Incident response is a critical aspect of any organization's operations, and it's vital to have a well-planned and well-documented incident response playbook in place. However, traditional incident response playbooks can be time-consuming to create, difficult to maintain, and often become out-of-date quickly. That's where "playbooks-as-code" comes in - a methodology that enables you to write your incident response playbook in code.
In this blog post, we'll explore the benefits of using Terraform to build automated incident response playbooks, and provide a step-by-step guide on how to do it.
Why use playbooks-as-code for incident response?
When you manage your incident response playbooks as code, you derive similar benefits to managing infrastructure or even your software as code. Below we’ll dive into each of these areas and how this helps with cloud incident response playbooks specifically.
Version control
When managing your incident response playbooks as code, you can leverage version control for your aws incident response playbook just like any other code. This means you can use the same techniques and best practices for managing changes, reviewing and approving changes, and rolling back changes that you use for your software development projects.
This also provides you with much-needed history, so you won’t be afraid to make changes, as you can always view older versions and revert when necessary, and track who contributed to the incident response playbook, and it can serve as a resource during a real-time incident.
Infrastructure-as-code
By defining your incident response playbooks as code, alongside your infrastructure as code, you can easily share your aws incident response playbook with other teams in the same way you can share your infrastructure configurations. By defining incident response playbooks as code, you can then use them to automatically deploy and configure the infrastructure needed for cloud incident response playbooks like any other as-code resource.
Automated deployment
With Terraform, you can automate the deployment of your incident response playbook. This means you can test and deploy your automated incident response playbook quickly and efficiently, and ensure that your incident response infrastructure is always up-to-date and ready to use.
For instance, if we detect a malware outbreak, the initial step would be to block our services in order to safeguard our data. To accomplish this, we can create a dedicated IAM Policy with explicitly denied permissions for S3, DynamoDB, and RDS. This policy can be easily modified using a dedicated variable, allowing for a quick change in your aws incident response playbook.
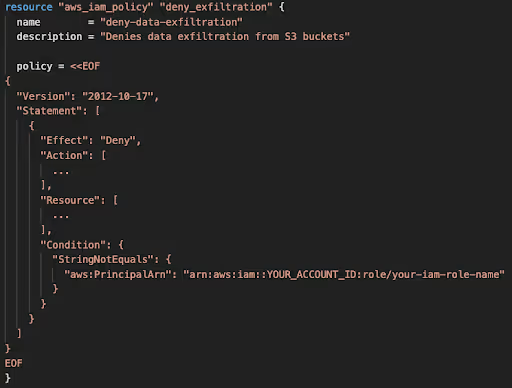
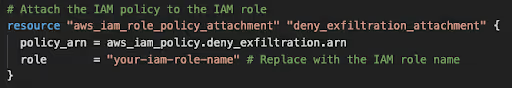
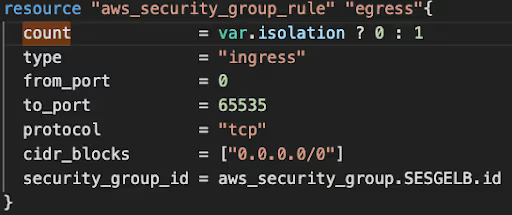
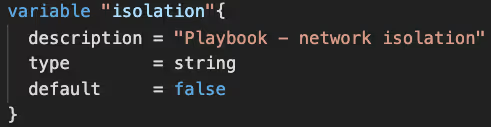
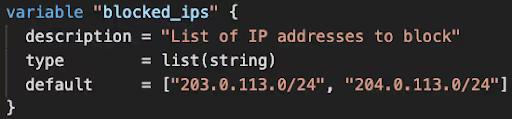
In the event of a data breach, the initial step is to isolate our network. We can achieve this by creating a dedicated variable (with a default count of 0) to block network traffic.
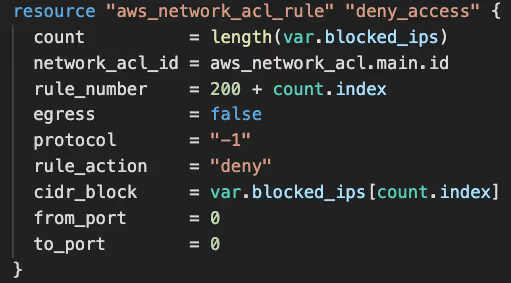
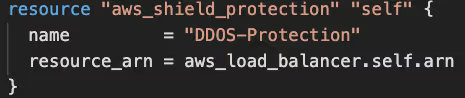
In the event of a DDoS attack, the primary action is to block the suspected IPs and configure managed DDoS protection services, such as AWS Shield Protection.
How to build incident response playbooks-as-code with Terraform
Terraform is a tool for building, changing, and versioning infrastructure safely and efficiently. It allows you to define your infrastructure as code, which means that you can use the same tools and techniques that you use for developing software to build and manage your infrastructure.
Using Terraform enables you to build incident response playbooks-as-code with all of the advantages above baked in.
Infrastructure-as-code to power incident response playbooks-as-code
The first step in building your incident response playbook-as-code with Terraform is to start by defining your Infrastructure-as-Code. This means you need to create a Terraform configuration file that describes the resources you need for incident response. There is a lot to be said about doing this - if you’re not familiar or have not done this before, you can read up about Terraform Modules here.
But just for context this means creating a Terraform configuration file that defines a set of infrastructure resources such as: EC2 instances, an S3 bucket to store logs, and an IAM role to grant access to the instances, in YAML or JSON so it’s machine-readable and automatable.
Writing your incident response playbook
Once you have defined your Infrastructure-as-Code, you are now set up with the necessary prerequisites to be able to write your incident response playbook. This should include the steps your team needs to take in response to different types of incidents.
For example, you might have a set of steps for responding to a DDoS attack, a different set of steps for responding to a data breach, and so on.
Your incident response playbook should include detailed instructions for each step, including who is responsible for each task, what tools or resources are required, and any other relevant information.
Using Terraform to automate deployment
Once you have defined your infrastructure as code and written your incident response playbook, you can use Terraform to automate the deployment of your incident response infrastructure, just like you would use it to automate any other parts of your infrastructure.
This means you can test and deploy your incident response playbook quickly and efficiently, and ensure that your incident response infrastructure is always up-to-date and ready to use.
Test and refine your incident response playbook
Finally, it's essential to test and refine your incident response playbook regularly. This means you should simulate different types of incidents and ensure that your incident response playbook works as expected. Eventually incidents are high pressure situations that require prepping for, and you should always make sure that is not the first time the team is seeing the playbook and learning how to use it.
You should also review and update your incident response playbook regularly to ensure that it remains up to date, and ready to use in a real-time incident.
Wrapping it up
Automation has brought significant value when it comes to managing the many complex services and systems we run on a daily basis. It has enabled greater scale and efficiency, and these benefits can be translated to many other aspects of our day-to-day operations through the excellent tooling that has arisen over the years to support modern engineering’s scale.
While nobody wants their systems to go down - failure always happens - and being prepared for incidents early and often is critical today, with the significant cost of an outage to the business. By automating the management and maintenance of incident playbooks, you can focus on actually preparing your teams through process and culture for managing incidents, than the mundane details of updating the text and configurations in your playbooks.
I hope you found this example useful, remember Terraform is only one tool that enables this kind of automation, and was just a way for you to understand how to practically build and automate your playbooks, but you can of course leverage your IaC of choice for this to achieve the same results.





.svg)








