TL;DR
- Enterprise cloud migration today is about modernization with control, not just moving workloads from one platform to another.
- Most large organizations operate across AWS, Azure, and GCP, creating complex governance, identity, and cost challenges.
- Manual migration methods carry forward drift, inconsistent tagging, and security gaps, reducing reliability and compliance.
- Infrastructure-as-Code (IaC) is essential for achieving repeatability, auditability, and automation; yet, many enterprises still lack full IaC coverage.
- Firefly solves this by automatically discovering all live cloud assets, generating IaC, detecting drift, and enforcing guardrails across environments.
- The outcome is a controlled, compliant, and efficient migration process that maintains visibility and governance across every cloud.
Enterprise cloud migration today is less about “moving to the cloud” and more about running across multiple clouds without losing control. Most large companies already use AWS for scale, Azure for Microsoft integration, and GCP for data and AI. Each defines identity, networking, and policy differently. You can’t reuse the same templates or IAM logic across them; what works in AWS IAM doesn’t directly translate to Azure RBAC or GCP IAM.
Over the years, teams have built cloud environments by hand, scripts, console clicks, and partial automation. This leaves thousands of unmanaged or undocumented resources that become a problem when you start migrating workloads or unifying governance.
That’s where Firefly fits in. It automatically discovers every resource across clouds, generates IaC definitions from what already exists, detects configuration drift, and applies policy guardrails to keep everything compliant.
This guide shows how to build a codified migration workflow that works across AWS, Azure, and GCP, from discovery and codification to continuous governance, using Firefly as the control plane.
Why Cloud Migration Becomes a Necessity (and Not Just a Strategy)
Cloud migration isn’t always about cost savings or modernization. Sometimes, it’s driven by capability alignment, where data and workloads are moved to the platform that best meets your specific needs. For instance, AWS dominates in global scale and enterprise integrations, Azure is unmatched in Microsoft ecosystem alignment and compliance tooling, and GCP excels in data analytics, AI, and ML workloads.
The necessity of migrating from one provider to another arises when specialized workloads demand it. Imagine your organization already runs on AWS with all your data inside S3 buckets, and your data science team realizes that GCP’s Vertex AI and BigQuery pipelines are better suited for your ML workflows. Now, you need to migrate your ML workloads into GCP, but your data remains in AWS S3.
The challenge becomes clear: migrating that data and aligning your infrastructure between two distinct cloud platforms is not a trivial task. You need to ensure consistent configurations, policies, encryption keys, and access controls across both providers. Without proper tools and processes, this migration could be prone to human error, creating gaps in security and governance.
The Enterprise Cloud Migration Lifecycle
Every large-scale migration follows a consistent pattern: discover what exists, prepare a secure foundation, codify it, migrate in stages, then optimize and govern.
Each cloud provider describes this process differently; AWS uses Assess, Mobilize, Migrate, Modernize, and Azure calls it Plan, Ready, Adopt, Govern, while GCP defines it as Discover, Plan, Migrate, Optimize. However, the underlying process remains the same.
1. Discovery and Assessment
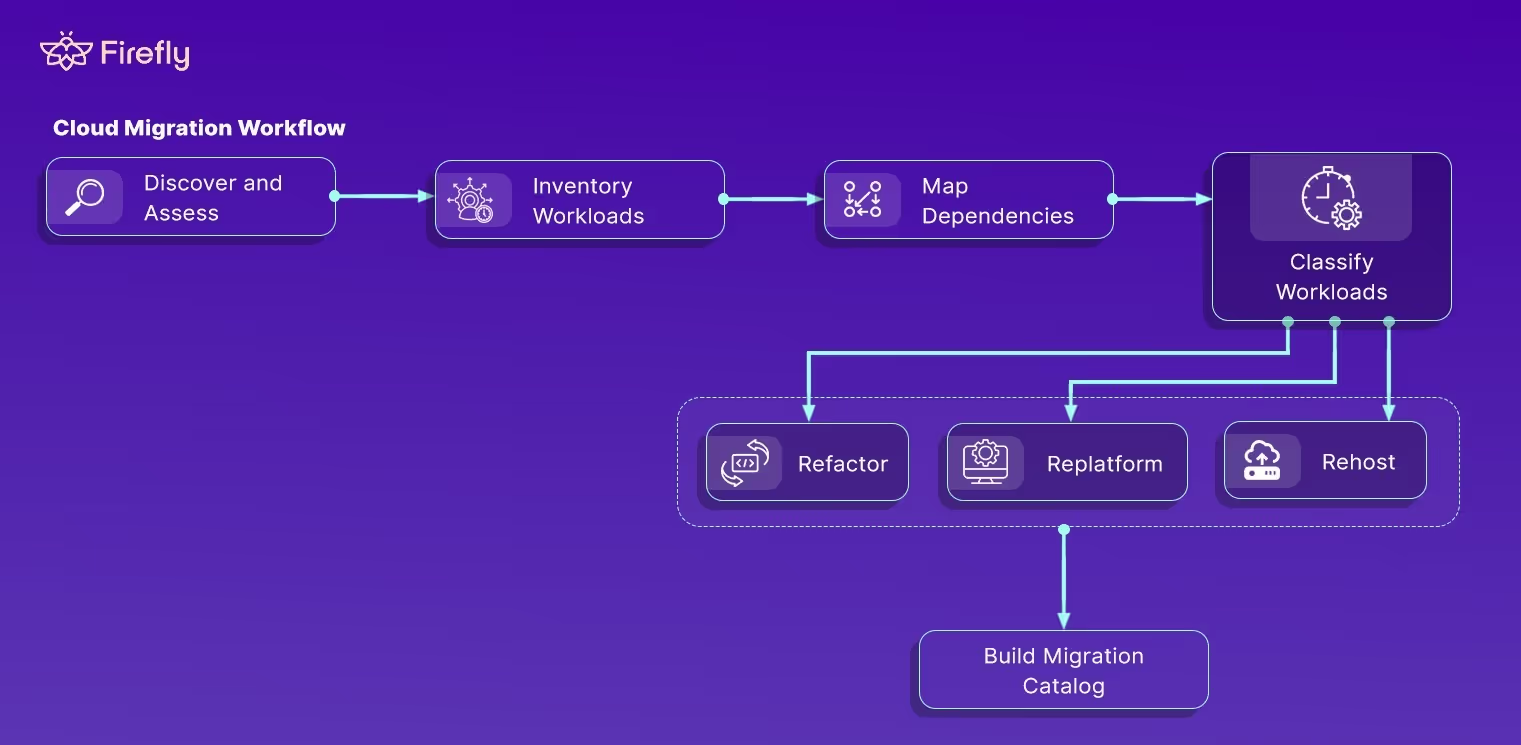
Before moving anything, you need a complete picture of what’s running today. Use tools like AWS Application Discovery Service, Azure Migrate, or GCP StratoZone to inventory workloads, dependencies, utilization, and ownership.
Group applications logically by dependency, not by name or instance. Move related services together to avoid broken links. Then classify each workload:
- Rehost for lift-and-shift migrations with no changes
- Replatform when moving to managed equivalents
- Refactor for workloads that need code or architecture updates
The result should be a migration catalog, a single, living inventory that defines what to move, when, and how.
2. Landing Zone Preparation
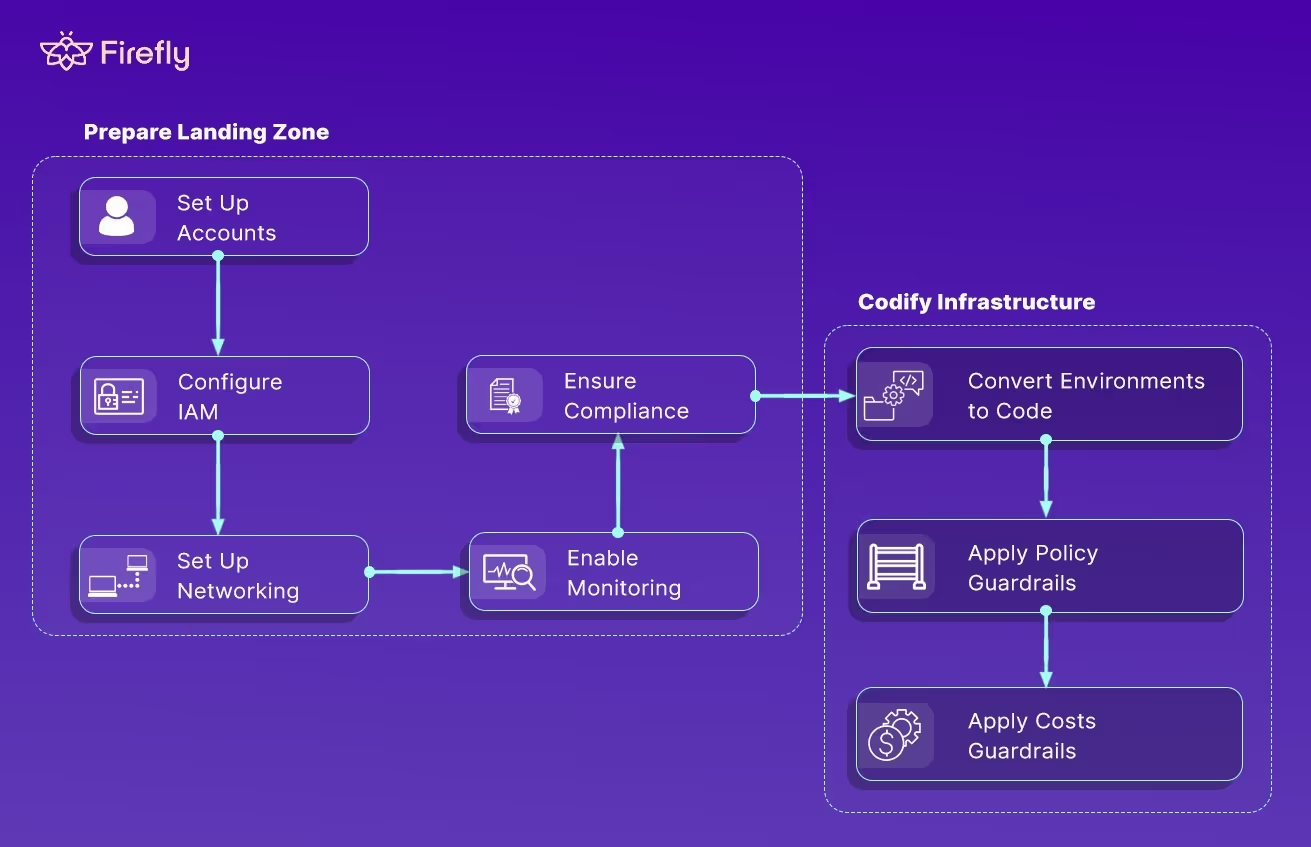
Before migration begins, prepare the target cloud environment with a defined structure, security, and networking. This includes accounts or subscriptions, access policies, and network baselines.
Native tools for each provider include:
- AWS: Control Tower, Service Control Policies, CloudTrail, Config
- Azure: Management Groups, Blueprints, RBAC, Policy
- GCP: Organization, Folders, Projects, Org Policies, VPC Service Controls
Networking design is equally critical. Define CIDRs, private connectivity (VPN, Direct Connect, ExpressRoute), DNS, and routing upfront. A properly built landing zone prevents configuration drift before workloads even land.
3. Infrastructure Codification
Once the foundation is stable, codify it. Use Terraform, Pulumi, or OpenTofu to describe your environment declaratively, including networks, IAM, encryption, monitoring, and logging.
For existing manual environments, Firefly can automatically discover live resources and generate IaC definitions, giving you an accurate starting baseline.
Run all changes through version control and automation:
- Use terraform plan to preview.
- Run automated policy and cost checks.
- Use terraform apply only after review and approval.
Codification ensures repeatability and traceability. Every change is reviewed, logged, and versioned, and configuration drift becomes measurable.
4. Migration, Validation, and Optimization
Migrate workloads in controlled waves, starting with lower-risk systems. Utilize provider tools, such as AWS Application Migration Service, Azure Migrate, or GCP Migrate for Compute Engine, for server migration and database migration services for data movement.
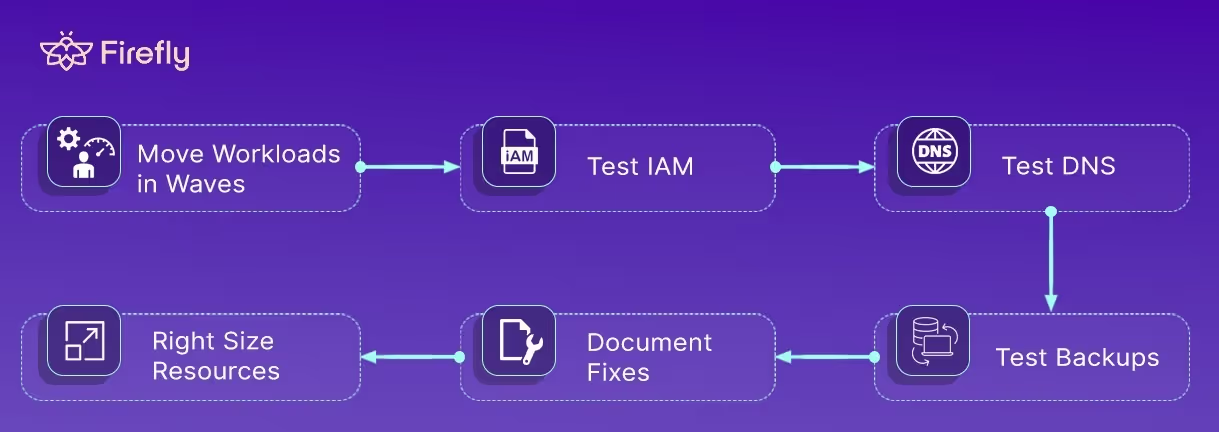
After each wave, validate IAM, routing, DNS, monitoring, and backups. Test rollback paths, document findings, and update IaC templates to capture lessons learned.
When the workflow is stable, scale it using a migration factory model, a repeatable, versioned process for each wave.
After cutover, focus on tuning:
- Right-size compute and storage
- Apply tagging and backup consistency
- Optimize cost visibility and retention policies
Every improvement and fix should be implemented through code, never made manually. That’s what keeps cloud environments consistent, auditable, and compliant.
Multicloud Reality Check
After the first few migration waves, most enterprises are multicloud by necessity. Teams choose providers for good reasons: AWS for breadth and scale, Azure for Microsoft alignment and governance tooling, and GCP for analytics and ML. Add regional rules, vendor contracts, and acquisitions, and you’re operating all three.
The hard part isn’t running workloads in multiple places; it’s maintaining consistency in identity, networking, storage, and cost when each cloud implements them differently.
Identity and Access Management
- AWS IAM evaluates JSON policies per API call, which is granular but can be easily mis-scaled at scale.
- Azure Entra ID + RBAC cascades permissions through Management Groups, Subscriptions, Resource Groups, and Resources—a clear hierarchy with less granularity.
- GCP IAM stacks roles across Organization, Folder, Project; cumulative inheritance can be surprising if you expect explicit deny semantics.
Even a basic “deploy” permission is expressed differently in each provider. Don’t try to mirror roles 1:1. Define access intent (who deploys, who manages networking, who reads logs) as policy-as-code and compile it per cloud.
Networking
- AWS: Regional VPCs stitched via Transit Gateway/PrivateLink; watch CIDR overlap and transfer cost.
- Azure: VNets/Virtual WAN with tighter subnet and DNS rules; NSG or route drift often blocks hybrid paths.
- GCP: Global VPCs ease routing but couple some access to IAM, not just ACLs.
Plan CIDRs globally. Treat networks as one corporate fabric. Consistent naming and DNS strategy avoid painful overlaps and shadow routes.
Storage and Object Permissions
S3, Blob Storage, and Cloud Storage are not interchangeable once you enforce access:
- S3: IAM + bucket policy; legacy ACLs still affect evaluation order.
- Blob: RBAC and account/container keys behave unlike S3 policies.
- GCS: Uniform IAM is simpler, but some object-level controls differ from those expected for S3.
Normalize storage policies in code early, or cross-cloud backup/artifact pipelines will fail on permission semantics.
Cost of Migration: Why It Spikes and How to Control It
Migration is expensive for predictable reasons: you double-run during pilots and cutover, move large datasets, duplicate tooling until steady state, and forget to retire “temporary” resources.
Main drivers
- Running source and target concurrently (compute, DBs, licenses)
- Egress and interconnect fees (cross-region/cloud, Direct Connect/ExpressRoute, VPN)
- Refactoring/replatforming time and managed-service premiums
- Tooling overlap (security, APM, backup)
- Idle/orphaned assets (snapshots, unattached volumes/IPs)
- Missing tags/owners that hide spend and block showback
Controls that work
- Right-size before you move (Compute Optimizer, Azure Advisor, GCP Recommender).
- Gate IaC with cost checks (e.g., Infracost) in CI; fail PRs that exceed budgets or introduce high-cost SKUs without approval.
- Plan data paths to minimize egress; prefer private links; replicate incrementally.
- Enforce required tags in code (cost center, owner, env) and block non-compliant deploys.
- Time-box double-run windows and put decommission steps in the runbook—with alerts.
- Post-cutover tuning: commitments/Savings Plans, storage class moves, log/metric retention, autoscaling thresholds.
A key takeaway is that the cost problem exists because every cloud expresses the same idea differently, in terms of configuration, tagging, and billing. To manage it reliably, those definitions must live in one place and render consistently.
That’s exactly what Infrastructure-as-Code enables.
Infrastructure as Code: The Minimum Operating Standard
If multicloud introduces three different control planes, IaC is how you express one intent and render it three ways. It’s no longer “nice to have”; it’s how you achieve scale, control, and auditability.
1) Repeatability
Build every environment from the same versioned modules. Align CIDRs, tagging, encryption, logging, and baseline policies across AWS/Azure/GCP. If you can’t recreate it from code, you can’t claim it’s secure or compliant.
2) Auditability
All changes flow through version control. A standard pipeline previews (plan), runs policy checks (e.g., OPA/Rego), estimates cost (Infracost), and requires review before apply. Your PR history becomes your compliance evidence.
3) Enforcement
Move governance left. Define guardrails as code (e.g., “encrypt storage,” “require owner tag,” “no public endpoints”) and block non-compliant plans pre-deployment. Preventive controls beat cleanup sprints.
4) Codifying What Already Exists
The biggest gap is legacy. Years of manual builds won’t magically conform to templates. Firefly scans live AWS/Azure/GCP, generates Terraform/Pulumi/OpenTofu for real resources, and gives you an immediate codified baseline—so drift detection and policy enforcement start on day one.
5) Continuous Drift Detection
Compare the deployed state to the desired state continuously. With Firefly, drift shows up in dashboards, links to the exact code, and is remediated via PRs, not hotfixes in production. That keeps environments aligned as teams move fast.
6) IaC as the Enterprise Control Plane
Treat IaC as the source of truth for identity, network boundaries, encryption, and tags. Combined with Firefly’s discovery, codification, and guardrails, you get a practical control plane that spans AWS, Azure, and GCP, providing consistent standards, continuous compliance, and clear ownership, without attempting to make the clouds behave identically.
Where Firefly Fits in the Migration Flow
When enterprises start a large-scale migration, the biggest challenge isn’t “how to deploy to another cloud.” It’s figuring out what you already have, how it’s managed, and how to move it without losing governance, context, or IaC control. That’s exactly where Firefly plugs in, between the discovery and execution phases of the migration lifecycle.
Firefly becomes the control center for your hybrid state: it discovers everything you have across AWS, Azure, GCP (and even SaaS and Kubernetes), codifies it into Terraform/Pulumi/OpenTofu, detects drift, enforces policy, and lets you generate migration-ready IaC for other clouds.
Let’s walk through how this fits into an enterprise migration.
Discover and Inventory All Cloud Assets
When you first open Firefly Inventory, you see a complete, searchable map of every asset across AWS, Azure, and GCP, organized by provider, type, owner, and IaC status.

(This is where the user sees codified, unmanaged, and drifted assets.)
Here’s what matters in a migration context:
- You instantly see which assets are Unmanaged (no IaC), Codified (tracked by Terraform/Pulumi), or Drifted (IaC mismatch).
- The IaC Coverage bar at the top provides a sense of how “ready” your environment is for migration.
- You can filter by Data Source, Location, and Tags, e.g., show all Google Cloud Storage Buckets in us-central1 tagged Environment:Prod.
This is how an enterprise builds its migration inventory backlog, not by manual CMDB exports, but by pulling live data from every connected cloud account.
Example Use Case:
During an AWS-to-Azure migration following an acquisition, the central platform team utilizes Inventory to identify all unmanaged AWS S3 buckets associated with the acquired business unit. These become “Wave 1” migration candidates.
Codify the Existing Infrastructure
Once you’ve identified unmanaged resources, select them in bulk and click Codify. Firefly auto-generates Terraform (or Pulumi/OpenTofu) templates for each selected asset.
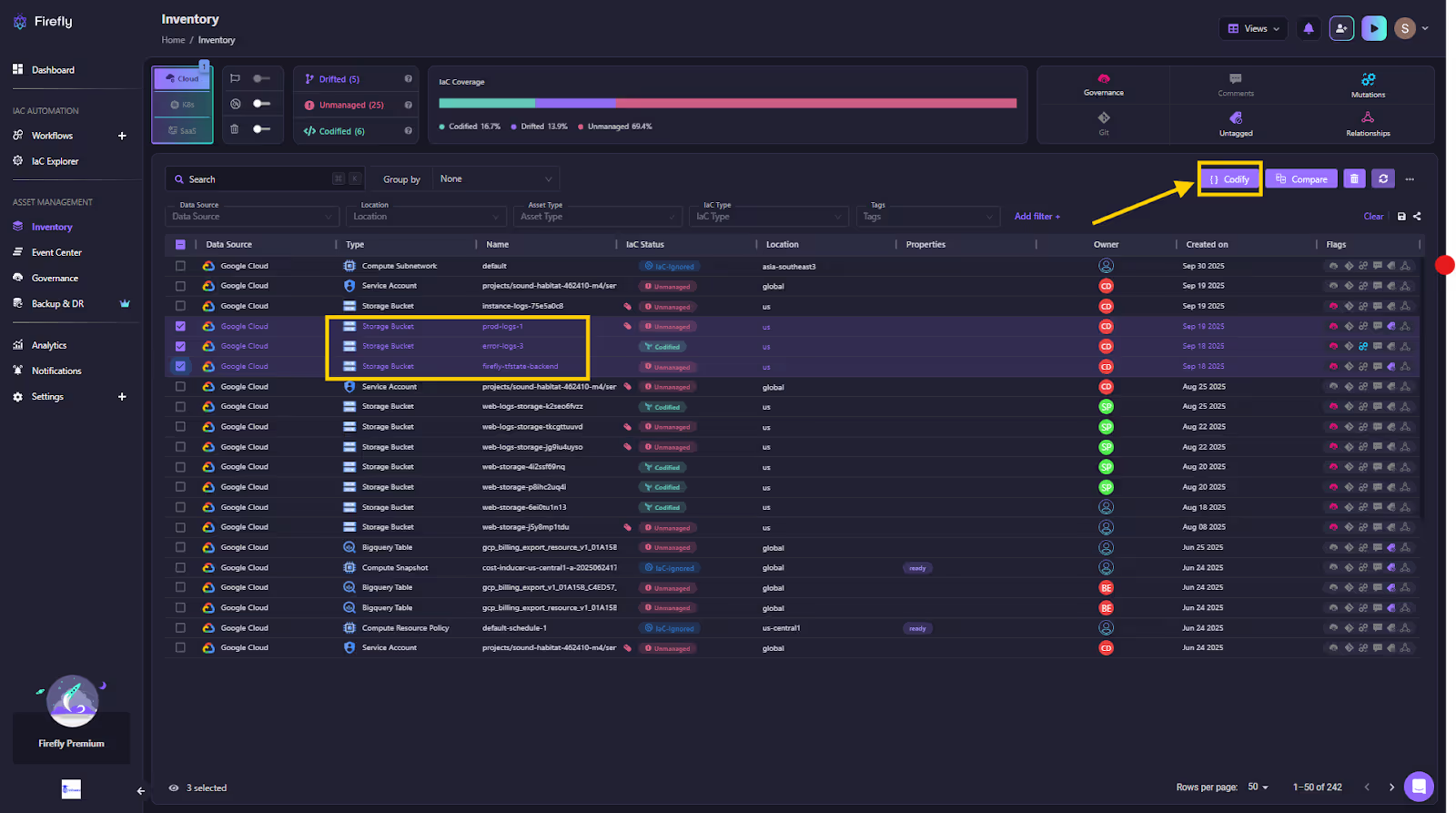
Here, you see Firefly generates Terraform definitions for three existing S3 buckets, each tagged with environment and ownership metadata. The generated code automatically includes:
- Region and environment variables (us-east-1, dev)
- Ownership and governance tags (managed_by = terraform)
- Default encryption and backend logging structure
Firefly supports multiple providers, including Terraform, OpenTofu, Pulumi, and Crossplane, ensuring compatibility with your existing workflows.
Once codified, you can:
- Download Terraform directly
- Open a Pull Request to your IaC repository
- Separate variables, provider blocks, and imports automatically
- Include comments, dependency mappings, and locals blocks for readability
This is how you bootstrap IaC coverage for environments that were never built with code in the first place.
Here, you can see Firefly’s side panel listing provider frameworks, Terraform, Pulumi, Crossplane, Config Connector, and migration targets AWS, Azure, and OCI:
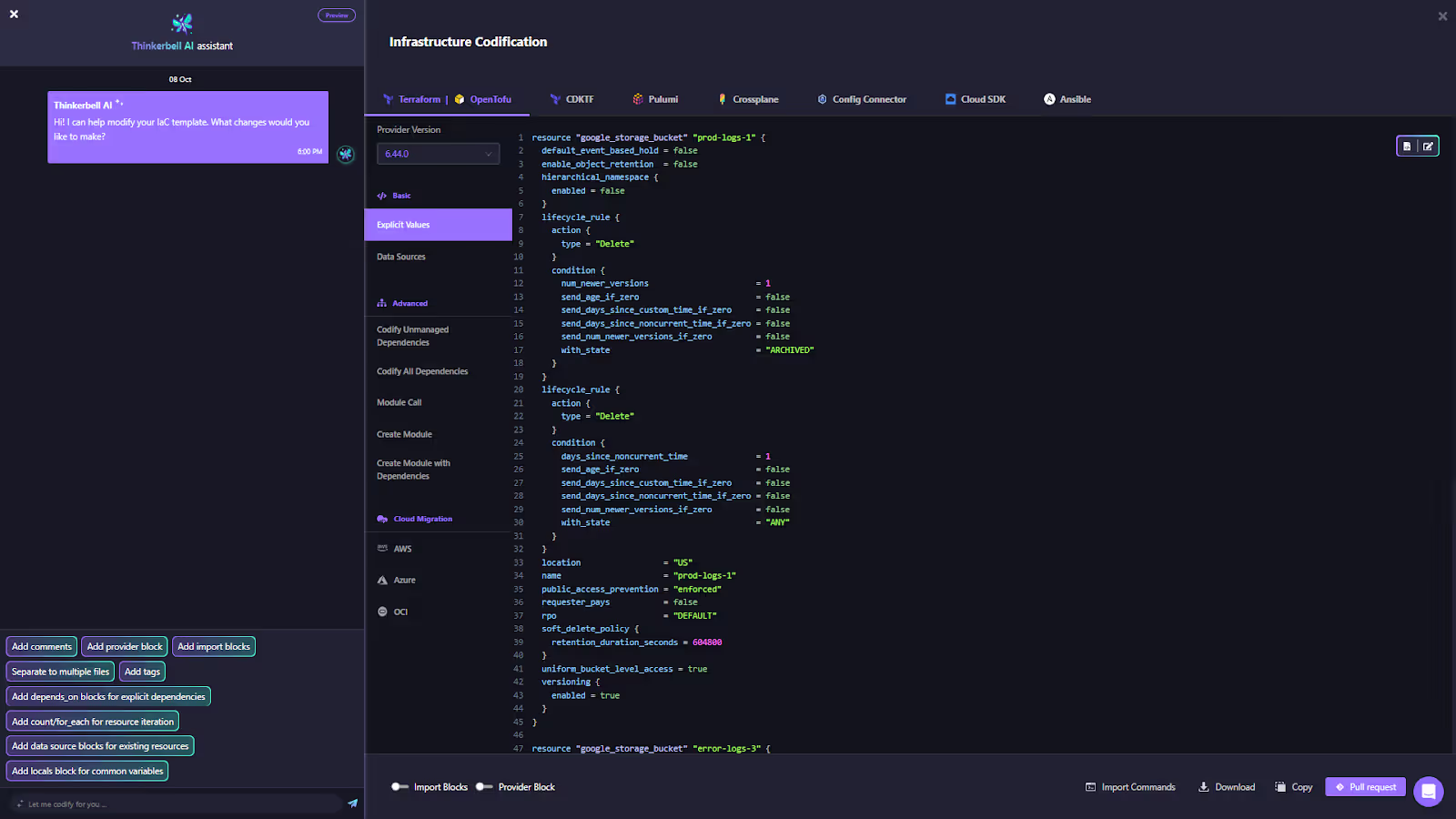
This interface allows you to codify once and migrate anywhere, maintaining parity between clouds during the transition phase.
Cross-Cloud Migration and Mapping
After codification, Firefly enables cross-cloud mapping. This means your codified AWS resources can be instantly translated into their equivalents on Azure or GCP.
For example:
- An AWS S3 bucket maps to an Azure Storage Account + Container
- An EC2 instance maps to an Azure Virtual Machine
- IAM roles map to Entra ID role assignments
S3 Bucket Ready for Migration: The updated AWS S3 codification view below displays variables such as versioning, force_destroy, and tags, ready to be translated into Azure equivalents:
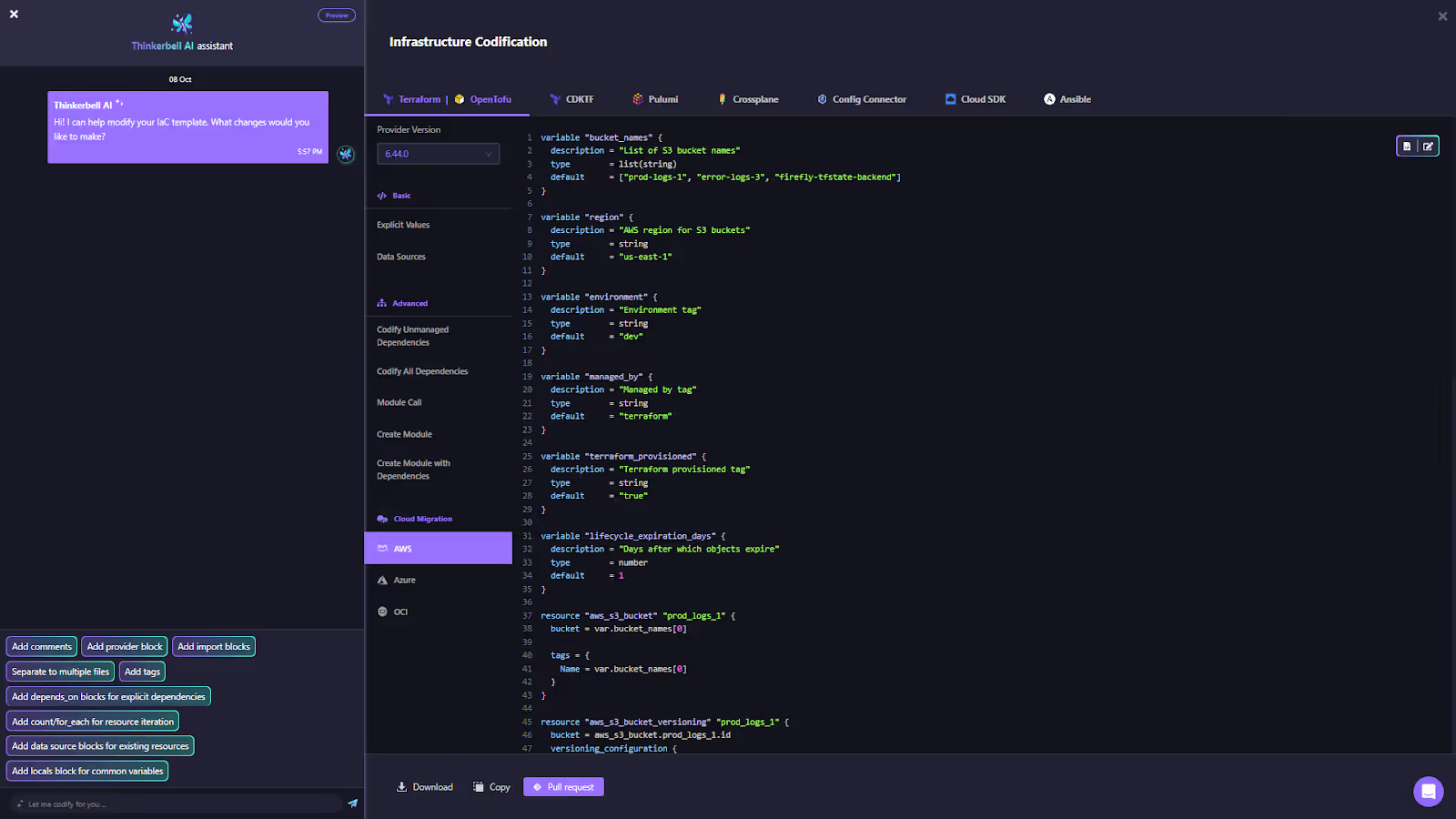
Here, Firefly created an AWS storage bucket (web-storage-6ei0tu1n13) for migration, codified with Terraform variables for region, versioning, and tagging consistency. With one click, the Cloud Migration tab lets you choose a destination provider and generate the corresponding Azure or GCP Terraform definitions automatically.
Unified IaC Across Providers
Once you’ve codified and generated the new Terraform, Firefly helps maintain a single view of truth.
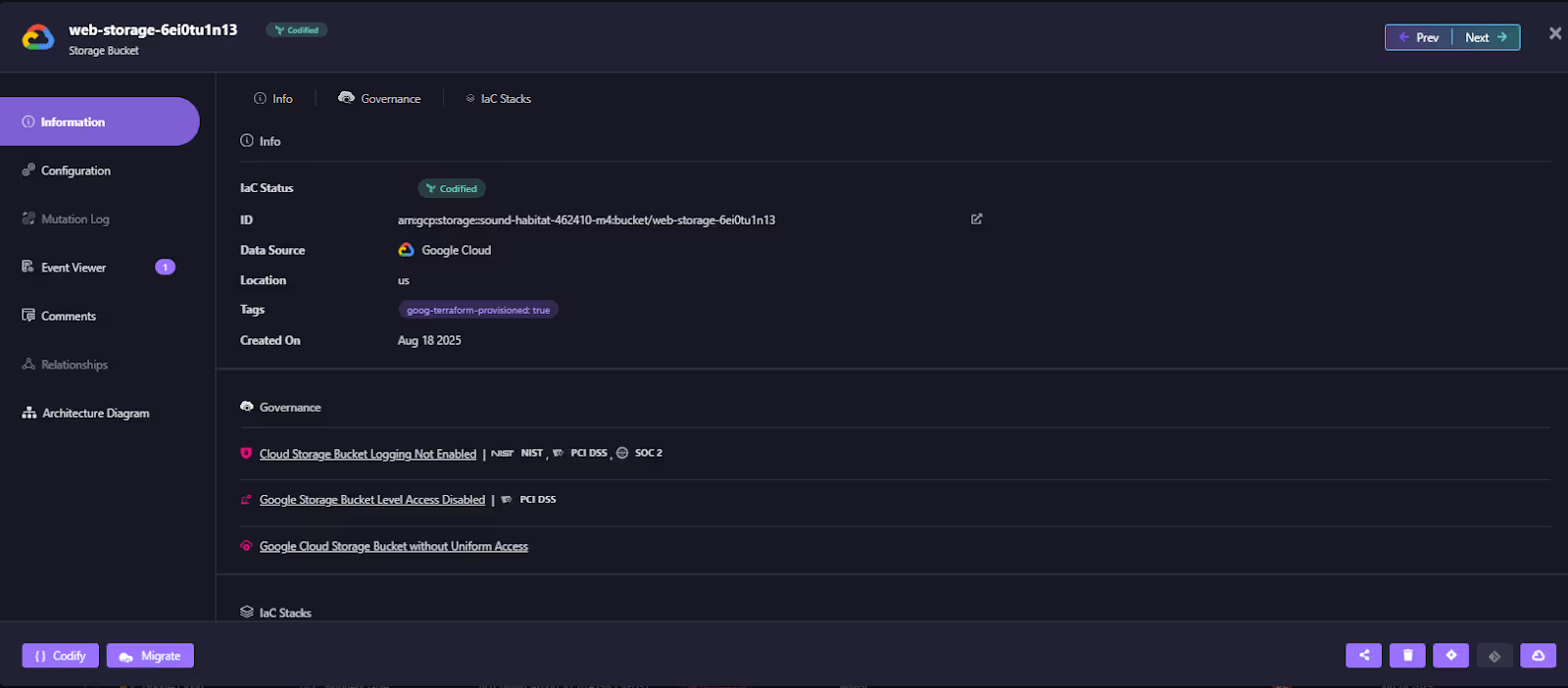
Here you can see Firefly managing IaC for AWS, Azure, and OCI using consistent variables, provider versions, and tags. This is critical for enterprises that operate in hybrid mode during transition, with workloads split across providers, but one standardized Terraform pipeline for all.
Iterate and Integrate with CI/CD
Once all your resources are codified, you integrate Firefly with your existing CI/CD pipelines. It becomes part of your automated validation loop:
- Detect drift, then auto-generate Terraform diffs, then open PRs for review
- Validate policy-as-code (OPA/Rego) during terraform plan
- Track cost and tagging coverage continuously
Firefly can push codification outputs or drift reports into GitHub, GitLab, or Bitbucket, and trigger Slack or Jira notifications for review. This transforms migration governance into a self-healing feedback system; your IaC stays continuously aligned with reality.
Firefly is the Full Solution for Enterprise Cloud Migration
While AI-powered coding assistants can indeed generate Terraform code, they don’t provide the following critical features:
- Automated discovery of live infrastructure.
- Multi-provider IaC generation that handles the differences between cloud platforms.
- Version control and GitHub PR integration to track changes and collaborate with your team.
- Drift detection and continuous monitoring to keep infrastructure consistent with code.
- Integrated compliance and policy enforcement during migration.
In short, Firefly isn’t just about generating Terraform code. It’s about ensuring that migration is done automatically, securely, and with complete governance, enabling enterprises to move large-scale workloads across clouds with confidence and compliance.
If you're looking for a simple way to generate IaC, a coding assistant might suffice. But for enterprise-level migrations, Firefly provides the comprehensive automation, governance, and compliance that ensures your migration remains consistent, auditable, and fully aligned with your organization's policies.

FAQs
What are the 5 phases of cloud migration?
The five phases are Assessment, Planning, Migration, Optimization, and Governance. You start by analyzing workloads, then plan and execute the migration, followed by optimizing performance and establishing governance for ongoing management.
What is an example of cloud migration?
A common example is migrating an on-premises CRM to AWS using services like DMS or MGN, enabling better scalability, reduced infrastructure costs, and faster feature delivery.
What is the 7-step model of migration?
The 7 Rs are: Retire, Retain, Rehost, Replatform, Repurchase, Refactor, and Relocate. These represent different strategies to modernize or move workloads to the cloud based on business goals.
What are the four steps in Google’s cloud migration methodology?
Google follows four stages: Assess, Plan, Migrate, and Optimize, using tools like Migrate to Virtual Machines and Database Migration Service to streamline workload transitions and performance tuning.