyrocketing cloud budgets, a significant portion of that spending is being wasted.
Nearly 91% of organizations are facing inefficiencies in cloud usage, leading to wasted resources. This waste isn’t a result of the cloud being inherently expensive, but rather due to a lack of control, accountability, and cost discipline. Overprovisioning resources that go unused and leaving idle resources running due to a lack of decommissioning are key contributors to this problem.
Traditional methods, such as manual end-of-quarter audits, simply can't keep up with the dynamic nature of modern cloud environments. As cloud resources are constantly changing, new resources spin up automatically with every code push, and governance struggles to stay current and reactive. The old ways of managing cloud resources are no longer effective.
To address these challenges, enterprises need a fundamental shift from reactive, manual management to a proactive, automated system. Governance-as-Code (GAC) is the solution. By embedding governance directly into the engineering workflow, GAC ensures compliance is an integral part of the deployment process, helping businesses regain control and maximize the value from their cloud investments.
The Enterprise Struggles: The Hidden Cost of Fragmentation
Fragmented governance is the silent killer of cloud budgets and security postures. It’s a reality born from a combination of manual processes, tool silos, and out-of-date organizational models.
The Visibility Gap and ClickOps
The biggest problem in the cloud is a Visibility Gap. Most enterprises rely on Infrastructure-as-Code (IaC) tools like Terraform or CloudFormation to manage their resources. Their internal governance tools or scripts, with every deployment, check only the resources defined in that IaC.
The issue here is that the unmanaged resources, often created via the console or what we call ClickOps, completely bypass the IaC pipeline and, even, bypass central governance tools. This creates unmonitored, unknown assets.
The Cost of Drift and Policy Fatigue
Even if everything starts perfectly from IaC, configuration drift is inevitable. A developer logs in to quickly fix a production issue, changes a setting, and now the live cloud environment no longer matches the defined state in the Terraform code. This leads directly to policy drift and non-compliance.
Financial Impact: This delay in detection is expensive. McKinsey research quantifies this: when governance signalslike a security violation or a cost overrun surface too late, projects can run 45% over budget. This isn't theoretical. It’s the direct cost of using static, backward-looking policies in an environment that changes every minute. The longer a non-compliant resource lives, the more money it costs, and the higher the security risk.
Evolving Organizational Models: Federated Control
The traditional, old-school Centralized Governance Modelwhere a single, monolithic Cloud Center of Excellence (CCoE) tries to approve every single cloud resource across the organization, is a guaranteed way to slow down cloud adoption to a crawl. It creates a bottleneck and encourages shadow IT.
The key to success is the Federated Model. It's about achieving centralized policy definitions (setting the organizational standards) that are then enforced through decentralized, automated guardrails. Engineers across different business units can move fast because the guardrails are immediate and automated, allowing them to innovate within the clearly defined boundaries of security, compliance, and cost.
GCP Compliance Validation with Terraform and OPA: A Hands-On Walkthrough
Let’s suppose you're an engineer responsible for ensuring your company's infrastructure is secure, compliant, and cost-effective in Google Cloud Platform (GCP). You’re tasked with creating a secure, scalable solution for managing cloud resources, specifically focusing on Google Cloud Storage (GCS) buckets.
In this scenario, you need to enforce a critical security rule: every GCS bucket must have uniform_bucket_level_access = true to ensure strong, consistent access control. With the growing complexity of cloud infrastructure, manual compliance checks are no longer sufficient. How do you automate and enforce this security requirement across your GCP resources? That’s where Terraform and Open Policy Agent (OPA) come in. This hands-on walkthrough demonstrates how to automate GCS bucket compliance validation using Terraform, OPA, and GitHub Actions for CI/CD.
The Problem: Ensuring Compliance at Scale
As organizations scale, maintaining compliance across cloud environments becomes increasingly difficult. With manual intervention, compliance often becomes a bottleneck, leading to errors or missed configurations. In our case, the issue is ensuring that all GCS buckets are configured with uniform_bucket_level_access = true. If a bucket is created with this setting set to false, it opens up potential security vulnerabilities.
But here’s the twist: How do you ensure that such security requirements are always met without manually auditing each resource? The solution is automated governance using policy-as-code. Here are the step to do the same:
Step 1: Setting Up Terraform to Manage GCP Resources
First, we define the infrastructure we want to manage with Terraform. Terraform allows us to declaratively define cloud resources. We define a GCS bucket, setting the configuration to the desired compliant state.
Here's how the Terraform code in main.tf looks:
Terraform
# Configure the Google Cloud Provider
terraform {
required_providers {
google = {
source = "hashicorp/google"
version = "~> 4.0"
}
}
required_version = ">= 1.0"
}
provider "google" {
project = var.project_id
region = var.region
}
# Create a Google Cloud Storage bucket with uniform_bucket_level_access set to true
resource "google_storage_bucket" "example_bucket" {
name = var.bucket_name
location = var.region
force_destroy = true
uniform_bucket_level_access = true # ENSURE COMPLIANCE
versioning {
enabled = true
}
lifecycle_rule {
condition {
age = 30
}
action {
type = "Delete"
}
}
labels = {
environment = var.environment
managed_by = "terraform"
}
}Key Takeaway: We’ve defined the google_storage_bucket resource with uniform_bucket_level_access set to true, which is our desired compliant state. However, we still need an automated check to catch errors if an engineer accidentally changes this setting.
Step 2: Enforcing Compliance with OPA
Policy enforcement is the crucial next step. We use Open Policy Agent (OPA), a general-purpose policy engine, to ensure that every Terraform plan adheres to our compliance rules. We write the policy in Rego.
Here’s how the policy in storagepolicy.rego looks:
package terraform.gcs
# Policy to enforce uniform bucket level access on GCS buckets
deny[msg] {
# Check all planned changes in the Terraform plan
input.planned_values.root_module.resources[_].type == "google_storage_bucket"
resource := input.planned_values.root_module.resources[_]
# Check if uniform_bucket_level_access is set to false
resource.values.uniform_bucket_level_access == false
bucket_name := resource.values.name
msg := sprintf("GCS bucket '%s' has uniform_bucket_level_access set to false. Security policy requires it to be true.", [bucket_name])
}
# Rule to provide policy summary for CI/CD
policy_summary = result {
violations := deny
result := {
"total_violations": count(violations),
"compliant": count(violations) == 0,
"violations": violations
}
}This Rego policy above inspects the JSON output of the Terraform plan (input.planned_values). It explicitly searches for google_storage_bucket resources where the future state (.values) sets uniform_bucket_level_access to false. If it finds one, it populates the deny[msg] rule, which blocks the deployment and provides a detailed error. This is a proactive, "shift-left" governance check.
Step 3: Automating with GitHub Actions
To ensure that policy checks are non-negotiable, we integrate the validation into our CI/CD pipeline using GitHub Actions.
Here’s the relevant part of the workflow in .github/workflows/terraform.yml:
jobs:
terraform:
runs-on: ubuntu-latest
steps:
# ... initialization steps ...
- name: Terraform Plan
run: terraform plan -out=tfplan.json
- name: Run OPA Policy Check
run: opa eval -d policy/ -i tfplan.json "data.terraform.gcs.policy_summary"
- name: Apply Terraform Changes
if: success() && github.ref == 'refs/heads/main'
run: terraform apply tfplan.jsonThe pipeline first generates the Terraform execution plan and saves it as tfplan.json. The critical step is "Run OPA Policy Check", which uses OPA to evaluate the plan against our storagepolicy.rego. If the OPA evaluation finds a policy violation (i.e., the deny rule is hit), the job fails. Critically, the final "Apply Terraform Changes" step is conditional, only running if: success() of the previous steps. This automation successfully prevents non-compliant infrastructure from ever reaching the GCP environment.
Step 4: Manual Testing and Policy Violations
When an engineer accidentally sets uniform_bucket_level_access = false and commits the code, the CI/CD pipeline runs the OPA check:
Result (Policy Violation): The pipeline stops, and the OPA output will show:
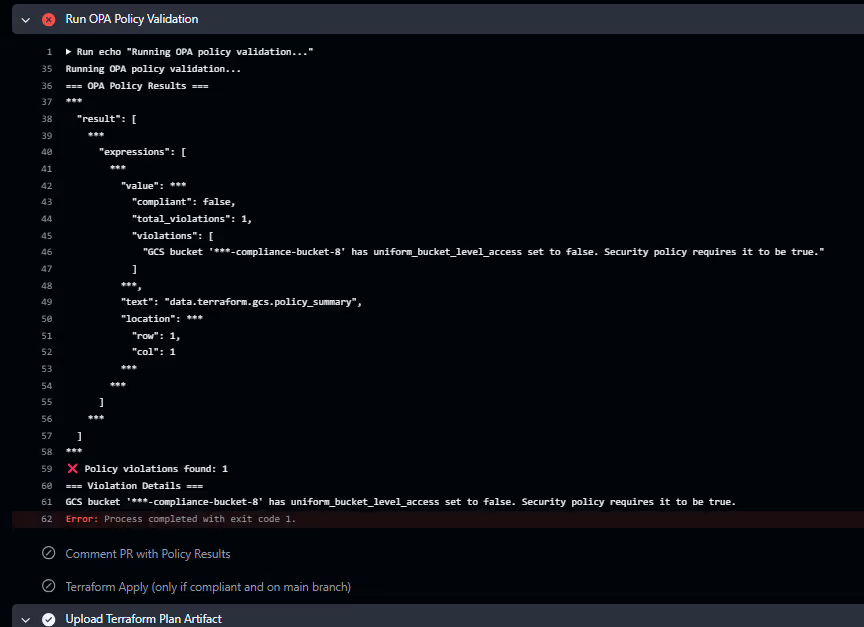
GCS bucket 'my-insecure-bucket' has uniform_bucket_level_access set to false. Security policy requires it to be true. The engineer is forced to correct the IaC code before the pull request can be merged. When the code is compliant (uniform_bucket_level_access = true), the policy check passes, and the deployment proceeds.
Challenges Demonstrated and The Bigger Picture
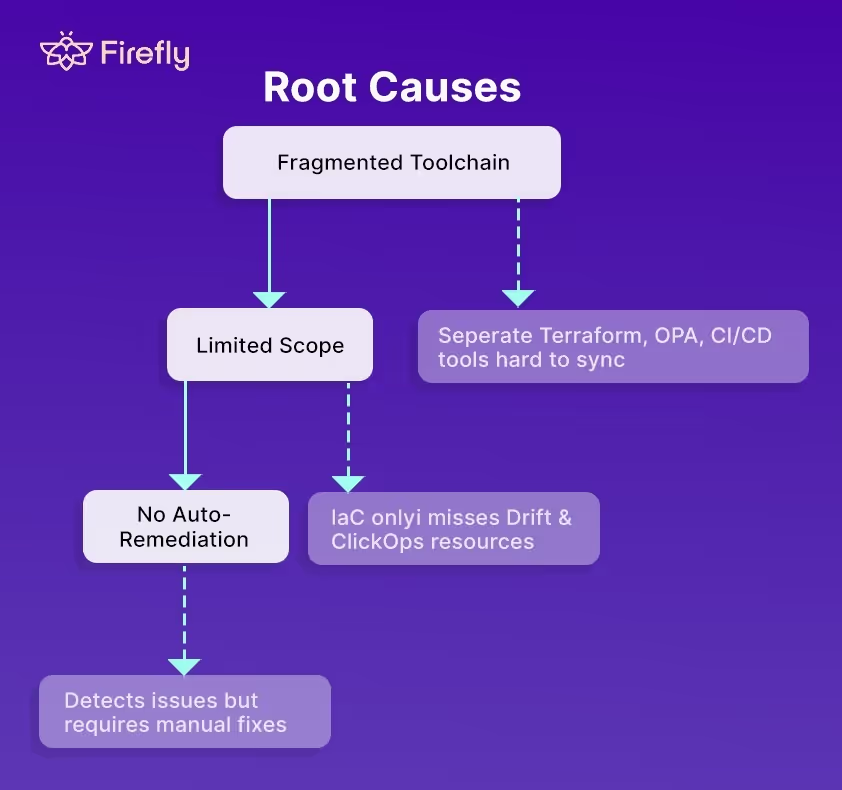
The above walkthrough exposes the inherent challenges of this manual Governance-as-Code setup at enterprise scale:
- Scope Limitation: This only checks new deployments. It does absolutely nothing to police configuration drift (manual changes after deployment) or resources created via ClickOps. These remain critical visibility and control gaps.
- Fragmentation: We are manually gluing together three separate tools: Terraform (IaC), OPA (Policy), and GitHub Actions (CI/CD). Managing this toolchain across multiple clouds (AWS, Azure, etc.) requires massive, duplicate effort.
- No Remediation: The system denies without remediation to automatically fix non-compliant configurations or automatically codify ClickOps resources, leaving the burden of remediation entirely on the development team.
This setup proves GAC works in principle, but the next section will discuss the need for a unified platform to manage GAC at the speed and complexity required by modern enterprises.
Firefly’s Solution: Making Governance-as-Code Work
The core problem with the manual, multi-tool GAC setup is its reliance on disconnected scripts for Terraform, OPA, and CI/CD glue. is operational complexity and coverage failure. It creates silos: policy checks only cover new IaC, leaving live configuration drift and manual ClickOps resources completely invisible.
The solution requires shifting the control plane from this fragmented toolchain to a unified, codified platform. This platform treats Governance-as-Code (GAC) not as a static, pre-deployment policy checker, but as a live, automated system for continuous resource lifecycle management and compliance enforcement across the entire cloud estate. Its primary technical value is achieving a true single pane of glass for both the IaC desired state and the live cloud actual state.
Unified Governance Across All Cloud Platforms
Large enterprises rarely stick to a single cloud. They have critical workloads on AWS, Azure, GCP, OCI, and Kubernetes. The primary enemy is fragmentation, where security and compliance teams must manage multiple policy engines and disparate compliance views. Firefly offers a single, centralized platform to define and enforce organizational policies, covering security, cost, and compliance, across all major cloud environments (as visible in the Governance Policy Dashboard shown in ).
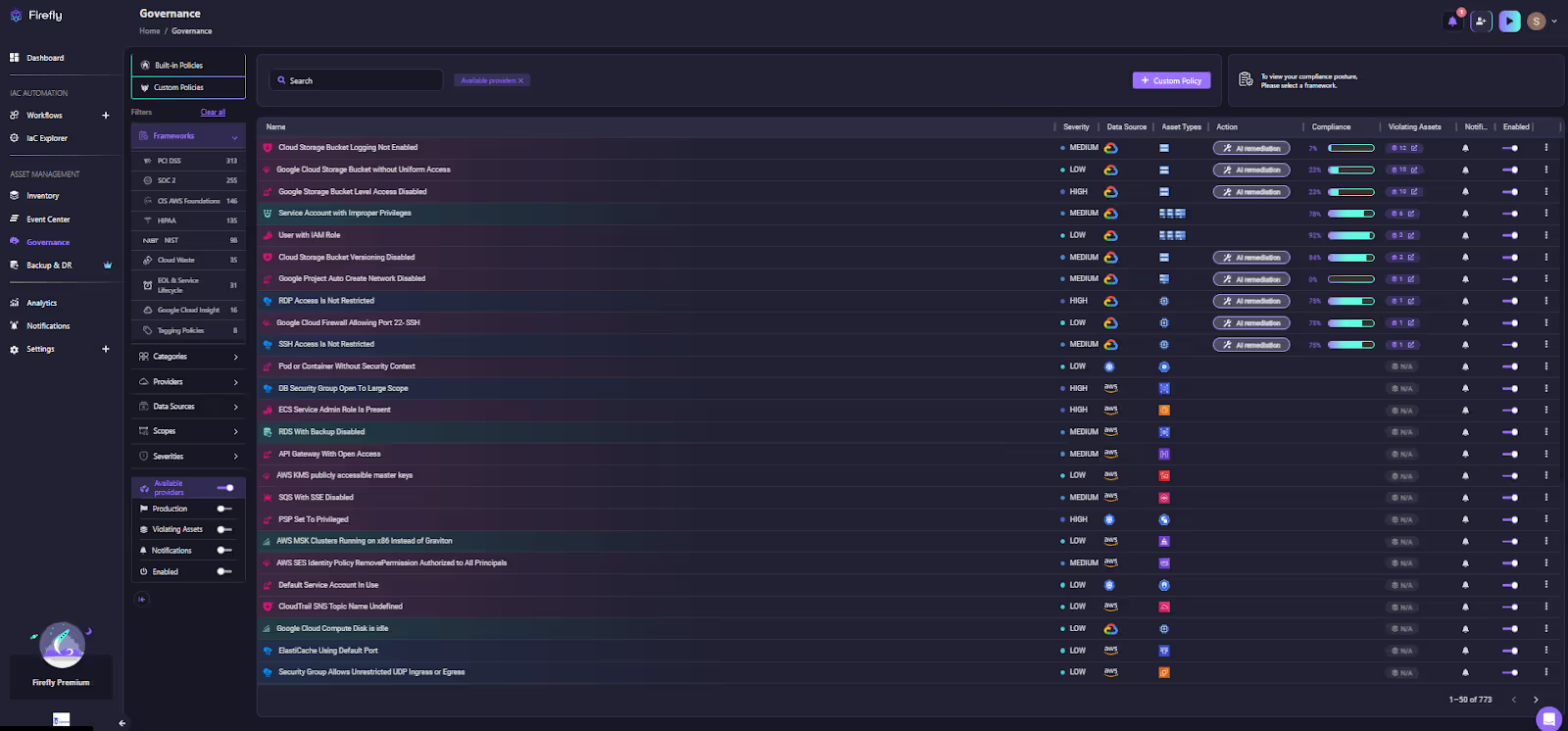
This consolidation immediately simplifies the governance control plane, moving from tool sprawl to a single source of truth. The platform is built on the Open Policy Agent (OPA) framework and manages dozens of built-in policies for security, compliance (e.g., CIS, SOC2), and cost optimization.
Bridging the Gap: Automating Resource Codification
The single most significant security and control gap is unmanaged infrastructure (ClickOps). Firefly addresses this by continuously scanning the entire cloud footprint (live state) and allowing you to convert any manually created infrastructure into deployable IaC (Terraform/OpenTofu) using Thinkerbell's AI capabilities.
This process, often called Resource Codification, is important because it includes every resource, even those created outside the IaC pipeline, such as the prod-logs-1 storage bucket shown and tagged as Unmanaged, with a ClickOps tag indicating it was created as ClickOps:
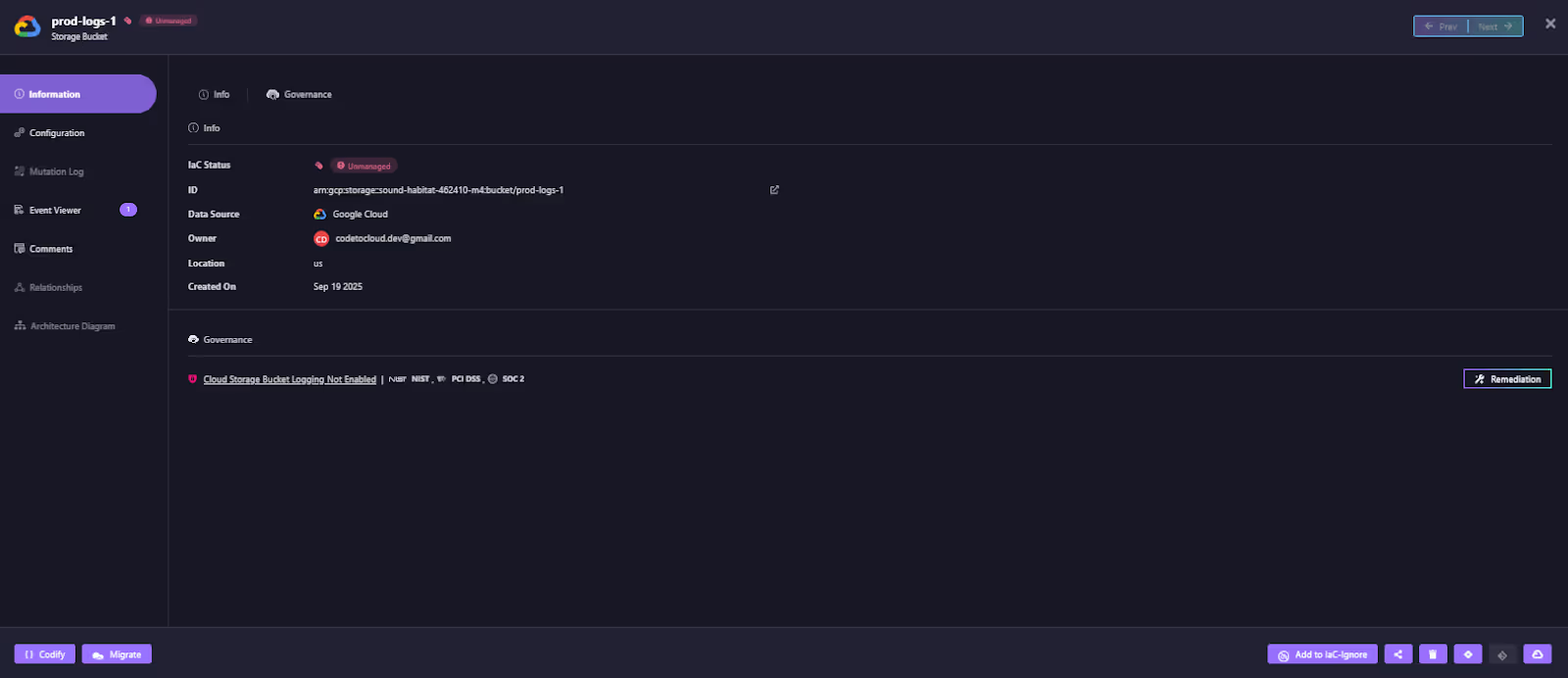
This significantly reduces risks like the one that led to the Capital One breach by eliminating unknown, unmonitored assets.
Proactive Security: Shifting Left
Governance should be preventive, not punitive. It needs to stop non-compliant deployments before they consume resources.
As shown in the walkthrough below, Firefly’s Guardrails, built on OPA, directly integrate into the Workflows running in Firefly’s SaaS runners, which are being executed within Firefly. For example, when the gcp-compliance-check is being deployed, the platform detected that a configuration is being deployed that fails the bucket-access-check policy
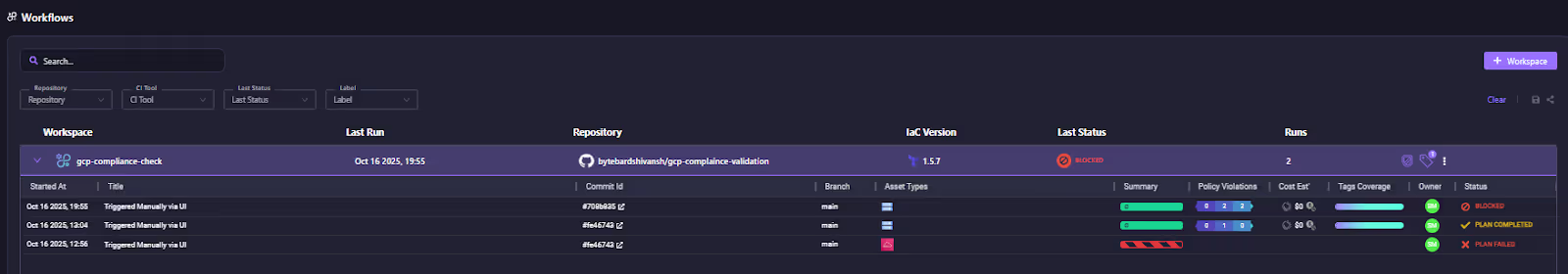
The deployment at the Apply stage was BLOCKED because the policy violation was detected at the Plan stage. Here is how Firefly runners blocked the workflow before it gets applied:
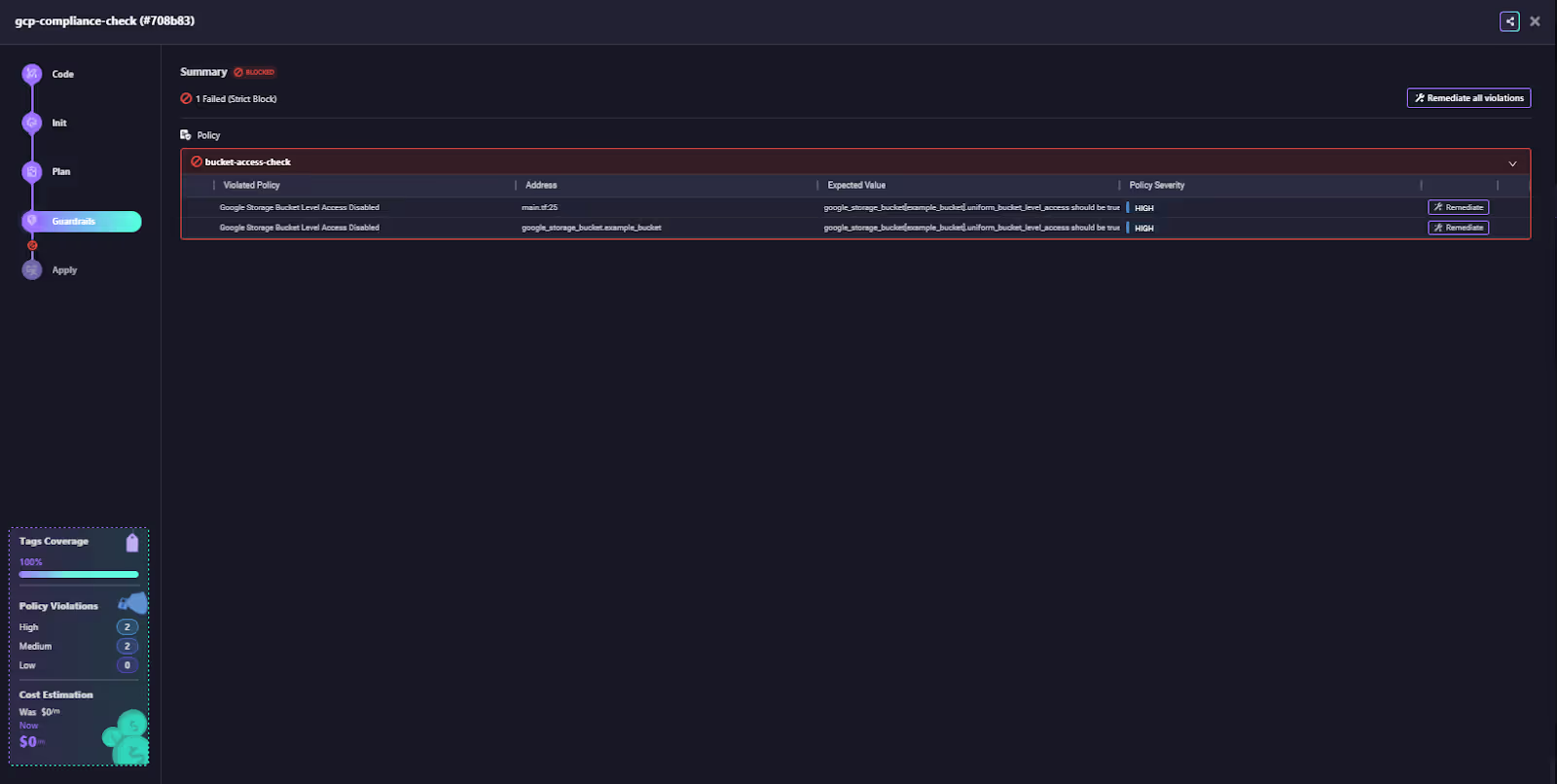
This enforcement happens automatically when the repository is added to a SaaS Runner without the need for manual Rego code writing into a YAML file. This "Shift-Left" mechanism prevents non-compliant code from ever being deployed. The platform, in this manner, also enforces Proactive Governance.
Enforcing GitOps: Automating Drift Fixes
Configuration drift is quite common in enterprises where multiple teams access the same infrastructure with various intentions, but it cannot be ignored. Firefly helps prevent policy and configuration drift by enforcing an auditable workflow against the codified state. Any deviation from the defined IaC triggers one of two automated actions, ensuring the live state and the codified state always match:
- Reconcile the Live Asset to IaC (Revert): The platform detects a manual change (tracked in the Event Center) and automatically reverts the live asset to the desired state defined in the code. This is strict enforcement.
- Align IaC to Live Asset (Accept & Codify): If a manual change was necessary (e.g., an urgent production fix), Firefly accepts the change and automatically generates a Git Pull Request (PR) to update the IaC code in the repository. This preserves the manual fix while maintaining Git as the single source of truth.
Firefly significantly reduces manual workload by using AI to automatically generate the necessary IaC patches (the corrected Terraform HCL) or the equivalent CLI commands to fix the drift. This feature, demonstrated by the "Remediate" option next to violations, reduces Mean Time to Remediation (MTTR) from days (waiting for a developer to manually write the fix) to mere minutes.
Proof that Governance-as-Code Works
The shift to a platform-based Governance-as-Code (GAC) model isn't just about better control; it delivers tangible, measurable financial and operational benefits. It transforms governance from a cost center into a core value driver.
Micro FinOps: Cutting Cloud Waste at the Source
Effective GAC immediately impacts the bottom line by eliminating the low-hanging fruit of cloud waste.
Case Study: Comtech. By automating drift detection and governance, Comtech was able to identify and fix a specific, recurring automation flaw that was creating unnecessary, idle resources. This wasn't a manual oversight; it was a bug in the provisioning logic that was allowed to run rampant. The fix, enabled by continuous GAC monitoring, resulted in a hard, annual saving of $180,000. This proves GAC is essential for Micro FinOps: catching the small, recurring waste patterns that manual auditing misses.
Boosting Developer Velocity: Platform Engineering Efficiency
A common misconception is that governance slows down developers. The opposite is true when governance is automated and embedded.
Case Study: AppsFlyer. By implementing an automated platform engineering model that explicitly treated governance as a product, AppsFlyer achieved an 84% boost in platform engineering efficiency. This was done by providing developers with pre-approved, compliant IaC templates and automated guardrails. Instead of waiting for manual security reviews, developers received immediate, actionable feedback from the GAC engine. This demonstrates that effective, automated governance accelerates, not hinders, developer velocity.
Security Outcome: The most critical benefit is risk reduction. Enterprises that successfully implement this proactive, automated governance approach see dramatic security improvements, achieving 99.8% compliance and effectively realizing nearly zero security incidents tied to misconfigured or non-compliant cloud resources.
FAQs
1. What is the enterprise governance framework?
An enterprise governance framework is a structured system of policies, processes, and tools that ensures accountability, compliance, and alignment between IT operations and business objectives. In cloud environments, it defines how resources are managed, secured, and optimized across teams and platforms to maintain control, transparency, and regulatory compliance.
2. What is the primary role of AWS governance in cloud security?
AWS governance provides the mechanisms and tools, such as AWS Control Tower, Service Control Policies (SCPs), and AWS Config, to enforce security, compliance, and operational standards. Its primary role is to prevent misconfigurations, manage permissions through IAM, and ensure consistent enforcement of security baselines across all AWS accounts and workloads.
3. What is enterprise data governance?
Enterprise data governance is the process of managing data availability, integrity, privacy, and security across the organization. It establishes policies and frameworks to ensure data is accurate, compliant with regulations (like GDPR or HIPAA), and used ethically and consistently for analytics, AI, and business decision-making.
4. What is an example of enterprise data?
Enterprise data includes critical information used to run and manage an organization’s operations. Examples include operational data like customer orders and transaction records, financial data from billing and accounting systems, and HR data such as employee details and labor statistics. This data forms the foundation for decision-making, compliance, and business growth.


